Threats, Vulnerabilities, and Risks
As a business owner or employee in the UK, it’s important to have a comprehensive understanding of the cyber threats, vulnerabilities, and risks that can impact your organisation. The purpose of this blog is to give you a good understanding of what threats, vulnerabilities, and risks are and how they interact so that you can calculate the best course of action to take to limit any negative impacts on your organisation.
Cyber Threats:
A cyber threat is any event that could compromise a computer system, service, or network. These threats can be natural (e.g., floods or hurricanes), unintentional (e.g., human error), or intentional (e.g., hacking attempts). Threats are not always obvious, and it is important to remember them as actual events rather than people or things. These may be referred to as threat actors and are usually the origin or creator of threats.
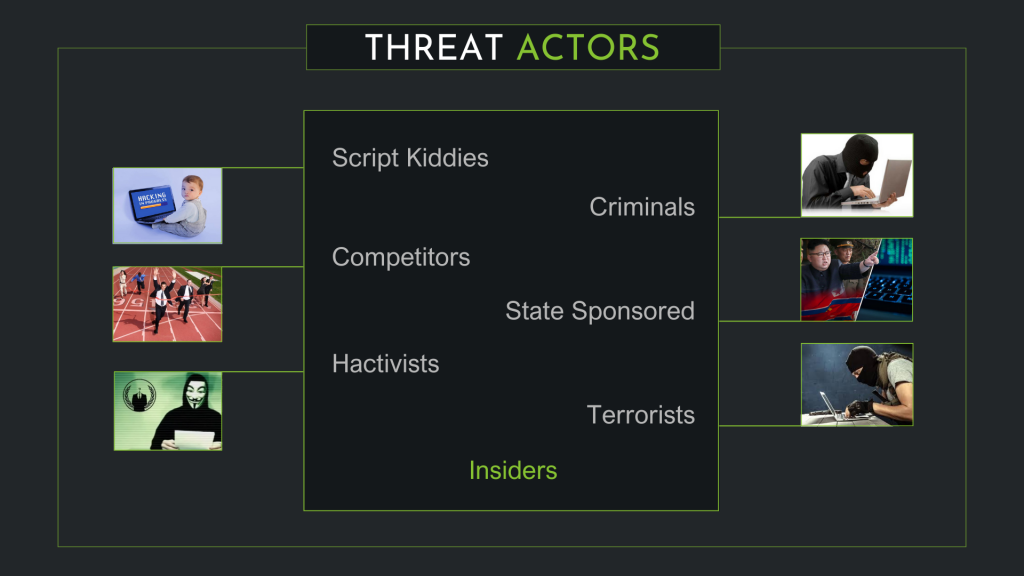
Threat Actors:
These are individuals or groups responsible for creating cyber threats. They can range from inexperienced “Script Kiddies” to professional hackers, competitors, state-sponsored Advanced Persistent Threats (APTs), hacktivists, terrorists, and even disgruntled insiders.
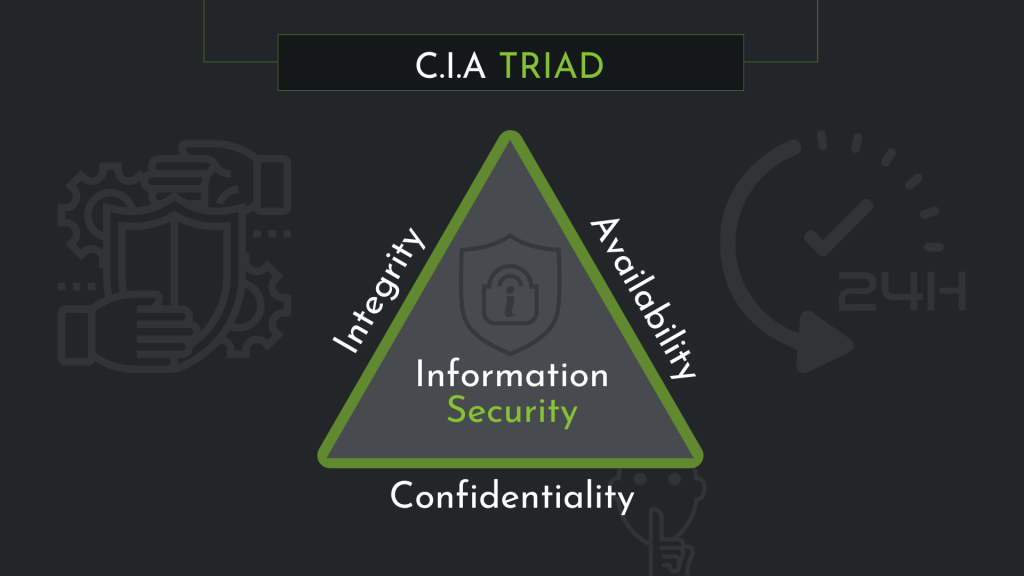
Confidentiality, Integrity, and Availability (CIA) Triad:
This security model focuses on protecting sensitive information from unauthorised access (confidentiality), ensuring data is not accidentally or maliciously altered (integrity), and guaranteeing the availability of data when needed (availability).
Confidentiality: The ‘C’ focuses on preventing unauthorised access to this information, which can be achieved by implementing various security measures. Examples of these measures include access control lists, file and volume encryption, and setting appropriate permissions. By effectively managing confidentiality, businesses can ensure that only authorised individuals have access to sensitive data, minimising the risk of data breaches or leaks.
Integrity: The second component of the CIA Triad, integrity, is concerned with preserving the accuracy and reliability of data. This involves protecting information from being altered, deleted, or tampered with by unauthorised users. Additionally, integrity measures help to ensure that any accidental changes made by authorised users can be reversed. Common techniques for maintaining data integrity include hashing, digital signatures, and implementing robust access controls. By upholding data integrity, businesses can maintain the trust of their clients and stakeholders in the accuracy and reliability of their information.
Availability: Finally, the last element of the CIA Triad is availability. This component emphasises the importance of ensuring that data and systems are accessible when needed by authorised users. To guarantee availability, businesses must implement measures to protect their systems from downtime, whether due to technical failures, cyberattacks, or natural disasters. Such measures can include redundant systems, regular backups, and disaster recovery plans. By prioritising availability, businesses can continue to operate efficiently and reliably, even in the face of potential disruptions.
Vulnerabilities:
A security vulnerability is any weakness in an IT system, application, policy, or procedure that could allow a cyberattack to succeed. Vulnerabilities can also be either intentional or unintentional and, in some cases, automated, e.g., when hackers use bots. They could include outdated software, or a lack of software altogether, or even a simple physical vulnerability such as a door that has been left open. Within the context of IT security, vulnerabilities are known weaknesses. Therefore, knowing the factors that impact your vulnerability will help you to better understand your cybersecurity posture – and that is the overall state and strength of your cybersecurity efforts.
Risk:
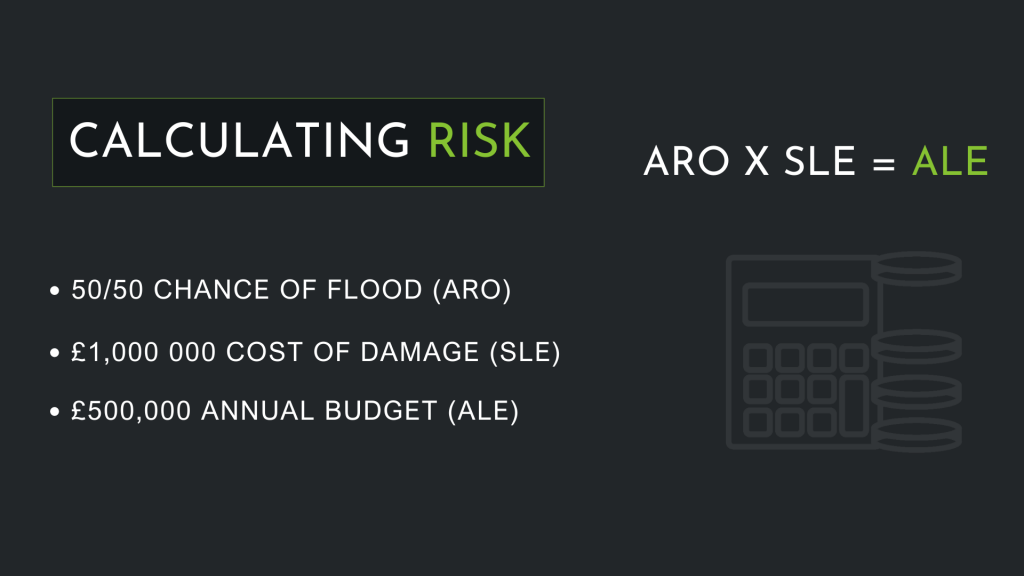
Risk is defined as the potential loss or harm related to technical infrastructure or the use of technology within an organisation and is calculated in a very specific way. There are three variables that we need to consider – the annual rate of occurrence or (ARO) – this is how often an event takes place within the space of a year. The Single Loss Expectancy (SLE) – what it will cost the business in a single event that the event takes place. And the Annual Loss expectancy – how much of a loss there will be from this event occurring over the course of the year.
Calculating and Mitigating Risk:
To determine the level of risk, multiply the ARO by the SLE. This will give you the ALE, which can then be used to decide what controls need to be implemented to mitigate the risk.
It’s essential to have a good understanding of cyber threats, vulnerabilities, and risks to protect your organisation against cybercrime. By staying informed about advancements in cybersecurity and implementing appropriate risk mitigation measures, you can contribute to the growth and security of your business as we accelerate into the future.
The post Threats, Vulnerabilities, and Risks appeared first on Penetration Testing UK – Sencode.
*** This is a Security Bloggers Network syndicated blog from Blog - Penetration Testing UK - Sencode authored by SencodeTeam. Read the original post at: https://sencode.co.uk/threats-vulnerabilities-and-risks/





