How to Detect and Respond to SS7 Attacks — OT Telco Use Cases
In the telecom environment, using Signaling System No.7 (SS7) protocol is very crucial, especially in 2G networks. If you’re wondering how SS7 works, SS7 protocol is an international telecommunications standard used to set up public switched telephone network (PSTN) and one of the services that it offers is for Short Message Service (SMS). A common concern is that attackers try to exploit security vulnerabilities in the SS7 protocol which compromises voice and SMS communications.
To detect an SS7 attack, Positive Technologies developed a solution called Telecom Attack Discovery (TAD). Due to the nature and extent of an attack, which can cross from information technology (IT) to operational technology (OT), LogRhythm has implemented TAD into our security solutions to help combat SS7 attacks.
How to Detect and Respond to an SS7 Network Attack with LogRhythm’s TAD Integration
Here are four of the most common SS7 vulnerabilities customers and telecommunications organizations can detect using LogRhythm’s integration with TAD.
1. Detect Prohibited Interconnect Packets
Attackers can exploit messages received from interconnected links from other networks, without any explicit agreement to do so. Here are examples of what damages this type of SS7 attack can cause:
Denial of Service (DoS)
- Disruption of network nodes operation
- Disruption of phone subscription services
Fraud
- Illegal use of network resources or services
- Money transfer from subscriber’s account
- Call redirection
- Modification of subscriber’s profile
Data leakage
- Disclosure, interception, or theft of subscriber information such as location, text messages, and conversations
- Access to network configuration details
For all of these examples, LogRhythm has automated alert and alarm capabilities using Risk-Based Priority (RBP) in order to detect these types of attacks and notifications are sent to the appropriate user or groups.
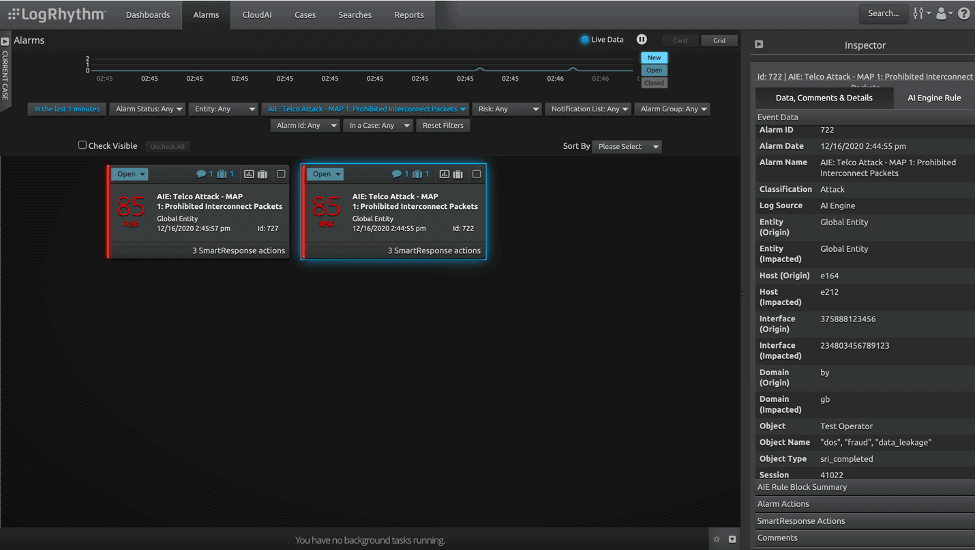
Figure 1: How to detect prohibited interconnect packets with LogRhythm
2. Detect Packets from an Unauthorized Network Requiring an Answer
This attack exploits messages which should mainly be received in relation to an inbound roaming (visiting) subscriber from that subscriber’s home network and require an answer. The impact of this attack is data leakage.
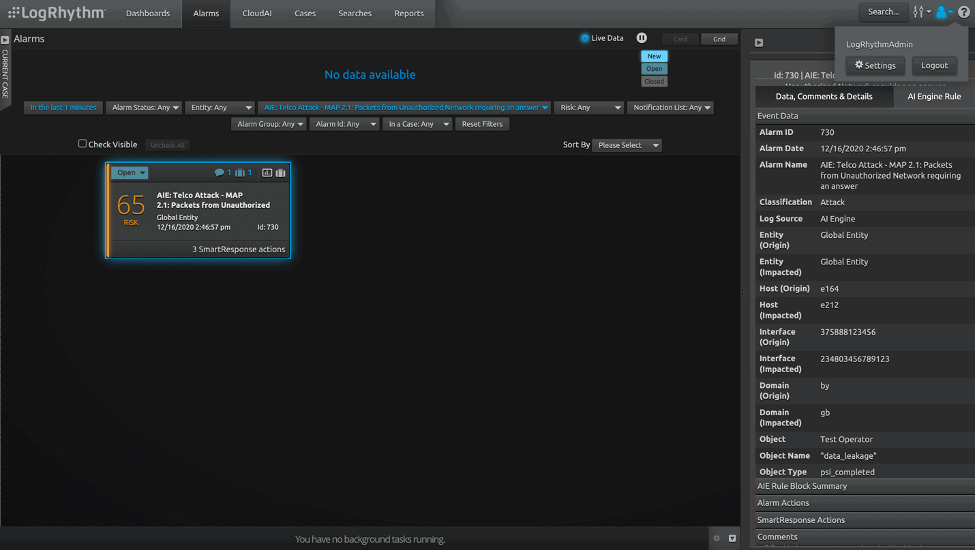
Figure 2: Detect packets from unauthorized network requiring an answer
3. Detect Suspicious Location Packets
This SS7 attack exploits messages related to a roaming subscriber activity (other than subscriber registration) from the visited network that the subscriber is currently roaming in. The calling signaling connection control part (SCCP) address of such messages should normally match the current visitor location register (VLR) address. The impact of this attack is data leakage.
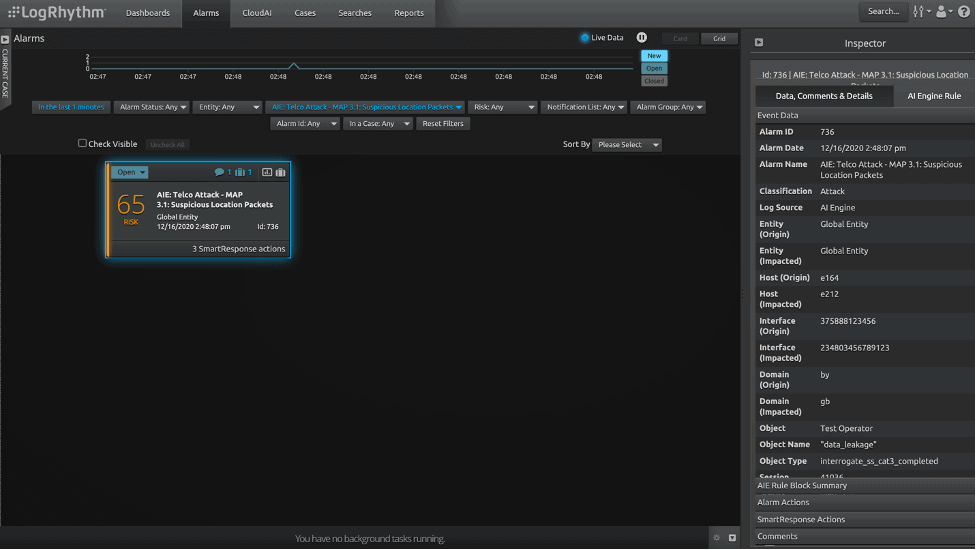
Figure 3: Detect suspicious location packets
4. Detect Suspicious Registration Attempts
This attack exploits messages directly involved in subscriber registration such as UL and serving area interface (SAI). These should normally be received only in relation to a roaming subscriber from the visited network that the subscriber is currently roaming in. Impact of this attack is DoS and fraud.
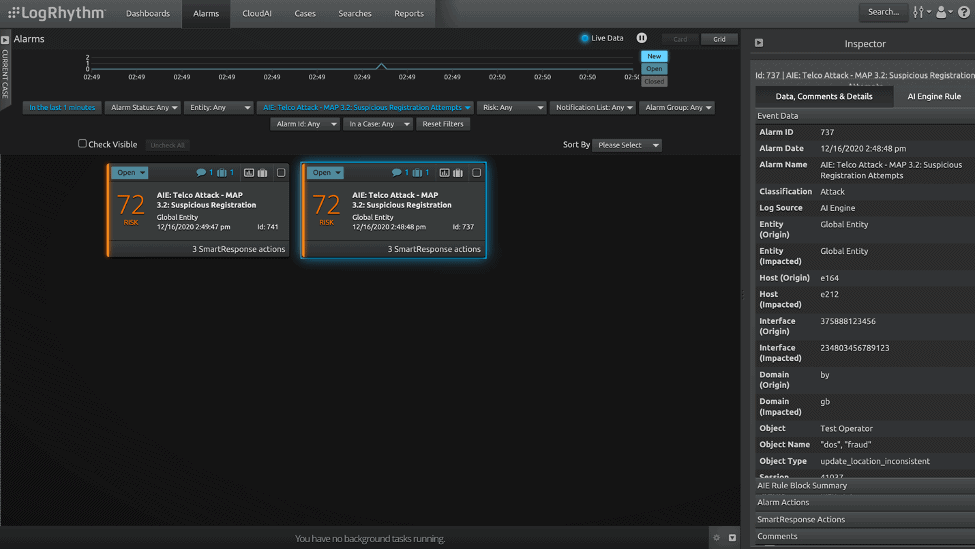
Figure 4: Detect suspicious registration attempts
Identify and Respond to an SS7 Attack in the Telco Environment
Providing 24×7 monitoring is another important step to detecting an SS7 attack in the telco environment. LogRhythm’s Event Dashboard and Analyze Dashboard layouts both leverage the same building blocks (widgets) to deliver use cases that help analysts identify and investigate activity. LogRhythm provides a Telco Security Dashboard which accumulates all the information from TAD and projects it in live form. This way customers can easily be able to monitor any abnormality triggered in their OT telco environment.
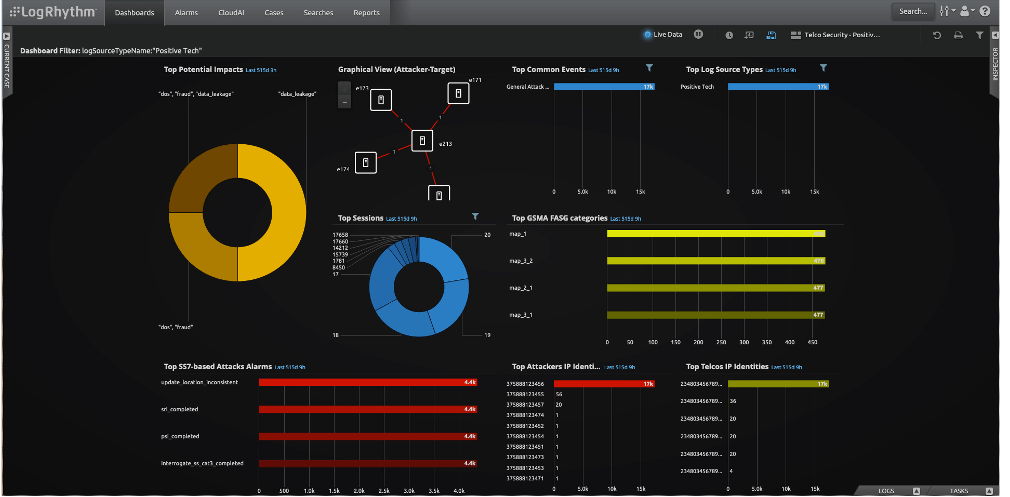
Figure 5: Telco security dashboard
LogRhythm Scheduled Reporting Capabilities
LogRhythm’s comprehensive reporting capabilities combine the convenience of prepackaged reports with the flexibility of custom reports to allow for effortless distribution of data. LogRhythm can be configured to send alerts and reports directly to individuals, groups, shared directories, helpdesks — or any combination — allowing for the effective dissemination of information across a distributed workforce. Reports can be scheduled for delivery or generated on-demand. They are easily accessed via the real-time Personal Dashboard, email notifications, or exported tools such as Excel files and PDF files.
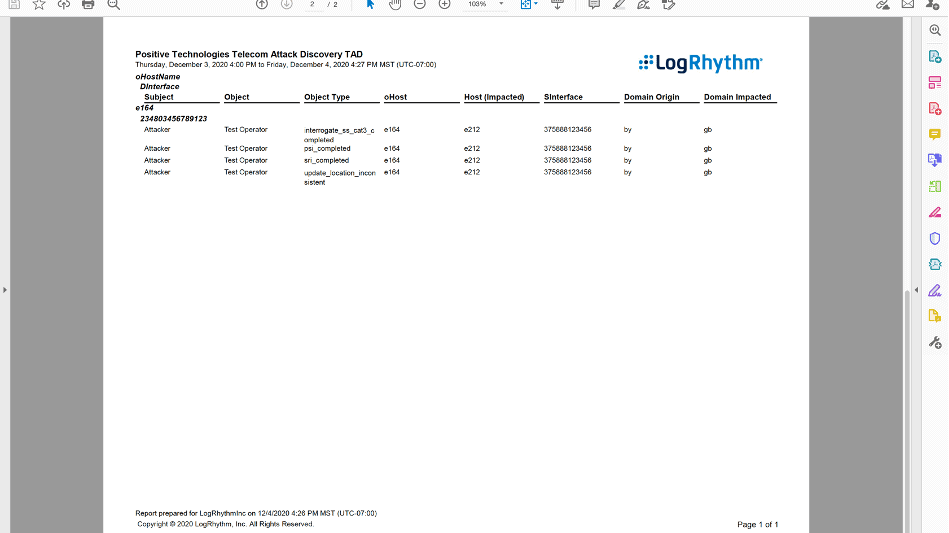
Figure 6: Telco security schedule report
Detect SS7 Attacks with SOAR
LogRhythm Case Management and SmartResponse automation™ streamline incident response and enable security orchestration with prescribed analyst workflows, team collaboration tools, and built-in escalation processes. To help mitigate SS7 attacks, LogRhythm’s unique SmartResponse enables automated incident response which improves time to response (TTR). Analysts can execute fully automated actions such as case creation or assign playbooks. LogRhythm also has options for workflow automation to specific users for review before they are executed in semi-automated, approval-based response actions. Teams can decide which actions to automate so that they can focus on more critical issues and less manual tasks.
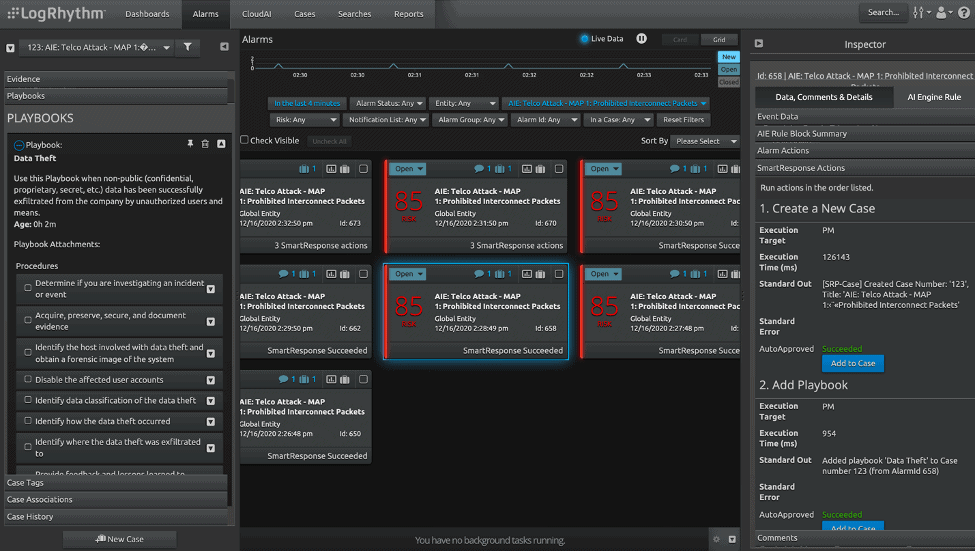
Figure 9: Automated response on adding playbook
Secure Your Telecommunication Organization with LogRhythm
With the increasing number of cyberattacks on telecommunication organizations, it’s critical to mature your security operations by implementing a security orchestration, automation, and response (SOAR) solution that can streamline threat investigation. LogRhythm’s SOAR product, RespondX, decreases workflow steps by dissecting use cases into manageable pieces. As your team standardizes process and becomes more efficient, you can take on complex telco-relevant use cases at scale.
The post How to Detect and Respond to SS7 Attacks — OT Telco Use Cases appeared first on LogRhythm.
*** This is a Security Bloggers Network syndicated blog from LogRhythm authored by Kelsey Gast. Read the original post at: https://logrhythm.com/blog/how-to-detect-and-respond-to-ss7-attacks-ot-telco-use-cases/





