How I pwned an ex-CISO and the Smashing Security Podcast
Disclaimer, this was a bit of fun with consent. But there are some worthwhile things to bear in mind.
- If you’re predictable, then criminals can take advantage of that. If someone knows what your pattern is to set passwords e.g. FacebookPassword1, TwitterPassword1, then you can easily guess what your other passwords are. Similarly, if you use the same naming convention all the time, or have a certain system you follow, if it’s know to others, it can be exploited.
- Yes, social engineering is a real thing and we need to be wary of it. Of course texting a friend and getting a response doesn’t really fall under that category. It would be a really poor world if we distrusted everyone and everything.
- Annoying security people brings so much joy to life.
For those who can’t be bothered watching the video.
Thom was recording a podcast with Graham and Carole of Smashing Security.
We guessed the URL he was using by replicating what he usually uses as a URL.

Social engineered Graham into telling us what time the recording was taking place.

We ended up gatecrashing the podcast recording.
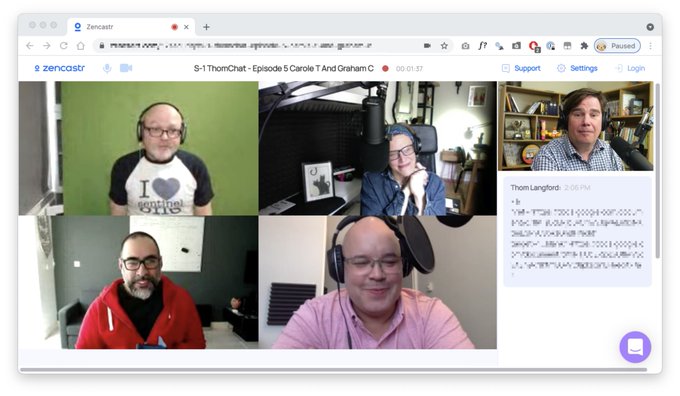
Andy and I spending the rest of the afternoon giggling like Beavis and Butthead.
*** This is a Security Bloggers Network syndicated blog from Javvad Malik authored by j4vv4d. Read the original post at: http://feedproxy.google.com/~r/J4vv4d/~3/ow874Kvd_4M/





