LockBit Ransomware Hacked: Database and Victim Chats Leaked

Image courtesy of crypto.news
A group claiming to be from Prague has hacked LockBit’s dark web panel, leaking sensitive data including its internal systems and Bitcoin wallets. LockBit, a notorious ransomware gang, had their internal data package compromised, which included over 60,000 Bitcoin BTC addresses, approximately 75 user credentials, and ransom negotiation logs. Analysts at SlowMist published a blog post detailing the breach.
The attackers accessed a lightweight PHP-based management platform utilized by LockBit. SlowMist speculated that the hacker likely exploited a PHP vulnerability, tracked as CVE-2024-4577, to breach the web backend. LockBit later claimed that only the lightweight panel was compromised, reassuring that "no decryptors were stolen, and no company data was affected." They have since offered a bounty for information on the hacker, despite the U.S. government previously offering up to $15 million for information on LockBit members.
Chats and Data Leaked
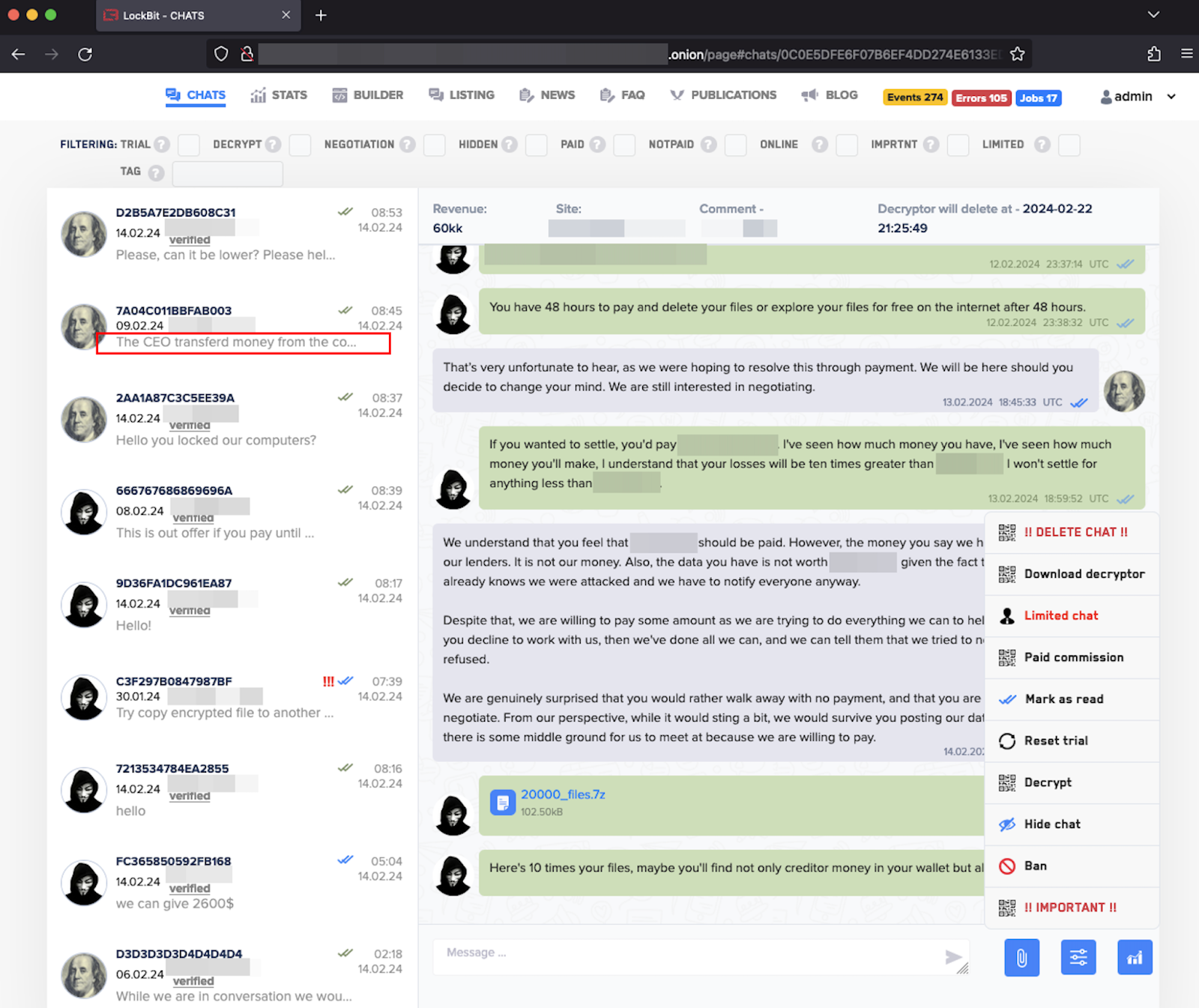
Image courtesy of SlowMist
The breach revealed chats between LockBit and its victims, showing a detailed record of ransom negotiations. This data could be critical for those monitoring ransomware operations and developing solutions to combat such threats. Companies focused on identity and access management (IAM) could leverage these insights to enhance their security measures, particularly when considering solutions like SSO and MFA.
BleepingComputer reported that the SQL dump included victim names and communications spanning several months. The archived data also contained individual encryptor builds developed by affiliates, potentially assisting in understanding how these ransomware operations function.
Previous Attacks on LockBit
LockBit has faced previous attacks, including a significant law enforcement operation dubbed “Operation Cronos” in February 2024, which resulted in the seizure of their website and data. This operation led to numerous arrests associated with the group, including Russian nationals linked to deploying LockBit ransomware. The U.S. Department of Justice has unsealed indictments against these individuals, highlighting ongoing efforts to dismantle ransomware networks.

Image courtesy of TechRadar
In light of these developments, organizations must reassess their security protocols. Implementing secure SSO and user management becomes essential for protecting sensitive data. SSOJet’s API-first platform offers robust solutions for enterprises, featuring directory sync, SAML, OIDC, and magic link authentication, which can mitigate risks associated with such breaches.
For enterprises looking to enhance their security frameworks, SSOJet provides the tools necessary for effective user management and secure authentication. Explore our services or contact us to learn more about how we can help safeguard your organization against ransomware threats.
*** This is a Security Bloggers Network syndicated blog from SSOJet authored by Goverdhan Sisodia. Read the original post at: https://ssojet.com/blog/lockbit-ransomware-hacked-database-and-victim-chats-leaked/



