HackerOne Brings Hackers Into Cybersecurity Workflows
HackerOne announced today that the portfolio of tools it makes available to white hat hackers is extended now includes a video capture capability that makes it easier to demonstrate how a vulnerability might be exploited.
At the same time, the HackerOne platform is making it simpler for cybersecurity teams to directly ingest and incorporate vulnerability attestation reports with compliance forms and digest remediation guidance provided by hackers.
Finally, HackerOne has enhanced its vulnerability insights tools to provide additional context, automated workflows and packed its penetration testing and hacker challenge service into a single offering.
Michiel Prins, co-founder and head of product for HackerOne, said the new capabilities are intended to make it easier for organizations to incorporate hackers they contract to test their security posture within their workflows. Those workflows incorporate custom triggers, recommendations and pattern matching as well as bi-directional data and record synchronizations with platforms such as GitHub, Jira, ServiceNow, Gitlab and Microsoft Azure DevOps.
HackerOne reported a 63% increase in the number of hackers submitting vulnerabilities over the past 12 months, with 38% of the hackers that make their services available via the platform noting they have spent more time hacking since the start of the pandemic. More a third (34%) of hackers said they have seen more bugs as a result of pandemic-led digital transformation initiatives.
Cybersecurity teams appear to appreciate the extra help. Half of the HackerOne hackers (50%) reported attitudes towards hackers are becoming more positive in the wake of the pandemic, with (34%) reporting they have earned more bounties.
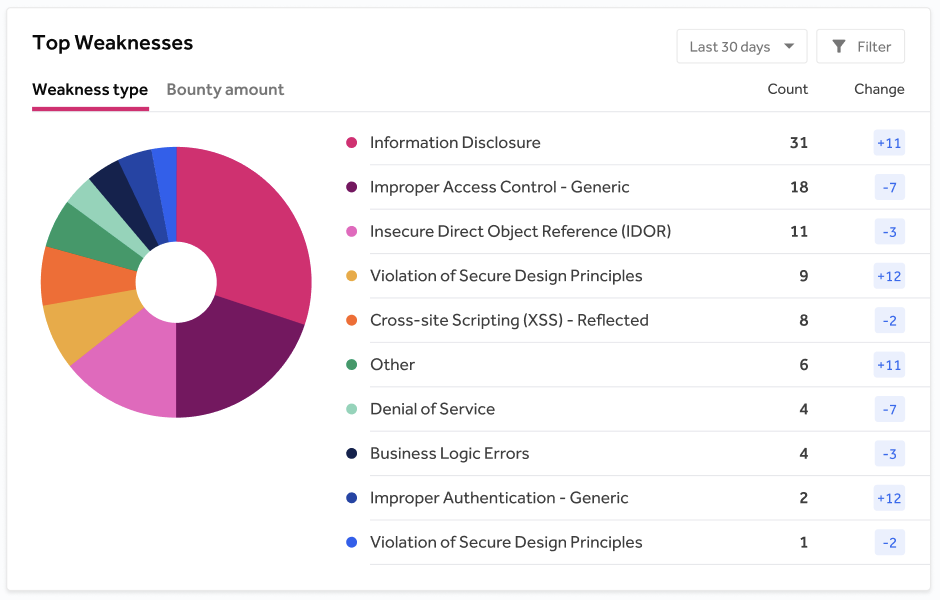
Prins noted that much of the testing hackers are being asked to evaluate involves cloud services. In fact, HackerOne has seen a 310% increase in reports involving cloud misconfiguration on the HackerOne platform. Misconfigurations are plaguing cloud security mainly because developers now routinely employ tools such as Terraform to provision cloud infrastructure.
Unfortunately, many of those developers lack an appreciation for what it takes to properly configure those services, which results in, for example, ports being left open. Cybercriminals now regularly make use of tools that scan for those misconfigurations because they know organizations are not likely to restrict usage of infrastructure-as-code (IaC) tools such as Terraform, noted Prins.
At a time when most organizations are finding it difficult to hire and retain cybersecurity expertise, Prins said a small army of freelance hackers provides a way to augment cybersecurity teams, which are typically understaffed and overworked. The hackers also provide an ‘outside-in’ perspective that cybersecurity teams, especially those that don’t have much hands-on hacking experience, usually lack.
Of course, not every one is entirely comfortable with the idea of paying individuals with a talent for hacking to compromise their IT environments. However, everyone in IT knows that black hat hackers are already probing for weaknesses across what has often become an incredibly extended enterprise in the wake of the COVID-19 pandemic. The race is on to discover as many vulnerabilities in those environments as possible, before some bad actor figures out how to exploit them.