Are You Vulnerable to BEC Fraud?
In the security realm, the $64,000 question for many is, “Am I or is my company vulnerable to BEC fraud?”
While that’s the money question, perhaps first question should be, “What is BEC fraud?”
What is BEC Fraud?
BEC—or business email compromise—fraud, according to the FBI, is:
“… a sophisticated scam targeting businesses working with foreign suppliers and companies that regularly perform wire transfer payments. The scam is carried out by compromising legitimate business e-mail accounts through social engineering or computer intrusion techniques to conduct unauthorized transfers of funds.”
BEC is not to be confused with the equally nefarious email account compromise (EAC), which “targets the general public and professionals associated with, but not limited to, financial and lending institutions, real estate companies, and law firms. Perpetrators of EAC use compromised e-mails to request payments to fraudulent locations,” according to the FBI.
Is BEC Fraud Really of Concern?
The answer to that question largely depends on whether your company’s executives, accountants and others who touch finances are sensitized to the existence of BEC fraud. If not, then take note.
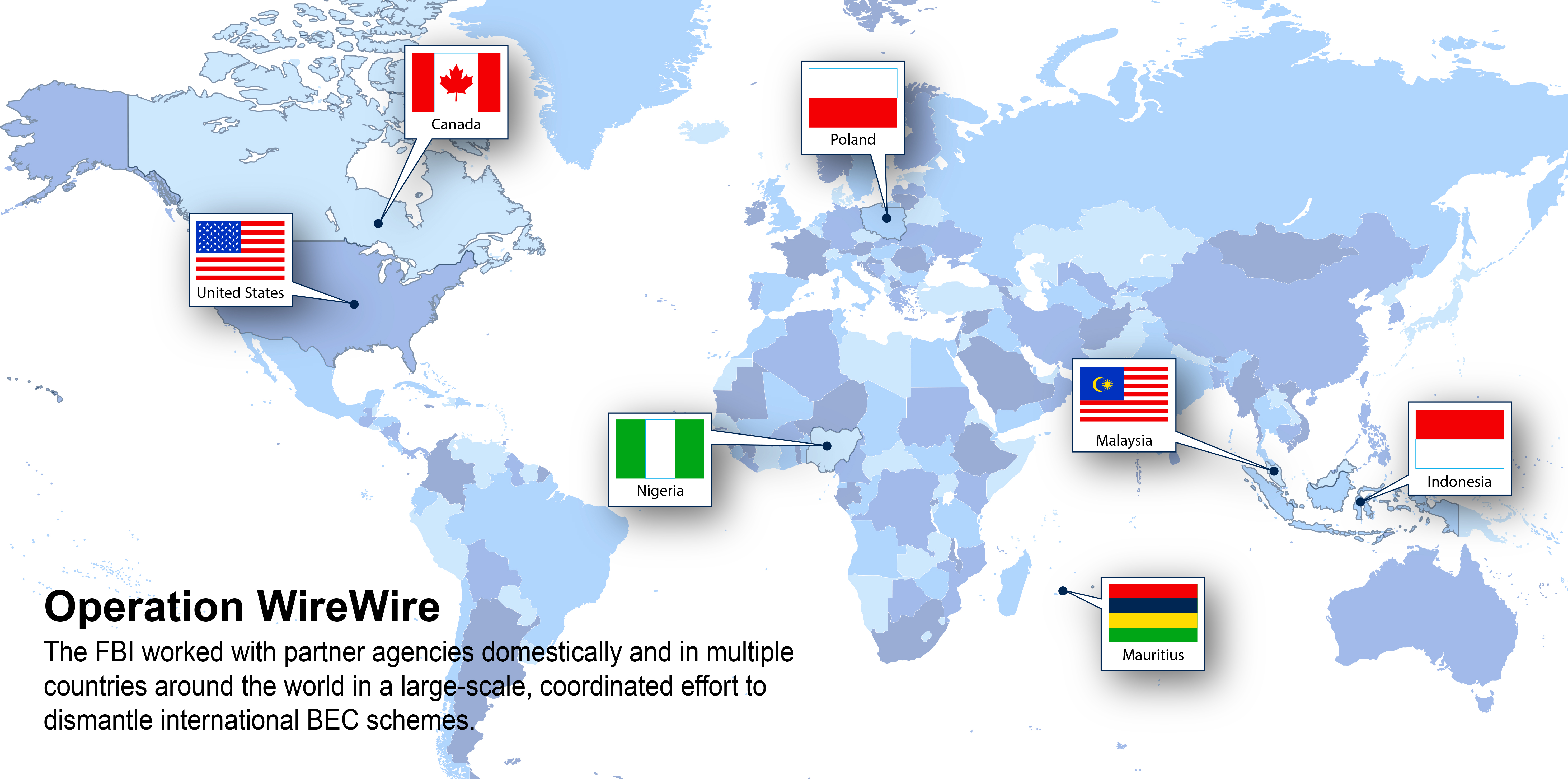
In mid-June 2018, the FBI announced a global takedown of hundreds of individuals who were involved in sophisticated BEC fraud schemes. The international law enforcement effort, “Operation WireWire,” saw three individuals in Canada, Mauritius and Poland arrested, 29 in Nigeria and 42 in the United States, for a total of 74. The six-month effort involved law enforcement organizations around the globe.
The FBI tells us that since the Internet Crime Complaint Center (IC3) began tracking BEC fraud (and variants), more than $3.7 billion has been reported as stolen.
Recognizing BEC Fraud
The most common approach from the miscreants occurs when the CEO is on the move.
The criminals first target an individual with fiscal authority and send that person an impersonal communication (SMS, email, IM), impersonating the CEO (or other senior executive) who is not readily available for contact and confirmation. If the email is sent from within the company infrastructure, via the compromised email server, the recipient’s reviews of the header content will be negative for anomalous content.
It is within the activity requested that the clues can be found.
The sense of urgency is almost always present, the FBI said. In addition, account numbers may not be the same as those used previously or the financial institution isn’t the same as what the company has engaged with in the past. And wire transfers are the most often requested action, as they are also the most difficult to claw back, given the instantaneous nature of the financial vehicle. But a check mailed to a mule (unwitting intermediary) also is an avenue used to move money.
Is money the only target? No. As detailed by the U.S. Department of Justice, personal identifying information (PII) may be as valuable to the criminal enterprise, as it will permit a future targeting effort. The one thing we can count on from the cybercriminal is that every action is to either create an immediate monetization or to enable a future monetization.
Three examples are provided by the FBI:
What are the Remedies?
- Use data loss protection processes, procedures and applications to detect the heuristic nuances of the emails or other means to reach in externally and socially engineer the action of an employee.
- Put in place two-person authorization protocols for transactions over a certain amount.
- Require all vendors use 2FA with your company; in this manner, their accounts within your infrastructure have an additional level of protection. It may not be your company that is compromised, but it is your company that is being targeted for the BEC fraud.
- When executives are out-of-pocket, either on business or personal travel, have in place a precise and easily verifiable means to validate all transactions that may be performed involving financial instruments to protect against being socially engineered.
Remember, you’re not paranoid if they really are out to get you.
Which reminds me, how does your company handle financial transactions?




