Protect Yourself from Social Media Scams

Technology and social platforms allow us to connect like never before and change how we communicate and interact as societies. We live in a world where toddlers can navigate smartphones better than their grandparents. Before, we read the morning newspaper; now, one of the first things we do when we wake up is check our social media accounts. This is our new way of staying connected to the world. With one click or tap, we can see pictures from exotic places, videos of puppies and kittens that keep us as happy as coffee does, and the personal thoughts of favorite celebrities, authors, and artists. Social media keeps us connected in ways that were not possible before. However, with this connectivity also comes vulnerability. As the way humans interact changes, the scams change along with it. As a result, we need to be aware of social media scams and how we can protect ourselves.
Social Media Scams
When we think of scams, many of us think of the famous “Nigerian Prince”. Most of us have heard of it and there are even jokes about it. Yet, it was very successful in its time. Has it become less successful now? Probably. Many in the current generations are tech-savvy users and we are becoming more educated on “obvious” schemes such as that one. But, with our advancement and awareness comes the advancement of these attacks and attackers.
Social media scams are rapidly becoming more popular. Forbes states, “people who are active on Facebook, Instagram, and Snapchat are 30% more likely to be victims of fraud due to increased exposure and information sharing.” Various social media scams utilize basic social engineering techniques to build rapport quickly. Techniques such as using sympathetic themes and open-ended questions, validating the target, and portraying selflessness are just a few techniques making these scams more believable. What does this mean for us? As these attacks morph, so must our mindset. We must be prepared to guard ourselves and those around us against these threats.
Seeing Through the Facade
Now that you’re more aware of one of the common vectors for malicious social engineering attacks today, you’re halfway there. Breathe! It all sounds scary and it can be. However, if you’re aware of the risks associated with social media and some of the more frequently used attacks, you are very well equipped to avoid them. So, what are some of the common attacks used today via social media?
Romance Scams
Romance scams are unique in that criminals prey on the target’s need for an emotional connection in order to execute the scam. The scammer will make contact with the target and try to establish a romantic connection with them. As the relationship progresses, the scammer will start finding ways to ask for money. To protect yourself from this scam, there are a few things you can do:
- Be aware if someone seems “too perfect” in their pictures. You can do a reverse image search on images.google.com to find out if the user is copying their personal profile pictures from the Internet.
- Ask specific questions and be alert for any inconsistencies.
- Be wary of those who always have an excuse as to why they cannot meet in person (constantly traveling, overseas, military) and constantly postpone plans to do so.
- Above all, never send money to someone you have never met.
If you would like to learn more about romance scams, check out Scam Artists on the Framework and our October Newsletter.
Social Phishing
Anyone can be caught off–guard by a social media phish. Last week, I received a direct message on Instagram from a close friend. It said, “I found something you might like” and had a link attached. Something didn’t feel right, so I asked if it was really from her. She said no and that she had received the same message from a friend—and that her account had been compromised when she clicked on the link. This kind of attack is not specific to Instagram, though. Facebook, Twitter, YouTube, Snapchat, LinkedIn, and other social media platforms have the same potential vulnerabilities. How can you protect yourself?
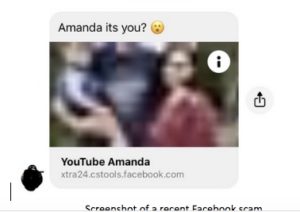
Screenshot of a recent Facebook scam
- Be aware and wary. Keep an eye out for any wording or messages that seems unnatural.
- Don’t click on links just because they were sent to you by a friend, inspect them first. Be wary of clicking on a link that contains extra letters and numbers in the URL, such as the “xtra24.cstools” in the picture above.
- Keep in mind, you have no idea a stranger’s motive for requesting to follow or connect with you. It is possible that they are completely innocent with no malicious intent. Just remember that allowing strangers to connect with you gives them access to whatever personal details your profile contains as well as the actions you perform, such as posting, liking, and commenting.
Quizzes
There’s nothing more tempting than finding out which Riverdale character you’re most like, or who you’re most romantically compatible with from Firefly (I mean, who didn’t have a crush on Mal in that pretty floral bonnet?). Unfortunately, scammers can use catchy quizzes like these to plant malware or harvest personal information. Even if the quiz is legitimate, personal information is still being gathered which can be used for targeted ads.
The best way to protect yourself from a potential scam in this instance is to simply refrain from taking the quiz. If you just need to know which Disney princess you would be best friends with (guilty), be sure to look at the fine print. Most will say that by participating in the quiz, you are agreeing to the site’s terms of use or terms of service. Often, you will find this agreement grants the third-party partner access to your social media, list of friends, and much more. You will need to determine if all those requirements are things you want this party to have access to.
Learning more about these widely used attacks and finding real life examples can help you be more cautious if one happens to come your way.
Be Aware—Not Scared
The most important step you can take when facing social media and its many inherent risks is to take time to understand the attacker’s mindset. If you know what they’re after, you can protect yourself. Take a few moments and look at your social media accounts from the attacker’s perspective. Do you publicly post about birthdays and anniversaries? Do you post in your bio where you work? Did you geotag your location when at your favorite restaurant last week? These are the bits of information attackers seek. Alone, these pieces of data may not seem like much information. When you add them together, though, they form a picture of your life. Attackers can use this information to send targeted phishing emails your way as well as targeted vishing calls.
One simple way to avoid giving attackers this information: set your profile to private. Be sure to check your privacy settings on a regular basis to see if any setting has been added, edited, or deleted. As an attempt to stay more secure, social media platforms often update their privacy settings. Because of this, your settings may be affected without your knowing. Be sure to check them regularly so you can remain aware and up to date on how your personal information is being shared.
Continue Learning
From newspapers evolving to smartphones, and Nigerian princes evolving to targeted phishing, technology and social platforms allow us to connect like never before. This ability to connect brings some dangers along with it. Hopefully, it also brings people greater awareness and widespread education. We invite you to explore our blog archives for more information regarding social media scams. Additionally, you can visit the Social-Engineer.Org site: https://www.social-engineer.org/framework/general-discussion/ to learn more on this topic. There you can find dozens of examples on scams, learn the psychology behind them, and be better equipped to handle attacks.
If you have already been a victim of a social media scam, or have received a scam message, be sure to report it to the social media platform on which it took place. This helps the platform stay current on its security and keep its users safe. With these and other resources, you can learn how to better protect yourself and those around you.
Sources:
https://www.forbes.com/sites/forbestechcouncil/2019/09/09/top-social-media-scams-and-how-to-avoid-them/#7a5dd343873d
https://www.kivitv.com/news/bbb-scammers-using-social-media-in-new-phishing-scam
https://www.social-engineer.org/framework/attack-vectors/attack-cycle/
https://mashable.com/article/wendi-deng-instagram-scam/#RPFrUmq5_sqB
https://latesthackingnews.com/2019/01/29/a-youtube-social-engineering-scam-poses-as-popular-influencer-accounts/
https://www.forbes.com/sites/jessicabaron/2019/04/30/social-media-platforms-increasingly-popular-with-cybercriminals/#188f23877324
https://www.scamwatch.gov.au/types-of-scams/unexpected-money/nigerian-scams
https://www.social-engineer.org/framework/psychological-principles/instant-rapport/
https://www.thebalancecareers.com/how-to-check-emails-for-fake-hyperlinks-3515356
https://inspiredelearning.com/blog/social-phishing/
The post Protect Yourself from Social Media Scams appeared first on Security Through Education.
*** This is a Security Bloggers Network syndicated blog from Security Through Education authored by SEORG. Read the original post at: https://www.social-engineer.org/general-blog/protect-yourself-from-social-media%E2%80%AFscams/



