Why Small and Medium-Sized Professional Service Firms Are a Big Target for Ransomware Attacks
If you focus only on the headlines, even in the specialist tech press, you’d be forgiven for thinking that ransomware attacks were mainly a problem for larger businesses and institutions. Those incidents which make the news tend to feature attention-grabbing numbers. These can be either in the size of ransoms demanded or the costs of restoration and recovery. Another type of attack that will always get in the news, would be related to vital services – the hospitals, schools, police departments, or other government services – whose disruption is likely to cause widespread concern. When a major bank, tech firm, logistics or telecoms provider, or well-known institution is knocked offline for days at a time, it tends to make the news.
At the other end of the scale are the individuals, and perhaps micro-businesses, hit by entirely automated malware infections. In these cases, mostly ultimately traceable to a spam email, or malicious advertisement in a video game, someone’s personal PC or laptop has been locked up and cherished photos, a draft of a novel or list of local customers is leveraged to extort a few hundred dollars in Bitcoin.
For much of the history of the ransomware threat, these have been the bulk of the victims, and the topic of most of the scare stories, at least until the rise of cloud services and automated duplication of data across devices gave us all an easy way to back up our data. But in between these two, there is another group which gets far less attention than it should – small to medium-sized businesses, many of them providing professional services such as legal or financial advice. Small businesses are the largest employer in the US, and make up the foundation of the US economy. The impact prevalence of ransomware on this industry segment stands out from other industries.
Ransomware Stats for Small and Medium-Sized Businesses
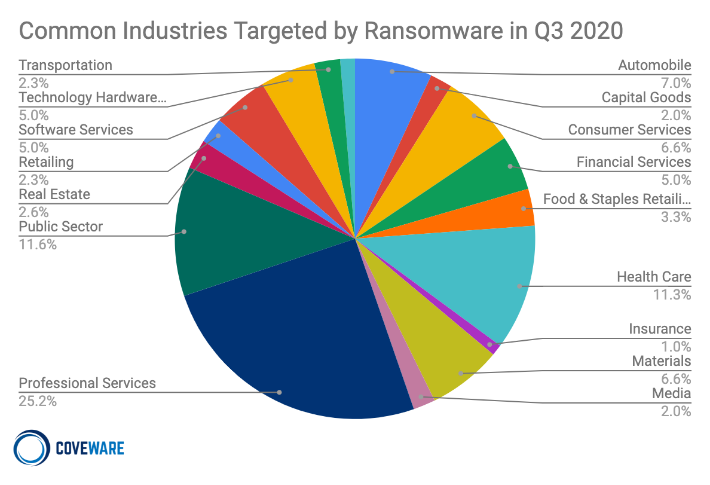
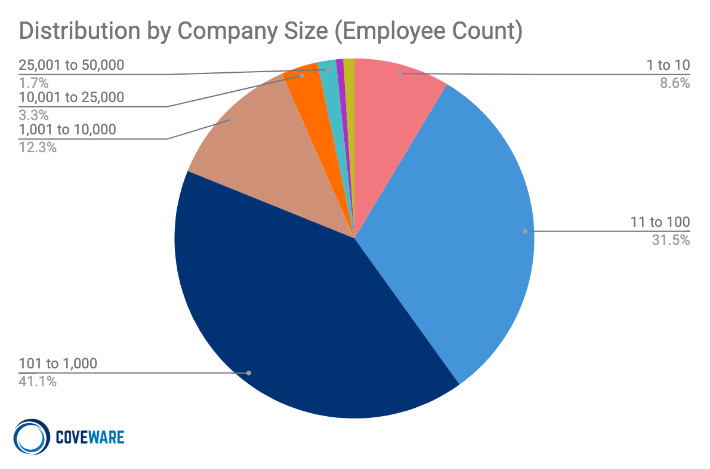
Coveware’s latest set of statistics from Q3 of 2020 show that more than 70% of ransomware incidents were companies with fewer than 1,000 employees, and 60% had revenues of less than $50 million. Looking at the breakdown by industry sector, more than a quarter of companies are in the professional services category, by far the largest single vertical and challenged only by health care and the public sector. As noted above, these get perhaps more attention than they should, weighing in at only 11.3% and 11.6% of incidents. No other category tops 10%.
With professional services firms making up only 14% of businesses in the US, but making up over 25% of ransomware attacks, this industry sector is absorbing more attacks than it should.
Why Are Small Professional Service Firms a Target?
When we think about why these small and medium-sized law firms and accounting operations are so often targeted, there are some obvious reasons. Companies with a few dozen or even a few hundred staff tend not to have dedicated IT teams implementing best practices and operating sophisticated security tools. They may only have a couple of techs, or a break-fix MSP keeping everything going, or outsource to a part-time service provider.
They’re more likely to have flat network structures and simple access control policies, focusing more on making sure everyone has access to what they need than ensuring no-one has access to things they shouldn’t. Their backups may be patchy, poorly tested, or even non-existent. Most problematic, is they’re seeing the same headlines as the rest of us, they’re probably not thinking of themselves as a prime target for ransomware, and so not taking the steps needed to keep themselves safe. Believe you are too small to be a target can be a damaging mistake. Every computer connected to the internet is a potential target, and small service firms have tendency to present cheap, easily discoverable vulnerabilities to the internet. These vulnerabilities make them a cheap target. With ransomware, economics matter and threat actors will focus on softer targets.
The Economics of Ransomware Attacks
Like other forms of financially motivated crime, cyber extortion is driven by the power laws of basic economics. Legitimate goods have a cost to produce, a cost to sell, and an end amount of profit earned from sales. Illegitimate “services” like extortion are no different. A ransomware attack costs money to stage and execute. Just like a legitimate firm, the average attack has a success rate and monetization rate that threat actors can expect as their profit. Rational economic behavior predicts that a financially motivated actor will seek to maximize profits (costs less proceeds). Attacks on larger, better-defended targets are more difficult to pull off. They take more time and expertise to set up, sometimes even involving expensive zero-day exploits which can only reliably be used once.
They can also take more time and effort to complete, with negotiations stretching for days or weeks, and throughout there is a higher risk of failure, of an attack being spotted and blocked, of a surprise system change undoing the attacker’s hard work, or of a victim simply refusing to pay up. The very high ransoms demanded reflect both the effort and the risk.
Increased Ransomware Vulnerability of Small and Medium-Sized Businesses
Smaller firms present a sweet spot on the curve for ransomware attackers, able and often willing to pay out at reasonably high rates but with much less effort and risk. Attacks on less well-protected networks require less expertise and investment, and a large part of that is down to the availability of large quantities of very cheap Remote Desktop Protocol (RDP) credentials. The market for stolen RDP credentials, often obtained from previous breaches and leaks, has grown so rapidly that supply outstrips demand, bringing prices as low as $100 for a small enterprise. With RDP access to a simple and under-secured network, pulling off an extortion sting can be the work of a few hours for a reasonably savvy operator, rather than the days or weeks of expert time needed to infiltrate, navigate, and compromise a more sophisticated business.
With their limited attention to IT security, small pro service firms routinely fall into this low-hanging fruit category, putting them firmly in the sights of the extortionists.
What Can Small Professional Service Firms do to Protect Their Data From Ransomware?
RDP compromise has long been the prime vector for ransomware, staying above 50% of all cases for at least the last two years. The good news is that it is fairly simple, and inexpensive, to secure. Of course, investing in a corporate VPN, next-gen firewall and end-point detection & response systems (and well-trained people to operate them) should make things even safer, but the first steps are much less resource-intensive. Those first steps include changing port numbers away from defaults to be less visible, imposing lockout provisions to block brute-force attacks, and applying a simple IP whitelist to limit attack sources.
Implementing proper least-privilege access control is a basic best practice and will help here too, ensuring only those users who really need elevated access can get it. 2-factor authentication should be in place on top of any username-password system, and is especially vital for anyone with admin rights, so requiring it only at higher levels will at least minimize escalation of privileges. For more details on securing RDP, see our full article on the topic. If you’re in charge of IT for a small-to-mid-sized professional service firm there’s a high chance you could become a victim – a few basic protections could be all that’s needed to move you out of that low-hanging-fruit category, and keep you, your data, and indeed your income safe.
*** This is a Security Bloggers Network syndicated blog from Blog | Latest Ransomware News and Trends | Coveware authored by Bill Siegel. Read the original post at: https://www.coveware.com/blog/2020/11/30/why-small-professional-service-firms-are-ransomware-targets





