Home » Cybersecurity » Application Security » Breaking Organizational Silos for Better Application Security
Breaking Organizational Silos for Better Application Security
We are all familiar with the way organizations are typically structured along functional lines, such as sales, marketing, development, etc. However, this architecture can lead to a frustrating distance between areas that have to work together to complete a program, project, or even a task.
This is especially crucial to consider with security efforts. Whether separated by functional lines, product areas, physical distance, or any other kind of barrier, it’s important to know how to get these groups on the same page.
At the Elevate 2021 conference, VP of Nomura Aruneesh Salhotra explained silo issues and how to improve security.
Who is responsible for application security?
Even if your organization has a security department, it doesn’t mean that department is wholly responsible for all aspects of security. While they may define policy, create governance, and implement tools, application security is everyone’s job. When the InfoSec department looks for opportunities to improve security, this will usually involve working with other teams such as application engineers, DBAs, and software developers to improve their practices.
But how can organizations with such different mindsets come together under the same roof? One method is to consider a foundation.
What are the key pillars of AppSec?
Imagine a temple of security built in classical Greek architecture with multiple columns holding up the roof, protecting the sacred ground from the elements. Your applications are like the sacred ground, while the roof represents your security program. These pillars are necessary to protect your applications from the outside elements, which are often extremely harsh.
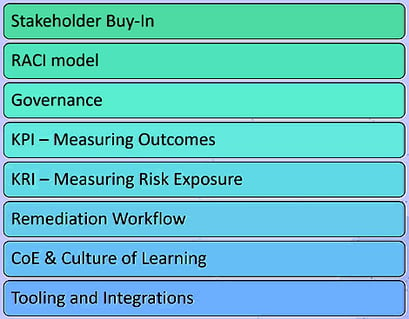 Key pillars of an AppSec program
Key pillars of an AppSec program
What are the areas of an AppSec program?
AppSec programs can be separated into the following:
-
Adoption
-
Governance
-
Training
-
Tooling
-
Integration
Each of these concerns will touch on several groups within any sizable organization, as shown in the (Read more...)
*** This is a Security Bloggers Network syndicated blog from Sonatype Blog authored by Phil Vuollet. Read the original post at: https://blog.sonatype.com/breaking-silos-for-security





