Top 5 takeaways from the latest Kubernetes security report
Most organizations have a DevSecOps initiative and responsibility for container security continues to evolve and remains decentralized. These are two of the findings from our latest report on the state of container and Kubernetes security (Download your copy today). We’re kicking off the fourth edition of our State of Kubernetes and Container Security Report (Fall 2020 edition) by examining how companies are adopting containers, Kubernetes, and cloud-native technologies while meeting the challenges of securing their vital Kubernetes applications. Based on responses from more than 400 Kubernetes and container users across IT security, DevOps, engineering, and product roles, the findings in this report serve as a benchmark for organizations when navigating their cloud-native security use cases and priorities.
Of all the survey responses, the following five findings stand out in particular.
1) 83% of organizations have a DevSecOps initiative
While Security as code, the holy grail of Kubernetes security, remains out of reach for the majority of organizations, DevSecOps is not just a buzzword. Our survey found that only 17% of respondents continue to operate DevOps separate from security. Even more promising is the fact that 43% of respondents have either integrated security across the entire container life cycle or have taken it one step further by enforcing security policies as code.

Download the full report
Download this report to learn more about the latest in container and Kubernetes adoption and security trends
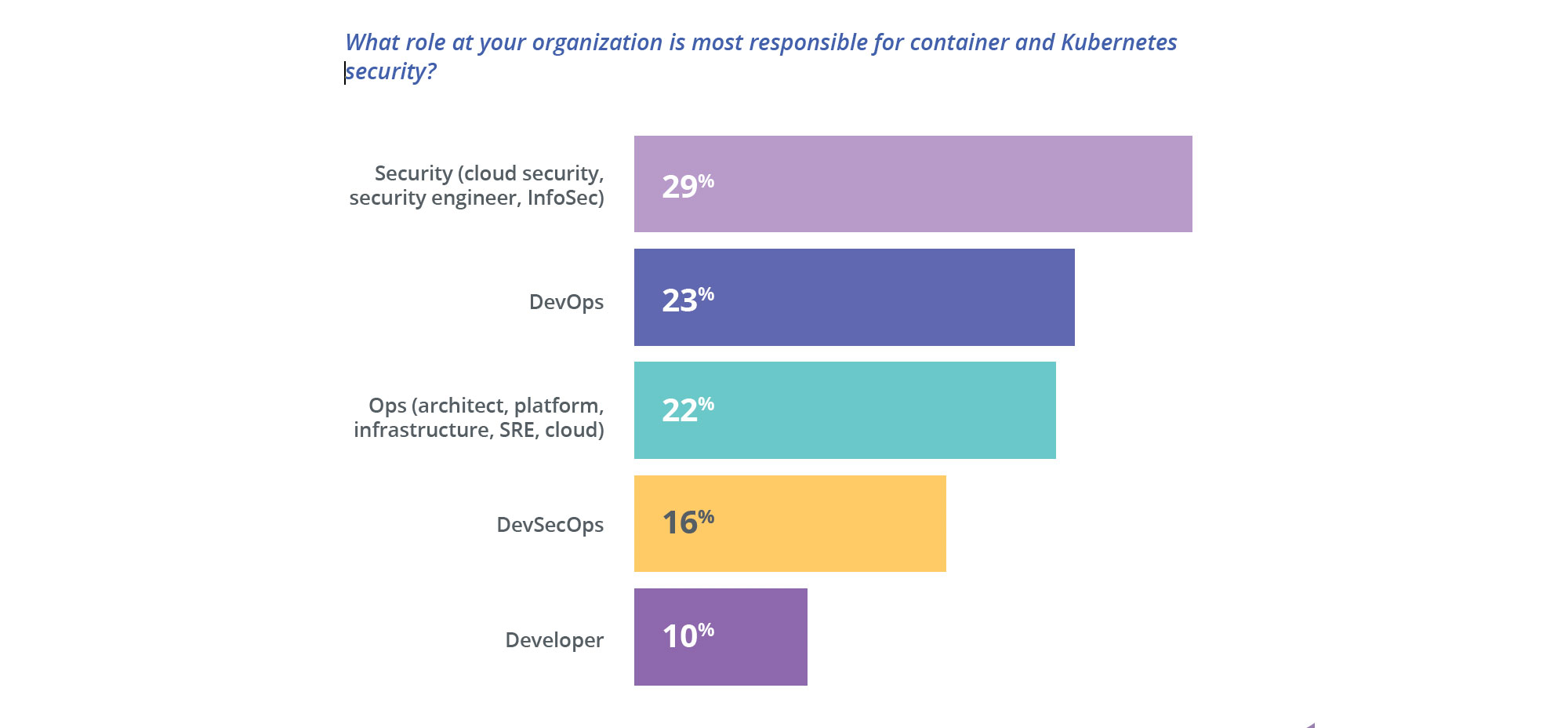
2) 29% of respondents consider the Security team to be responsible for Kubernetes security, followed by DevOps at 23%
Across various IT roles, Security is the single role most cited as responsible for securing containers and Kubernetes. But taken together, the myriad operational roles of DevOps, Ops, and DevSecOps beat out security, at 61%. Containers and Kubernetes adoption is primarily driven by DevOps, so it’s not surprising to see respondents naming them as responsible for securing this new technology. To bridge these gaps, container and Kubernetes security tooling must facilitate close collaboration among different teams – from Security to DevOps to Ops to Developers – instead of perpetuating the silos that often plague organizations.
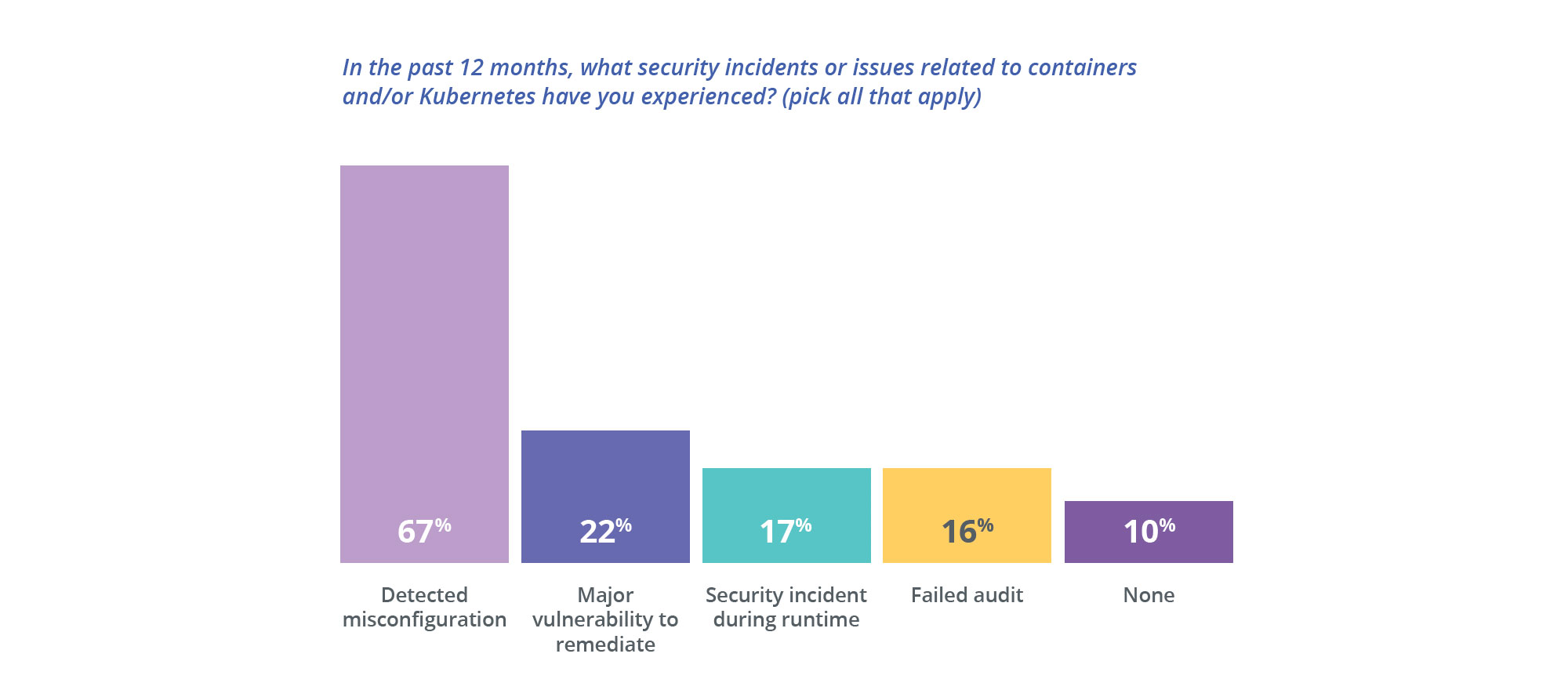
3) 90% of respondents have experienced a security incident in Kubernetes environments
A staggering 90% of survey respondents have experienced a security incident in their Kubernetes and container environments during the last 12 months.
Human error is the most often cited cause of data breaches and hacks, and containers and Kubernetes have a lot of knobs and dials, increasing the chances of human error. Getting all the configurations correct is often very challenging, even for seasoned developers. Not surprisingly, 67% of respondents have experienced a misconfiguration incident in their environments over the last 12 months. Almost a quarter reported detecting a major vulnerability, 17% experienced a security incident during runtime, and 16% have failed a compliance audit.
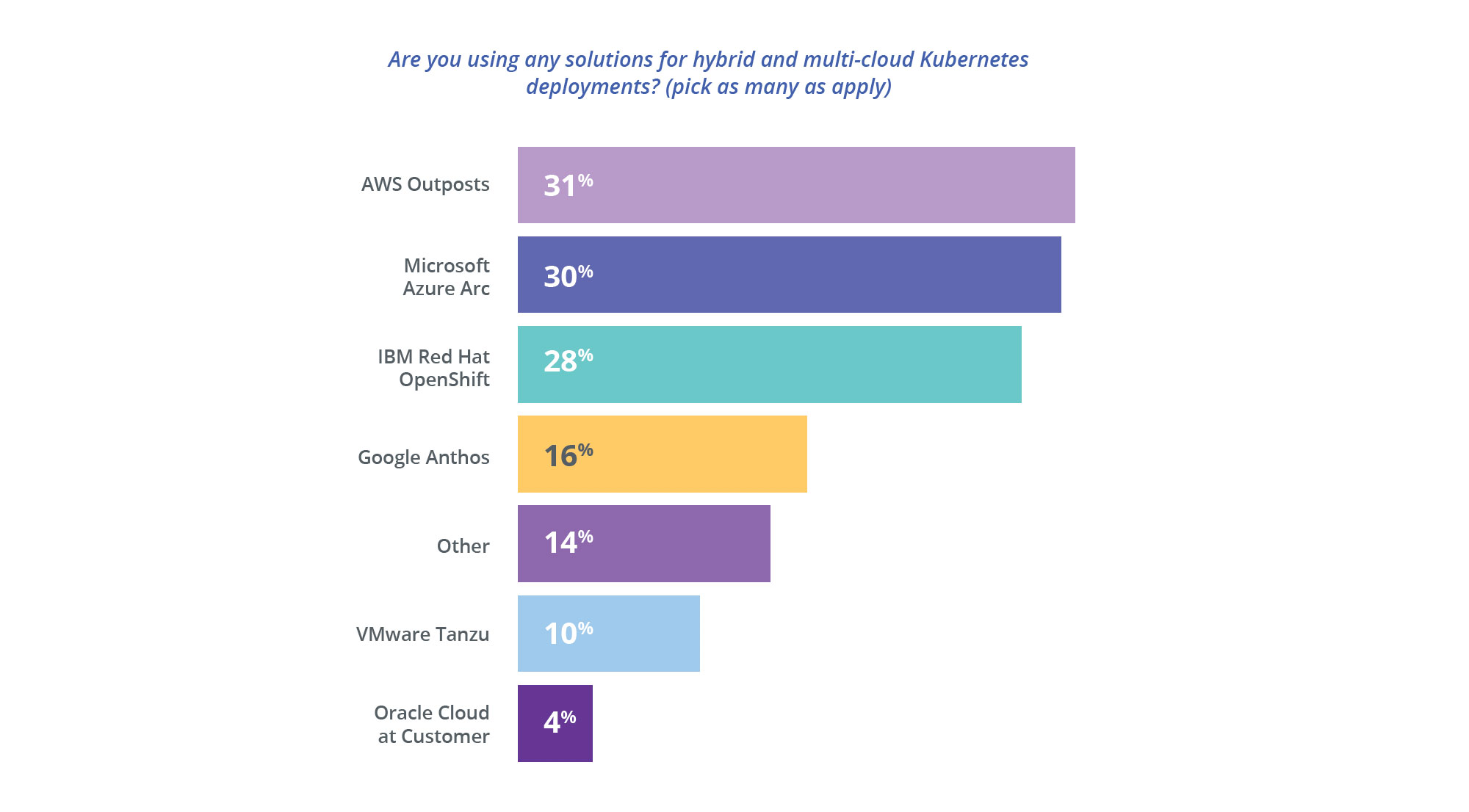
4) AWS Outposts, Microsoft Azure Arc, and Red Hat OpenShift are neck and neck for hybrid deployments
As we’ve seen hybrid deployments remain popular, we wanted to understand how organizations were deploying in hybrid mode. The popularity of technologies from the public cloud providers follows a similar arc of overall platform popularity, with one glaring difference: Amazon’s managed Kubernetes service (EKS) enjoys a 50% advantage in use over its next nearest competitor in our survey findings, Azure (AKS), but Amazon Outposts and Azure Arc are deployed at nearly equivalent levels.
Amazon, given its dominance in the cloud, took longer to support a hybrid approach, and customer anecdotes indicate its pricing sometimes causes sticker shock. Google Anthos, deployed at about half the rate of either AWS’ or Azure’s hybrid offering, has not enjoyed robust market growth.
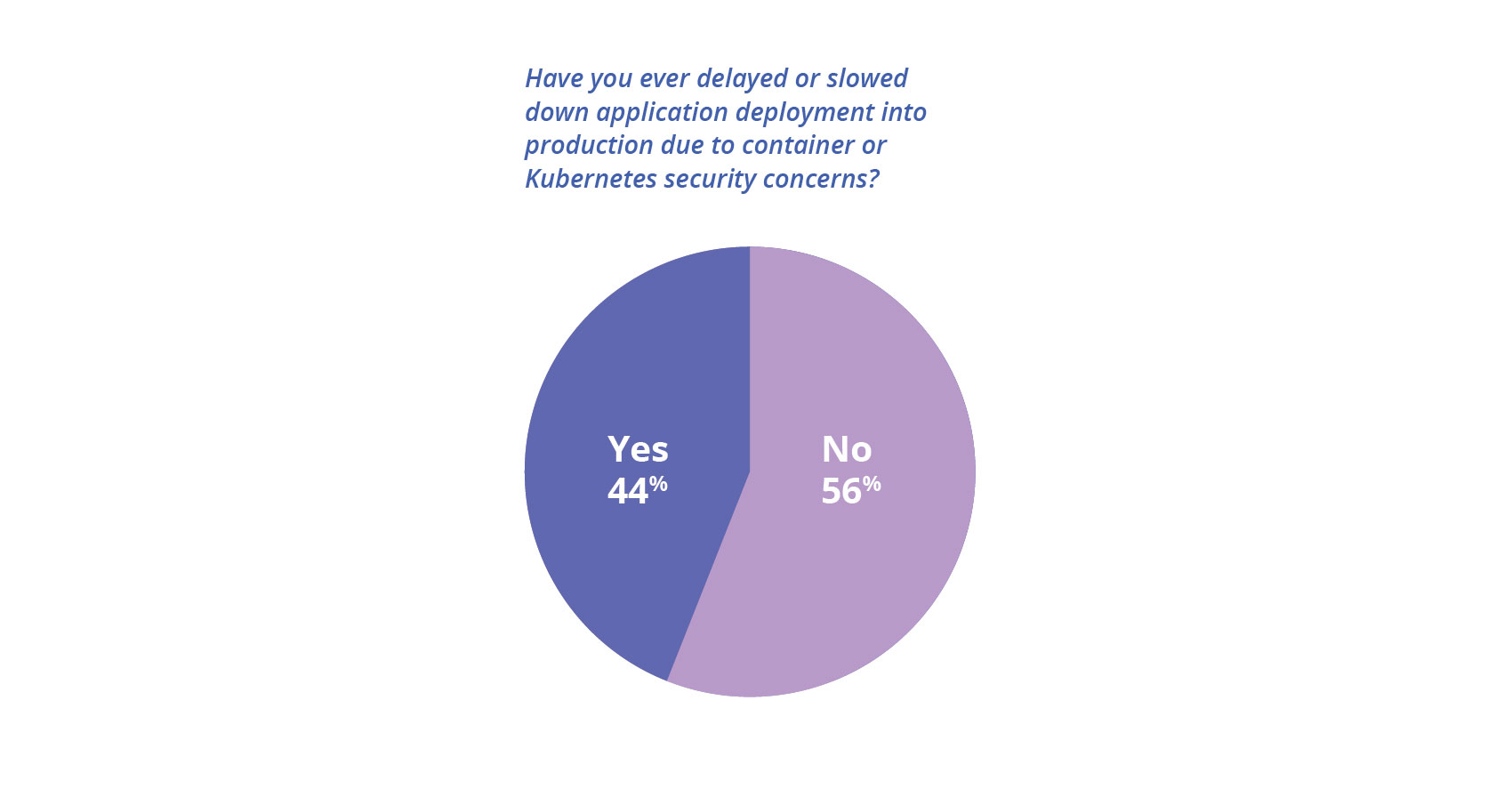
5) Nearly half of organizations have delayed deploying apps into production due to security concerns
Faster application development and release, quicker bug fixes, and increased feature velocity are three of the most often cited benefits of containerization. However, when security becomes an afterthought, you risk diminishing the greatest gain of containerization – agility. Just as we found in our study eight months ago, nearly half of the respondents (44%) have had to delay an application rollout because of security concerns.
Implications for container and Kubernetes security
The findings in this survey reinforce the need to shift security left and embed it into DevOps workflows earlier in the container life cycle. Otherwise you are putting at risk the core benefit of faster application development and release by treating security as an afterthought. With nearly half of our respondents delaying production rollouts because of security concerns, clearly a lack of security is inhibiting business acceleration and innovation. Download the full report to gain further insights into the state of Kubernetes and container adoption and security.
*** This is a Security Bloggers Network syndicated blog from The Container Security Blog on StackRox authored by The Container Security Blog on StackRox. Read the original post at: https://www.stackrox.com/post/2020/09/top-5-takeaways-from-the-latest-kubernetes-security-report/






