Azure Penetration Testing Guide – Policies, Tools & Tips
Keeping up with the trend of cloud computing, Microsoft Azure has become a popular cloud service platform. If you are here then you are curious to test whether your Azure platform is safe from cyber-attacks and security concerns. Cloud platforms always have a tradeoff between convenience and control. Even if the user is not completely in control of their cloud-based application, it is necessary to ensure that their application is protected.
Azure has a growing customer base and maintains a high standard of security. However, security is never a final state but a work in progress. With ever-changing cybersecurity scenarios and newer threats, thorough azure penetration testing is required to properly secure your application.
Azure penetration testing can be tricky since it might go against Microsoft’s security policies. Thus, with this guide, you will be able to navigate through Microsoft’s security policies and conduct pentest on your Azure application correctly.
Related: Hosting WordPress on Azure: What You Need to Know
How Microsoft’s Azure Penetration Testing Works
Before moving to pen test your application, let’s first understand how Microsoft’s Azure pen-testing procedure. Microsoft conducts Azure penetration testing based on Assume Breach procedure. In this case, the following aspects are tested:
- Intrusion and attack detection
- Rapid response to intrusions
- Recovery after data leak
- Safety against future attacks
There are two teams – Red and Blue, for Azure penetration testing. The Red team is responsible for simulating an attack on Azure platforms, without affecting customer’s data. While the Blue team is in charge of countering these attacks and recovery. Once the Blue team detects any breach, they:
- Collect all evidence regarding the incident
- Notify all operations and engineering teams
- Classify the threat to decide whether it requires further investigation
- Create a plan to alleviate the threat
- Execute the plan and recover the affected systems
After the attack, both the Blue and Red teams convene to analyze the attempt and response to the attack. Details such as the following are analyzed and discussed:
- Timing of the breach
- Mechanism of the breach
- Compromised systems and assets
- If the Blue team was able to mitigate the attack
- Whether recovery was successful and effective
Understanding Azure Deployment
The first step in Azure penetration testing is to understand how Azure is deployed on your end. Security management depends on the type of deployment. There are two types of deployment – Classis mode and Resource Management mode.
In resource management mode, you get all the cloud services bundled into a single entity. In this, you get a tool named Azure Resource Manager (ARM). As the name suggests, you can use this to better manage all your cloud services and apply security protocols in a standardized way. It also lets you apply role-based access control across all virtual resources in the group.
In classic mode, you get a bundled cloud service, containing a virtual machine, load balancer, an external IP, and a network interface card.
Azure Penetration Testing Policies
Microsoft encourages users to pen-test their Azure services and report their findings to help in fixing and patching the security gaps. However, to protect their customer’s data and to avoid disruption in their services, users need to follow some rules while pen-testing.
The following actions are prohibited by Microsoft:
- Scanning or conducting tests on other Azure customer assets
- Accessing data that is not completely self-owned
- Conducting any DDoS attacks
- Conducting any intensive network fuzzing against Azure virtual machines
- Any tests that generate a huge amount of traffic through automated testing methods
- Attempt phishing or any social engineering attacks on Microsoft’s employees
- Utilizing any services that violate the acceptable usage policies as mentioned in the online usage terms
The following steps are encouraged by Microsoft to conduct Azure penetration testing:
- Create multiple test or trial accounts to test cross-account access vulnerabilities. However, using these test accounts to access other customer’s data is prohibited.
- Running vulnerability scanning tools, port scan, or fuzz on your virtual machine.
- Testing your account by generating traffic which is expected to match regular working periods and can also include surge capacity.
- Try to break out of Azure services to access other customer assets. If any such vulnerability is found, you should inform Microsoft and cease any further tests.
- Test Microsoft Intune to ensure all restrictions function as expected.
Azure penetration testing requires you to be careful since Microsoft uses multiple automated attack mitigation services that are not disarmed for any pen-testing.
Azure Pen-testing Tools
To conduct a pen test, you will need tools that can either work automatically or can be operated manually. Below are some open-sourced tools that you can use for azure penetration testing:
1. Azucar
It’s a multi-thread plugin that automatically audits your Azure environment and collects all relevant details regarding the platform. It analyzes the collected data to detect any security concerns that might be present.
2. PowerZure
PowerZure is a PowerShell-based script that can be used for both reconnaissance and testing Azure. It has several functionalities for information collection, credential access, and data extraction.
3. MicroBurst
This is a powerful tool to thoroughly test your Azure deployment. It can be used to detect weak configuration, service discovery, and many other post-exploitation objectives.
4. CS-suite (Cloud Security Suite)
This tool lets you conduct a comprehensive cloud test on various services including Microsoft Azure.
Azure Penetration Testing Steps
Since we now know the rules and tools for Azure penetration testing, we can dive into the steps and areas which we can test.
There are three major areas for pen testing in Azure. Let’s discuss them.
1. Accessing Azure cloud services
Once Azure is deployed, the first thing to check is access management. The first place to start is the Azure web portal. Check the Azure access directory to review users who have access to your Azure services. Remove any unknown or unauthorized users from the access list. Additionally, harden the access by using multi-factor authentication for logging in.
If using other access getaways for Azure, notably PowerShell or REST APIs, check if the connection is encrypted. Also, be careful about persisting credentials across different machines. These alternate methods to access Azure can be an attractive target for attacks such as man-in-middle attacks and snooping.
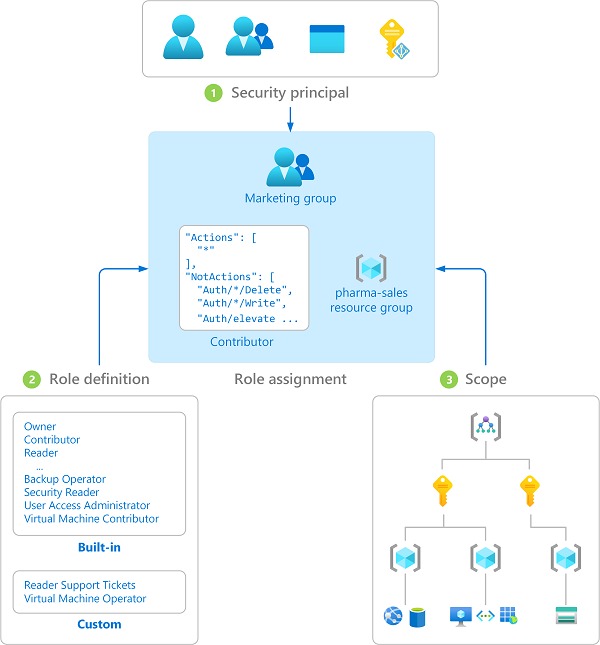
Using appropriate permissions for different user roles is a must for keeping your application safe. Azure provides three different roles, reader, contributor, and owner. The owner has the highest set of privileges, followed by contributor and reader. Make sure that the principle of least privileges applies to all users. While pen testing, you can check if any user has elevated permissions that do not match with the role.
2. Securing the database
In Azure, users store their data in MS-SQL databases, which are protected by multiple security tools by Microsoft over several layers. These tools include server and network-level firewalls, data masking, to name a few.
Regarding network-level security, ensure that both server and database-level firewalls are functioning. They can be configured by whitelisting safe IPs, as compared to blacklisting. For server-level firewalls, it controls access to a server that might host multiple databases. A database-level firewall is necessary to protect the individual database and provide fine-grained security.
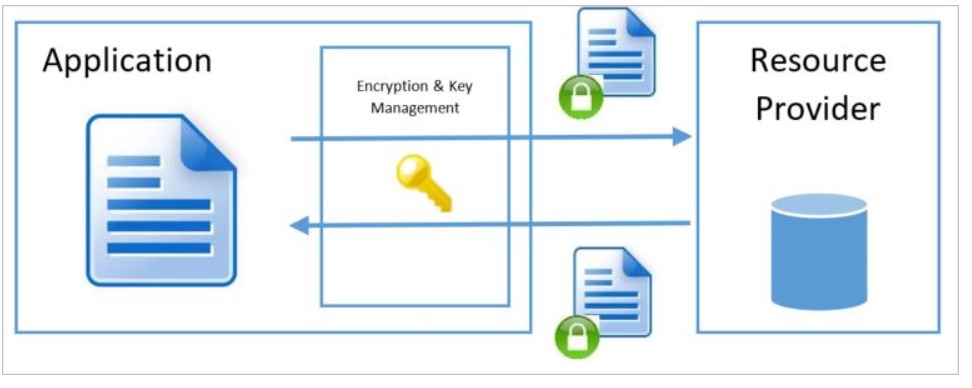
Always encrypted database engine is a powerful addition to Azure by Microsoft. This ensures that all data is encrypted in the client application before sending it to a database and the encryption key is never revealed to even database managers. This ensures that not even Microsoft administrators do not have access to sensitive data.
Data masking can also help in case complete data encryption is not possible. In azure, data masking protects sensitive data from those who o not require access to it. This can be specifically useful in scenarios such as storing financial details of customers and this can be configured by using Azure SQL Cmdlets, Portal, or REST API.
3. Encryption
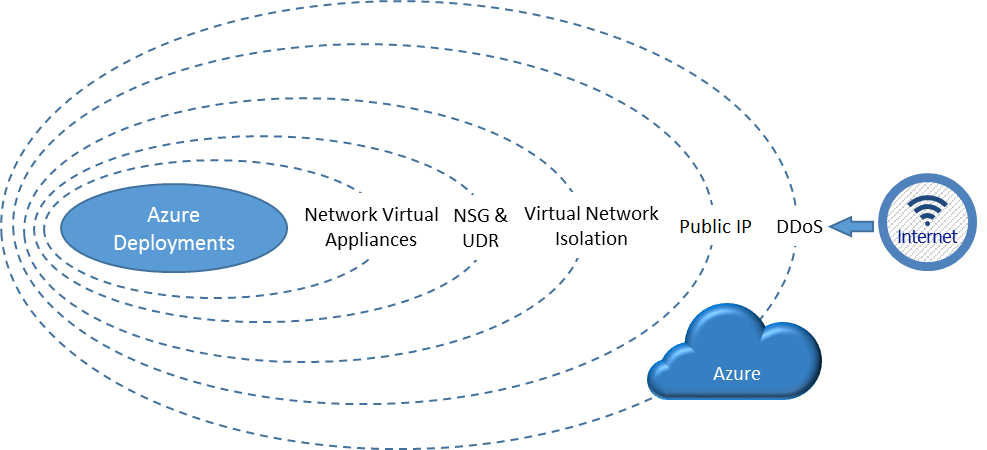
For a secure cloud platform, encryption plays a very important part. Data in the cloud needs to be encrypted both in transit and at rest.
For in-transit encryption, you can use the latest HTTPS or TLS implementation. Chances of unauthorized access from the user’s end need to be analyzed and if required, secure protocols such as VPN might also be used.
Encrypting in-rest data is a bit complicated since there are tradeoffs in every option. If you choose to encrypt all data stored in Azure, you generate an encryption key. This key can be stored either on Azure itself or on-premise. By handing over the encryption keys to Azure you get convenience and seamless integration across your Azure platform, but you’d lose control over key backup and rotation.
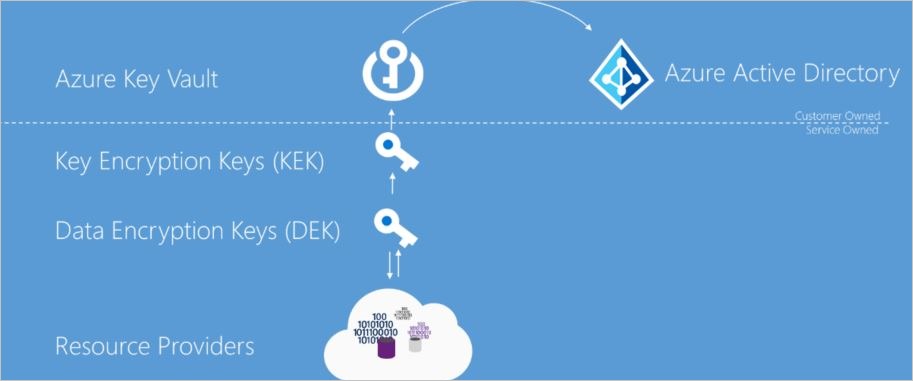
While managing your keys on-premise requires you to take complete responsibility for protecting them from attackers. By using Azure Key Vault you can control which Azure services can access it. But if attackers get their hands in this vault, they can use these keys to decrypt all sensitive data. It depends on the organization whether it is capable of managing encryption keys on-premise or allow Microsoft to be in charge of them.
Conclusion
Securing Azure means making choices in almost all aspects depending on your requirements. Azure penetration testing is not only for analyzing the security standard but also to understand what works for you. A thorough pen test will help you understand how to improve Azure security and keep your application safe. While manually it can be tricky and if proper protocols are not followed it might have some repercussions. That is why Astra offers a detailed Azure penetration testing service that makes sure all policies are followed and all aspects of the Azure application are prodded. You can check out Astra’s capabilities here.

*** This is a Security Bloggers Network syndicated blog from Astra Security Blog authored by Jinson Varghese. Read the original post at: https://www.getastra.com/blog/security-audit/azure-penetration-testing/





