DDoS Attacks Against Financial Institutes Resurge in June 2021
According to the latest report published by Radware’s Threat Research team, Q1 of 2021 saw an increase in volume of DDoS attacks by 30%. Beyond the sheer volume, technology evolution brings new means of DDoS attacks. The attack techniques are becoming more sophisticated, and the volumes increase. For cyber attackers, no business is too big or too small.
Over the last month, there has been a wave of attacks targeting specifically financial institutes all around the globe. One of the latest victims was a global European bank that was targeted by a multi-vector attack.
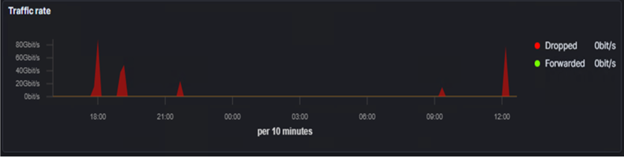
The bank, ranked as one of the top 15 banks in Europe, with over a trillion dollars in assets, has data centers all over the globe. During the second week of June 2021, it became a victim of three large bursts of traffic, which repeated persistently. This attack has reached over 200 gigabytes of volume in total (see Fig. 1)
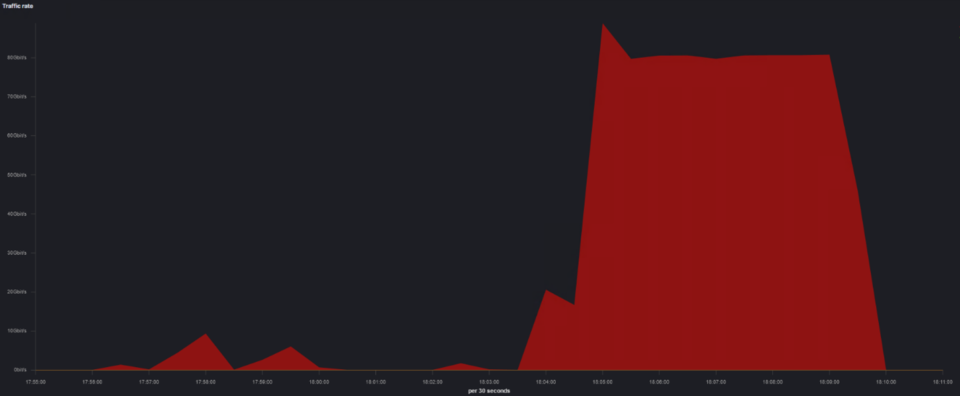
The first attack started around the evening and peaked at 80 Gbps within seconds (see Fig. 2). As the attack began, Radware’s ERT team immediately got involved to ensure complete and immediate mitigation.
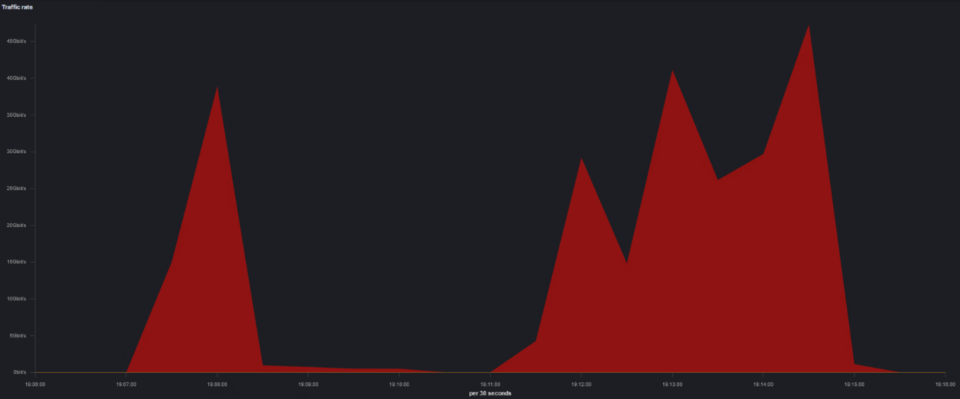
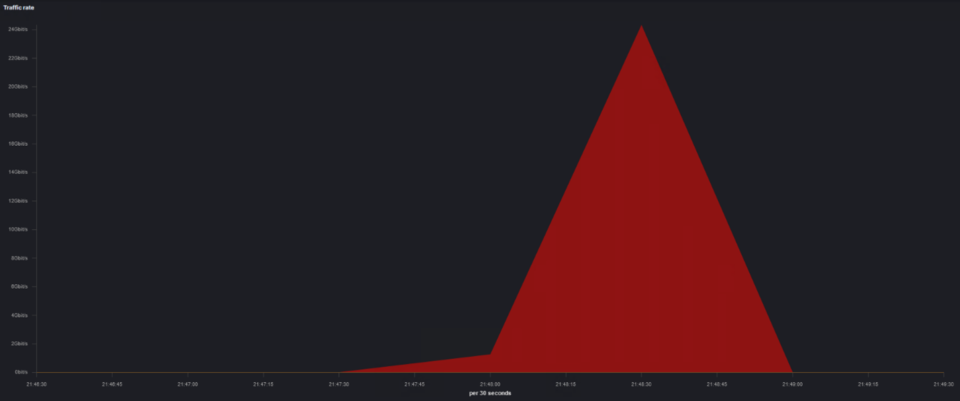
An hour later, the attackers launched the second and third attacks that followed. This wave of attacks peaked at 45 Gbps and 24 Gbps (see Fig. 3 and Fig. 4).
The Attack Vectors and the Radware Defense
All three attacks were multi-vector attacks, including the following:
- Network flood ipv4 UDP-FRAG
- Network flood ipv4 UDP
- DOSS-tcp-zero-seq
- Network flood ipv4 ICMP
- DOSS-ip-proto-oddness
- ICMP-BlackNurse-Attack
- TCP handshake violation. First packet not SYN
- DOSS-IP-GGP-Protocol-Flood
- DOSS-DNS-Ref-L4-Above-3000
- Memcached-Server-Reflected
MemCache Vulnerability
The last vector called MemCache relies on a technology called Memory Cache, a database caching system for speeding up websites and networks. When used as an attack vector, the attacker attempts to overload a targeted victim with internet traffic. The attacker spoofs requests to a vulnerable UDP memcached server, which then floods a targeted victim with internet traffic, potentially overwhelming the victim’s resources.
Memcached was used to launch the massive attack on GitHub in 2018. The fact that the servers do not have native authentication made it easier to launch amplified attacks against the victims. These servers served an internal purpose and were never meant to be exposed to the internet.
When the attack on the bank started, Radware’s behavioral detection technology immediately kicked in. It allows the analysis of the traffic and differentiates between legitimate and malicious traffic accurately. As a result, it took only seconds to generate signatures to block the attack. In parallel, all traffic containing anomalies, such as packets with invalid IP header length or port value set to zero, was automatically blocked.
All the bank’s data centers are protected by Radware’s always–on cloud services. All traffic is constantly diverted to one of Radware’s 14 scrubbing centers globally in such a setup. After the traffic is scrubbed and clean, it continues to its original destination.
[Click for Full Report: Quarterly Threat Intelligence Report]
Mitigated, As If It Never Happened
When under such types of attacks, on the bank’s side, one thing is crucial: protecting the SLA and user experience by ensuring absolutely no impact on the network.
While such a persistent and high-volume attack unfolded on the bank, no impact whatsoever was caused to the network. All legitimate users trying to access the network during the attack could do so, and no outages were reported even for one second.
How to Choose the Right Security Vendor
Last year 86% of enterprises were affected by a DDoS attack (Radware annual security report); now more than ever, there’s no room for mistakes when choosing the security technology and approach. Enterprises should make sure that the selected vendor is indeed capable of defending its network from bursts and multi-vector attacks becoming so current.
Top Three Questions to ask your vendor?
- Can the vendor ensure business continuity under attack?
- How much time into the attack will a contact from the emergency response team be available for support?
- What happens if the volume increases a certain threshold?
Organizations should make sure they are prepared now, to not find out otherwise under the worst circumstances.

Download Series 1 of Radware’s Hacker’s Almanac 2021.
*** This is a Security Bloggers Network syndicated blog from Radware Blog authored by Eva Abergel. Read the original post at: https://blog.radware.com/security/ddosattacks/2021/06/ddos-attacks-against-financial-institutes-resurge-in-june-2021/





