Your First SOAR Use Case: Phishing Triage
Phishing continues to be a dangerously effective attack method. Roughly 91% of successful attacks start with phishing. On average, 30% of the phishing emails sent get opened and viewed. Considering the minuscule cost and effort involved in creating and sending an email, it is no wonder this method continues to be so popular for attackers. And it’s becoming increasingly difficult to spot a phishing attempt. Attackers sending phishing emails can expect between 10% and 15% of the time that the malicious attachment or link will be accessed in some companies.
Without phishing automation, an analyst must manually receive a potentially malicious email through some system of detection or by notification from a user. The analyst must then inspect the email and manually extract details to validate them. This means looking at every part of the email in detail (headers, body, everything) and identifying anything that could potentially be an indicator of compromise (IOC). To determine the IOC’s risk, analysts must then access various threat intelligence and enrichment sources. This usually requires copying and pasting information into additional windows or browser tabs to investigate the IOCs and determine their risk. These steps are tedious, time consuming, monotonous, repetitive and easily messed up. Executing the response and any remediation actions adds even more steps and more time to the whole task of handling a single potential phishing message.
An excellent way to combat this problem is to make your existing tools and staff significantly more effective. Automating phishing triage with security orchestration, automation and response (SOAR) is the way to eliminate most, and in some cases all, of the manual tasks. Additionally, SOAR provides a way to handle every event and all the supporting steps at machine speed. Using Swimlane as your SOAR platform, you can ingest and parse emails, perform the threat intelligence lookups and handle the response and remediation means these steps are executed at speeds well beyond human capability. The steps are also guaranteed to be performed by the book, your playbook. Swimlane does not miss a step or accidentally make a mistake, so the accuracy exceeds human capability as well. Most importantly, SOAR handles the tedious, monotonous, repetitive tasks that quickly burnout and overwhelm analysts. This means analysts are freed up to contribute value to more important human tasks like research, threat hunting and expert evaluation of questionable events. The diagram below shows an overall view of one way phishing triage can be accomplished with Swimlane.
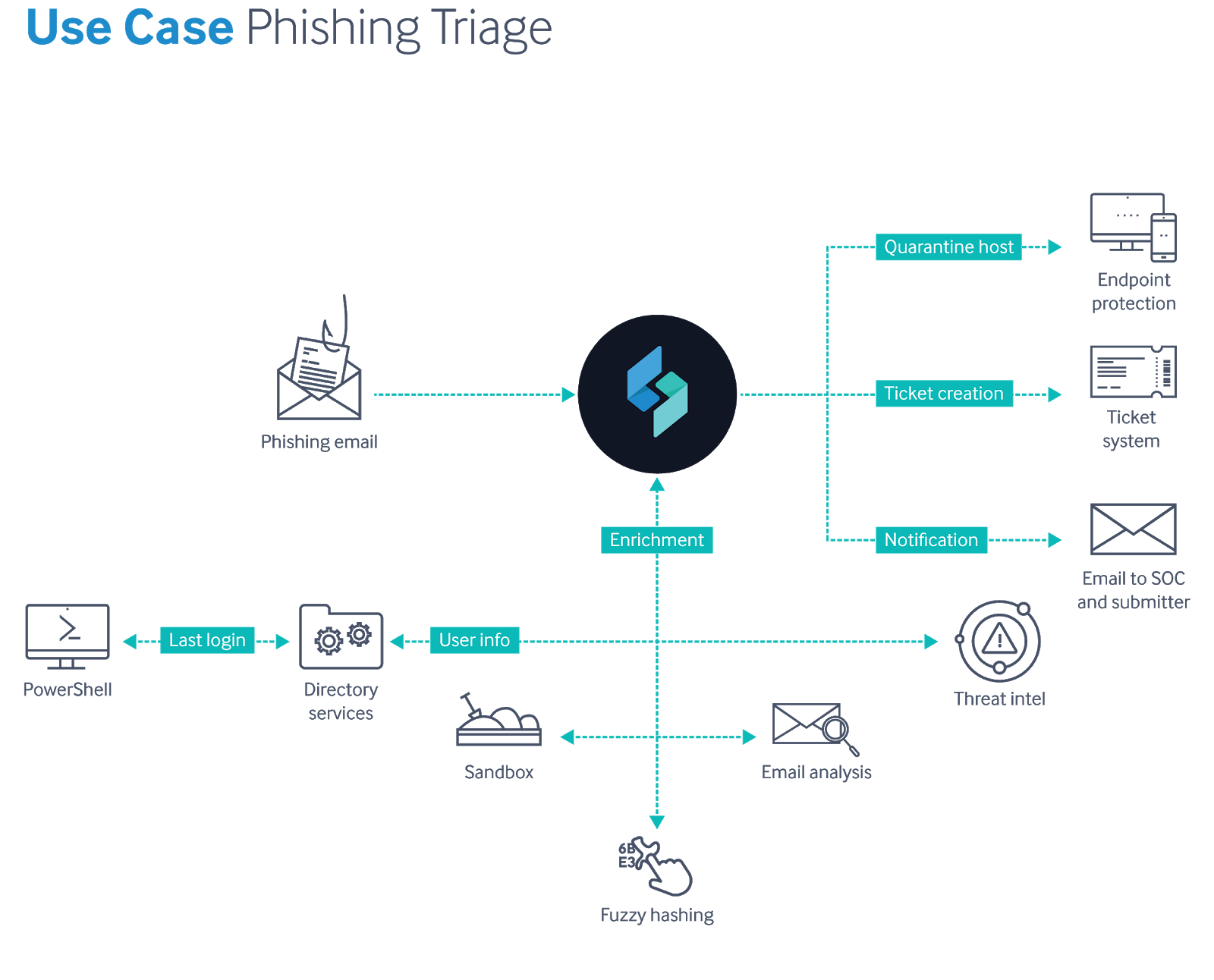
This phishing incident workflow starts with Swimlane ingesting an email from a monitored organization mailbox where users send suspected spam and phishing emails. When any email arrives, it is automatically ingested and parsed. Details like the header, subject, body, and email addresses are placed into data fields in a newly created case record. Potential IOCs like IP addresses, URLs and domains are also parsed into the appropriate fields. As the IOCs are identified by the workflow, integrations with other tools are automatically engaged to enrich the data and determine the associated level of risk. The phishing workflow also uses integrations to verify user details and, if desired, add additional user information to the record. Attachments or URLs found in the email are deployed using a sandbox resource and evaluated. This workflow also employs fuzzy hashing to match data to other known events.
The data returned from the various tools and resources is immediately added to the record. The workflow uses the combined information in the record to determine an overall risk score and whether the phishing email should be considered malicious, suspicious or benign. If the overall risk is severe and indicates the email is malicious, the workflow executes the designated response and/or remediation. In this example that includes steps like automatically quarantining the endpoint using the EDR tool, automatically generating and assigning an IT ticket to have the system restored to a non-infected state and a notification to the SOC and the user letting them know about the situation.
Swimlane also enables the automation of additional proactive tasks like threat hunting. When a malicious email is found, the SOAR solution can immediately search all the organization’s mailboxes and identify any other mailboxes where that malicious indicators are present. Depending on the desired level of automation, those additional emails can be automatically deleted or automatically presented to an analyst with a single click option for the chosen action. Automating phishing alert triage is just one use case example of what SOAR can do for your organization. Dive in with us to learn more!
*** This is a Security Bloggers Network syndicated blog from Swimlane (en-US) authored by Jay Spann. Read the original post at: https://www.swimlane.com/blog/your-first-soar-use-case-phishing-triage/





