Data Breaches at The Intersection of Vulnerabilities and Data Discovery

As we learn more about the inner workings of the malware that infected Target and most likely Neiman Marcus during the holiday season I thought it would be helpful to draw some conclusions about not only protecting against malware such as KAPTOXA and BlackPOS but some insights into how you can transform your security posture to prevent becoming the next data breach victim.
iSIGHT Partners in conjunction with the U.S. Secret Service performed a detailed analysis of the KAPTOXA operation which was behind the large scale point-of sale cyber-crime breaches announced this month.
After reviewing the January 14, document published by iSIGHT Partners (http://media.scmagazine.com/documents/60/kaptoxa_14816.pdf) which highlighted the characteristics of Trojan.POSRAM and another detailed analysis and background by IntelCrawler (http://intelcrawler.com/about/press08) on BlackPOS from which Trojan.POSRAM is derived, I wanted to point out some of the more interesting facts gleaned from both reports:
• Author is believed to be around 17 years old
• First builds of the malware were offered for 2000 USD
• It scans memory for card data track1/track2
• It stores card data on a the POS device and staging server in plain text
While it hasn’t been fully determined how the malware spread to multiple POS systems within these retail environments, its safe to assume that it might have been a combination of vulnerable systems as well as weak administration controls around remote management and passwords.
But Wait! Did you say data stored in plain text?
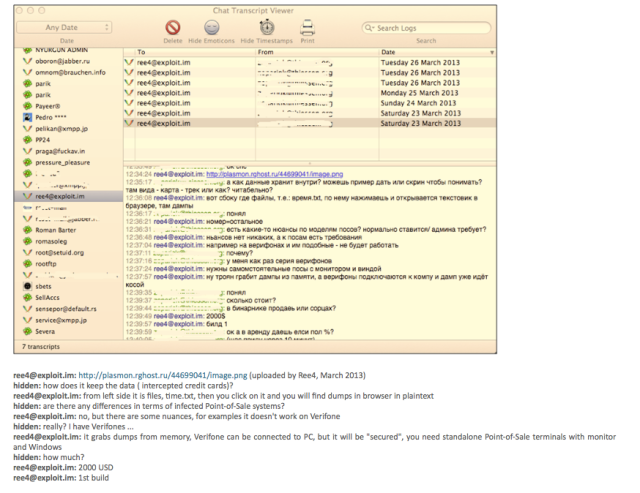
That’s right, after slurping the data from memory Trojan.POSRAM stores the data in
%windir%\system32\winxml.dll. Then between the hours of 10am and 5pm would periodically send that file over NetBIOS to a temporary dump server. If we consider the origins of Trojan.POSRAM being based on BlackPOS we can determine that the data is being stored in this dll file and other staging files in plain text. (See insert above for IntelCrawler chat with BlackPOS author)
So this gets to the intersection of why we believe organizations are missing some of the biggest points in securing their environments against these types of threats:
– Concentrated endpoint vulnerability management
– An effort to consistently assess where sensitive data is being stored
Endpoint Vulnerability Management
In todays world of disconnected systems, remote offices and more, it is increasingly more difficult to accurately detect vulnerabilities on systems using traditional network scanning methodologies. Without having an endpoint focus, results are often impossible to gather and contain huge amounts of false positives.
Considering the retail environments, looking at Target with approximately 1921 locations to scan and manage vulnerabilities, this is an overwhelming task. Traditional network vulnerability scanning solutions require appliances, credentials and lots of network bandwidth and connectivity to accurately scan these locations.
Lets also consider not only the retail locations in these environments but the vast amount of workers who are constantly on the road connecting to various networks and never are properly assessed against vulnerabilities because they are remote when the centralized network vulnerability scans are scheduled. These endpoints become the launch point for infiltration into the corporate network. Lets say an end-user visits a malicious link that installs a piece of malware that lays dormant until its connected to the corporate network and uses this as the infection point. In the case of retailers : Game over, BlackPOS is now on the network looking for POS systems to infiltrate.
Data Discovery
So in most cases, the anti-malware, network defenses and other defense in depth technologies should detect these breaches correct? No. As attackers become more sophisticated there is a further gap between the instant a piece of malware is released and the time which proactive protection is released by security vendors. But what are some other things you can proactively do to prevent these data breaches?
I can’t say it any louder. CONSTANTLY ASSESS for UNENCRYPTED CARD DATA!!
We help organizations on a daily basis understand where they have sensitive data being stored. And to be honest we find a lot of data that organizations never knew existed in their environment. Be it unintended backup storage, accidental end user copies, or even development logging on servers. Data is there whether you want it to be there or not. It happens.
The Power Of Combined Intelligence
At iScan Online, we provide customers with combined intelligence to know what devices are at risk to compromise from existing vulnerabilities as well as the intelligence to detect if there is sensitive unencrypted data at rest on the device. Armed with these pieces of information you can then take proactive steps to reduce the risk associated with these devices by first removing or encrypting the sensitive data and secondly applying remediation to remove the discovered vulnerabilities on the device.
Take a look at these sample reports from a vulnerability scan as well as a data discovery scan:
Vulnerability Report
Data Discovery Report
If you want more information or to try out iScan Online visit:
www.iscanonline.com
*** This is a Security Bloggers Network syndicated blog from iScan Online Blog authored by Billy Austin. Read the original post at: https://iscanme.wordpress.com/2014/01/22/data-breaches-at-the-intersection-of-vulnerabilities-and-data-discovery/



