Home » Security Bloggers Network » 9 Elements Required for an Effective Third Party Risk Management Framework
9 Elements Required for an Effective Third Party Risk Management Framework
The increasing reliance on third-party vendors has opened a set of risks that requires a new approach to implementing efficient Third-Party Risk Management (TPRM).
Third-party vendors such as payment gateways, web plugins, email servers, and countless others typically work with multiple companies at a time. Consequently preventing the next supply-chain attack before the vendor’s exploit is disclosed requires taking vendor-specific steps.
The recent IBM-sponsored Ponemon Institute Data Breach Report indicates that when a third party causes a data breach as opposed to another source, the cost is more than $370,000 higher, for an adjusted average total cost of $4.29 million, with an average cost per user of $150.
This rise in supply-chain attacks has prompted regulators to include stringent cybersecurity clauses in an ever-growing number of regulations. If the rising tide of fines for non-compliance is indicative of a trend across the regulatory landscape, compliance with existing, new, and upcoming regulations is imperative.
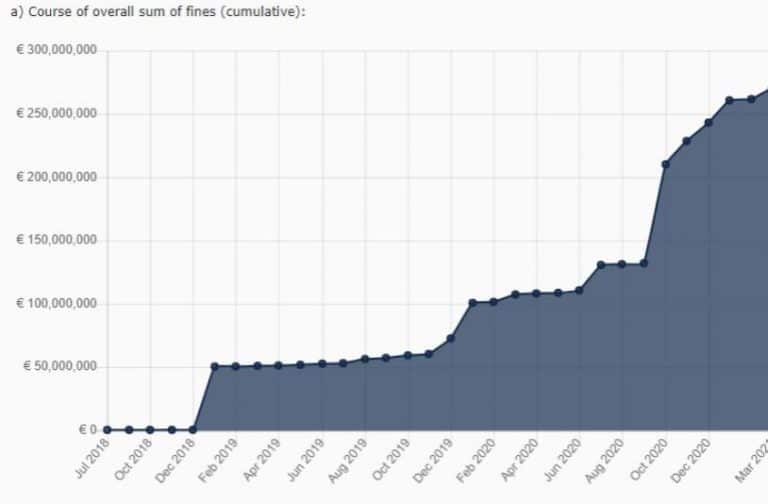
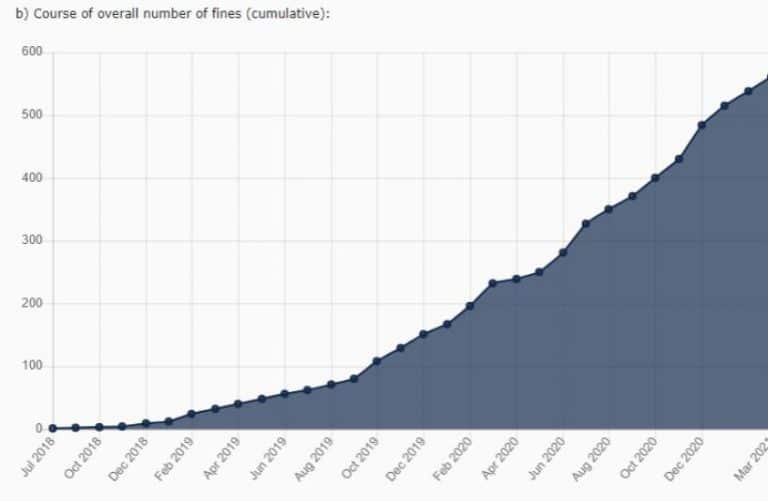
Current regulations already include GDPR, CCPA, SAFE DATA ACT, U.S. Consumer Data Protection Act, Filter Bubble Transparency Act, HIPPA, and many others in the US, PIPEDA in Canada, NDB in Australia, APPI in Japan, LGPD in Brazil, PDPA in Singapore and Thailand, PDPB in India and many more.
Implementing an effective third-party risk management strategy today is fundamental to insulating a company from financial, operational, legal, and reputational risks.
What Makes an Effective Third Party Risk Management Solution?
Applying the 3Ps of TPRM – Purpose, Perseverance, and Planning- brings together specific security skillsets and routine workload.
-
Purpose – Even if compliance regulations are becoming more encompassing, ticking the compliance box does not constitute a third-party risk management strategy. The defining goal of Third Party Risk ManagementPM needs to be the prevention of attacks.
-
Persistence – Third Party Risk Management is an ongoing endeavor, requiring continuous monitoring and recalibration.
-
Planning – Third Party Risk Management cannot be an afterthought. It needs to be planned meticulously and include contingency plans.
For more information on the 3p’s get in touch
Below are a few key points that need to be taken into consideration to minimize risks emanating from supply chain attacks:
-
Exhaustive list of all third-party vendors, including fourth, fifth, and nth party vendors
Insufficient business and suppliers’ context is an endemic issue in organizations. The first step of efficient third-party risk management is to ensure exhaustive visibility of your supply chain, including fourth parties. This implies knowing who they are, what segments of your system they interact with, what providers they subcontract, and so forth.
Assessing the risk posed by third-party vendors implies covering various aspects, ranging from contract, legal, and compliance risks to process and operational risks.
-
Comprehensive inclusion of all departments
Third Party Vendor Risk Management’s proper governance and processes requires staffing and funding. Obtaining the input of all concerned departments, not only compliance and IT but also operational risk, procurement, financial, and HR, is a crucial step to securing and allocating funds and defining a comprehensive implementation and monitoring schedule.
-
Experience –
As the recent Solarwind attack demonstrates, nation-state grade attacks are now being used to target and attack private organizations.
This means that, to prioritize defense, you need to think like a nation-state attacker and focus on exhausting the attackers to either discourage them or to gain insights in their tactics before they bear fruits and improve deflecting tactics.
Unfortunately, there is no plug and play solution that can provide the experience needed to take pre-emptive action. It requires switching to an Offensive Framework Methodology (OFM), that combines assessing risks, simulating attacks, establishing a cyber defense strategic plan and ongoing monitoring and updating.
-
Adequate staff resourcing
Planning for balanced staff resourcing should factor in the specific domains of specialization required to cover all supply chain aspects. It should consider that the human factor is still crucial in identifying potential threats, implementing contingency plans, and updating the system to meet new business or regulatory requirements.
-
Regulatory adaptability
As lawmakers are increasingly concerned by cyber risks, including those stemming from the supply chain, at any time, a regulatory change might require modifying the Third Party Risk Management measures in place.
Keeping up with the evolving legal landscape implies staying updated about planned new regulations for all relevant geographical areas and plans to upgrade your TPRM flow before the new regulations are enforced.
Get in touch for help staying compliant
-
Exhaustive Documentation
Without keeping track of all interactions with every vendor, some might fall through the cracks. Missing vendor-related data can have catastrophic consequences at operational, financial, and legal levels when a breach occurs.
-
Contingency plans
There are two situations that might require drastic action in a short time.
-
A vendor’s security, compliance, or operational score might fall below the minimum acceptable and have to be replaced.
-
A breach occurs.
A pre-established contingency plan prevents costly operational flaws, business losses, and more.
-
Continuous performance evaluation
Falling asleep at the infosec helm might sink your company. Continuous monitoring of staff performance, including quarterly evaluations, ensures quality consistency.
Similarly, monitoring the Third Party Vendor Risk Management strategy’s efficiency and fine-tuning it to reflect real-time challenges and emerging threats prevents risks unidentified in the initial planning stage.
-
Plans for the future
Vetting vendors is a time-consuming process that requires conducting third-party screening and complete due diligence, and after they are approved, onboarding them.
The time to start the vetting process is not limited to when your company is considering adding new services. A projected marked increase in activity should automatically trigger a verification process of all existing and contingency vendors to verify they have the operational ability to handle the growth.
Being proactive in setting up comprehensive Third Party Risk Management policies is fast becoming imperative.
Contact HolistiCyber for information about our third-party risk management solutions.
The post 9 Elements Required for an Effective Third Party Risk Management Framework appeared first on HolistiCyber.
*** This is a Security Bloggers Network syndicated blog from HolistiCyber authored by marketing envy. Read the original post at: https://holisticyber.com/blog/9-elements-required-for-an-effective-third-party-risk-management-framework/





