Unlocking the Power of BIN Monitoring for Compromised Cards
The Growing Need for BIN Monitoring
According to 2025 statistics, 63% of US cardholders have fallen victim to fraud, with many victims experiencing multiple instances of fraud. Amid this alarming trend, financial institutions must adopt intentional strategies to stay ahead of fraud to protect both their customers and assets. One critical yet often overlooked area of risk is the exposure of full payment card numbers on the dark web. Enzoic’s BIN Monitoring for compromised cards empowers banks, credit unions, and other financial organizations to proactively detect compromised card numbers associated with their BINs and act on this intelligence to mitigate fraud before it occurs.
A Bank Identification Number (BIN), sometimes referred to as an Issuer Identification Number (IIN), is the first six to eight digits of a payment card number and identifies the issuing financial institution. With Enzoic’s Credit Card and BIN Monitoring, organizations only need to provide the BIN, ensuring sensitive cardholder data never leaves your environment. Enzoic then identifies and returns full compromised card numbers associated with that BIN when they are found to be exposed, enabling organizations to take appropriate action before damages occur.
How Does Payment Card Information Become Compromised?
Payment card numbers can be compromised through a variety of methods, both online and offline. In many instances, data breaches at merchants, financial institutions, or third-party service providers expose large volumes of cardholder data to unauthorized parties. Skimming devices installed on ATMs, gas pumps, or point-of-sale terminals are another common tactic, capturing a card’s information when it’s swiped or inserted. Phishing emails or malicious websites can also trick cardholders into revealing their sensitive data. Once compromised, these cards are typically offered for sale on the dark web or other cybercriminal marketplaces.
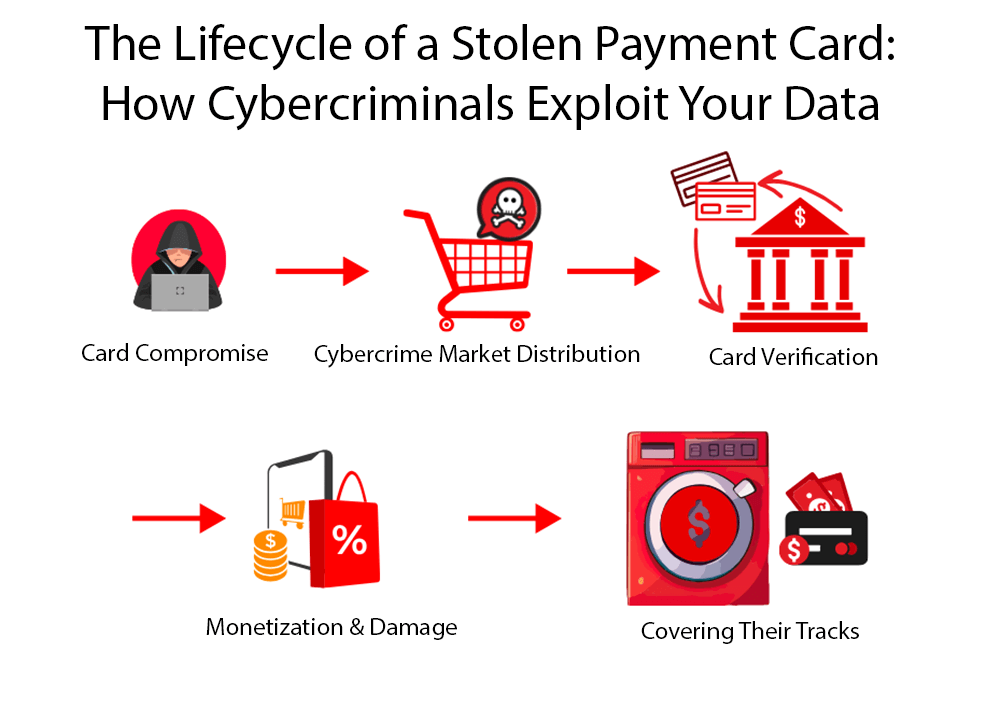
A stolen payment card typically follows a series of stages, beginning with the initial compromise and progressing as cybercriminals distribute the data on illicit markets. Once purchased, fraudsters verify the card details through test transactions before monetizing the stolen credentials through unauthorized purchases. The final step involves laundering the proceeds to conceal the original source of the funds. Recognizing this lifecycle is important for proactively protecting compromised cards instead of reacting only after damage has occurred.
How BIN Monitoring for Compromised Cards Works
Enzoic’s BIN Monitoring for compromised cards is powered by Enzoic’s threat intelligence database which actively searches for full card numbers associated with an institution’s BIN on the dark web. When a match is detected, organizations receive real-time alerts, allowing them to assess the risk and remediate it. This proactive approach helps financial institutions prevent fraudulent transactions before they occur, enabling them to quickly assess risk and initiate remediation.
Enzoic’s proprietary threat intelligence continuously scans the dark web, illicit marketplaces, and cybercriminal forums for full compromised card numbers and other associated data. By detecting compromised cards early, financial institutions can take preventative steps such as issuing new cards, implementing additional authentication measures, and enhancing fraud detection protocols. This ensures that financial institutions can stop fraud before it impacts their bottom line.
The Cost of Inaction and Why Enzoic Stands Out
Ignoring payment card security exposes financial institutions to substantial losses. The estimated cost per compromised card is $2,500, and large-scale card compromises can impact thousands of accounts within hours. The cost of a compromised payment card extends beyond the fraudulent charge, encompassing reputational damage, lost customers, and support personnel time. Implementing BIN Monitoring for compromised cards provides a cost-effective, proactive solution to mitigate this risk and prevent damages before it escalates.
Unlike other card monitoring solutions which only provide older data with infrequent updates, Enzoic’s BIN Monitoring for compromised cards leverages a continuously updated database of compromised payment card information sourced from both high-profile and smaller, under-the-radar data breaches. This ensures financial institutions aren’t left in the dark when lesser-known data leaks occur.
Central to Enzoic’s approach is the combination of automated scanning tools and dedicated human expertise. Our proprietary technology collects and processes vast quantities of compromised card data from the open internet, dark web, and private sources, while our in-house threat research team validates, refines, and organizes the findings.
Monitor BINs Without Providing Full Card Details
One of the biggest advantages of Enzoic’s BIN Monitoring is its simplicity and focus on security. Financial institutions only need to provide the first six to eight digits (the BIN) for the cards they want to monitor, meaning no sensitive cardholder information or full card details are shared. Once these BINs are in our system, Enzoic continuously tracks and identifies any compromised card numbers tied to those BINs. If exposed cards are detected, you’ll receive immediate alerts sent securely, allowing you to take prompt action, such as reissuing cards or stopping fraudulent transactions, without ever having to transmit or store full card data.
Take Action Today
Financial fraud is evolving, but so are the tools to combat it. Enzoic’s BIN Monitoring for compromised cards offers a powerful, automated solution to protect financial institutions from fraud, chargebacks, and reputational damage. Contact us today to learn how we can help protect your organization from card-related fraud risks.
Frequently Asked Questions
- What is BIN Monitoring, and why is it important for financial institutions?
Enzoic’s BIN Monitoring is a proactive fraud prevention solution that tracks payment card numbers associated with a financial institution’s Bank Identification Number (BIN) to detect compromised cards. By continuously scanning the dark web and illicit marketplaces, BIN Monitoring enables banks and credit unions to identify exposed card data early, take preemptive action, and prevent fraud before it impacts customers. - How do fraudsters obtain and sell compromised card numbers on the Dark Web?
Card numbers can be compromised through data breaches, skimming devices, phishing scams, and malware attacks. Once stolen, these details are often sold or traded on the dark web, allowing cybercriminals to conduct fraudulent transactions or resell card data in bulk. BIN Monitoring helps financial institutions stay ahead of these threats by identifying compromised card numbers as soon as they appear in underground markets. - Can Enzoic’s Credit Card and BIN Monitoring service be integrated with existing security or operational infrastructure?
Absolutely. Enzoic designed this service for flexibility and can seamlessly integrate into new or existing workflows, including SIEMs, card management, customer communication management, and even proprietary systems. This ensures minimal resource demands and allows for easy implementation within your existing security infrastructure. - How can financial institutions respond when a compromised card is detected?
Upon receiving an alert from Enzoic’s BIN Monitoring service, financial institutions can take several actions to prevent fraud, including:- Blocking or reissuing the compromised card
- Enhancing authentication and transaction monitoring for affected accounts
- Notifying customers about potential risks and advising security best practices
- Updating fraud detection systems to recognize patterns of BIN-related attacks
AUTHOR
 Josh Parsons
Josh Parsons
Josh is the Product Manager at Enzoic, where he leads the development and execution of strategies to bring innovative threat intelligence solutions to market. Outside of work, he can be found at the nearest bookstore or exploring the city’s local coffee scene.
*** This is a Security Bloggers Network syndicated blog from Blog | Enzoic authored by Enzoic. Read the original post at: https://www.enzoic.com/blog/unlocking-the-power-of-bin-monitoring-for-compromised-cards/



