Unisys Adds Visualization Tools to Stealth Platform
Unisys has updated its Stealth platform that automates microsegmentation of networking environments to now include visualization and dashboard tools that make it easier to track an organization’s overall security posture in real-time.
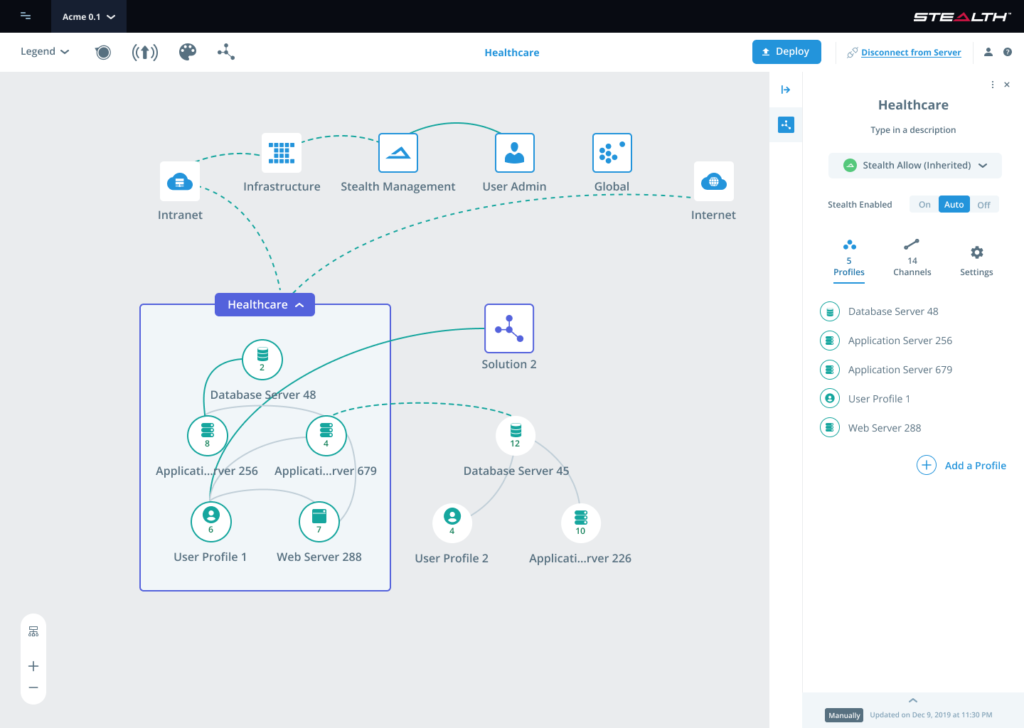
Vishal Gupta, chief technology officer and senior vice president of products and platforms at Unisys, said previous versions of the Stealth platform leveraged machine learning algorithms to simplify microsegmentation. Version 6.0 makes it easier for cybersecurity teams to visualize the relationship between all the endpoints that make up a modern networking environment, including multiple clouds and various edge computing platforms.
Gupta said Stealth makes it possible to apply a consistent set of streamlined security policies across thousands of network communication flows. That’s becoming increasingly critical as organizations begin to deploy across an extended enterprise microservices-based applications that have multiple dependencies. It simply isn’t possible for IT teams to determine how to apply microsegmentation optimally to create a zero-trust IT environment without relying on artificial intelligence (AI) in the form of machine learning algorithms, he said.
Many organizations have been relying on expensive virtual network overlays to apply microsegmentation to network underlays made up of heterogeneous networking equipment. The Unisys approach is less complex because it enables IT teams to employ a set of wizards to automatically segment networks based on the communication flows observed, said Gupta. Those communication flows are discovered using a mix of agent and agentless approaches using wizards, which can be deployed in about 30 minutes, and can be applied to Microsoft Azure, Amazon Web Services (AWS) and Google Cloud platforms, as well as macOS, iOS, iPadOS and Android operating systems.
Just as significantly, Gupta said Stealth enables cybersecurity teams to apply policies to microsegmented networks with no intervention required on the part of a network operations team. In dynamic computing environments, cybersecurity teams need to be empowered to quickly address issues as they arise, he noted.
Cybersecurity teams also need to be able to more easily create and maintain a zero-trust IT environment now that most employees are working from home to help combat the spread of the COVID-19 pandemic, Gupta added. As most IT professionals are also working from home, it’s never been more important for cybersecurity teams to be self-sufficient in terms of their ability to enforce security policies, he said.
Of course, it’s exceedingly difficult to determine when and how to microsegment an enterprise network without visualization tools. Unisys is effectively plugging a gap in its portfolio that should enable cybersecurity teams to more easily apply and adjust policies as IT environments are continuously updated. That capability when combined with the machine learning algorithms embedded in Stealth should also limit the total costs by making it more feasible for an existing cybersecurity team to monitor an ever-expanding attack surface.
It’s now only a matter of time before cybersecurity teams will be relying more on machine learning algorithms and other forms of AI to combat cybersecurity threats. The challenge now is determining where those algorithms will leave off and the need for human expertise begins.