Talks @ RSAC 2019: Fileless Malware and How to Detect Them
Fileless malware is becoming more prevalent. Here’s what you need to know, according to a session at RSAC 2019
RSA Conference is where thousands of attendees get together to discuss the latest on cybersecurity threats, tactics and solutions. With hundreds of sessions and talks, it’s hard to attend or consolidate all the different ideas, but here are few key lessons from the talk, “Combating the Scourge of Fileless Attacks,” March 4, which I learned and believe every blue-teamer should know.
What are Fileless Malware?
Fileless malware is a malicious software that utilizes legitimate or whitelisted software to infect other applications and machines. These malwares are known to evade traditional detection mechanisms involving anti-virus solutions, whitelisting procedures and static signature-based detection.
Fileless malware emerged in 2017 as a mainstream type of attack, but many of these attacks have been lurking around for a while. These are one of the most sophisticated and difficult detect. More recent, high-profile fileless attacks include the hack of the Democratic National Committee (DNC) and the Equifax breach.
What makes it dangerous is its ability to load itself and execute directly in system’s memory.
How it Works
Unlike traditional file-based malwares, fileless malwares are not stored in a file nor are installed as some background application/software. These are directly loaded and execute in memory. How? The most common attack vector is email phishing scams, which involve the following steps to infect an end user’s machine:
- Malicious email received
- File opened
- MACRO – DDE Injection
- PowerShell script (highly obfuscated) execution and registry changes for persistence
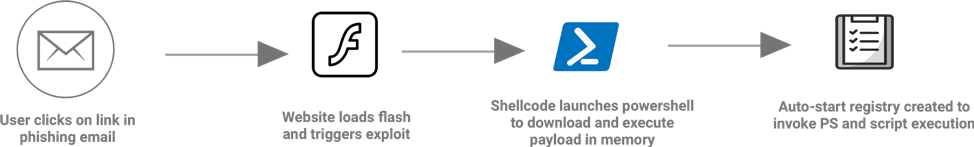 Through the process there is no installation of any new software or data hard disk modification in the hard disk; this makes it stealthy to common AV detection mechanisms.
Through the process there is no installation of any new software or data hard disk modification in the hard disk; this makes it stealthy to common AV detection mechanisms.
Detection Strategies
- Keep existing software up-to-date.
- Monitor powershell scripts and other scripting engines in the environments or systems.
- Don’t rely on behavioral detection—it’s usually too late. Instead, monitor new system processes and subsequent registry changes.
- Enforce Group Policy Object (GPO) across the organization for macros.
That’s it! Thanks, Stuart McClure and Brian Robinson for an informative talk. Let me know in the comments below what you think about these detection strategies.



