How Silverfort Protects Against the Risk from Shadow Admins
Shadow admins are one of the key attack surfaces that adversaries regularly take advantage of. The pattern of discovering a user who has been inadvertently assigned high access privileges is all-too-common in today’s cyber operations. This makes the ability to detect and prevent the abuse of these accounts a top priority for both identity and SecOps teams. In this article we’ll explain in detail how Silverfort’s Identity Threat and Detection (ITDR) capabilities enable the quick discovery of existing shadow admin accounts, the ability to monitor for new ones as they appear, and the securing of their access with MFA policies.
Shadow admins recap: what they are and what risks they introduce
Shadow admins are user accounts that either have admin access or have a way to achieve it while not actually being part of a documented admin group. As such, neither Identity nor Security teams are aware of their existence, and therefore don’t apply to them the standard monitoring and protection that admin accounts all require.
The most common example of this are user accounts that have the privilege of resetting the password of admin users. If adversary gains control of this type of account, they will then be able to use it to reset the passwords of admins and abuse the accompanying high level of privilege to access resources at will.
For a detailed explanation of shadow admins, read this article.
Silverfort shadow admin protection overview
Silverfort enables Identity and SecOps teams to easily discover shadow admins in their environments and either delete them or remove their redundant permissions. In addition, teams have the ability to continuously monitor for the emergence of new shadow admin accounts as well as take proactive protection steps against the attempt of any shadow admin account to gain access to a specific resource, including going as granular as enforcing MFA policies on password reset attempts for shadow admins.
These protections are equally effective both for accounts that were inadvertently assigned higher privilege access, as well as against any account manipulation that adversaries might perform that includes modification of the account’s original permissions and privileges.
Let’s see exactly how this is done in Silverfort’s console:
Discovery and removal of shadow admins
Purpose: eliminate all present shadow admins
In Silverfort’s Threat Detection screen, under the Attack Surface Management section, search for Shadow Admins. In this example there are two of these.
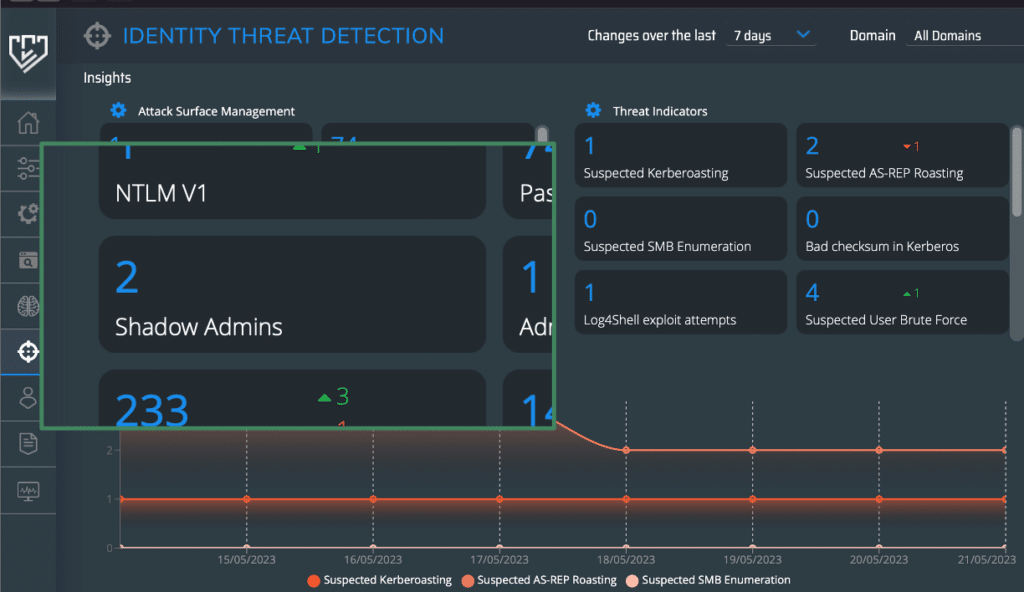
Clicking on the Shadow Admins space opens a window that shows you full details on these accounts.
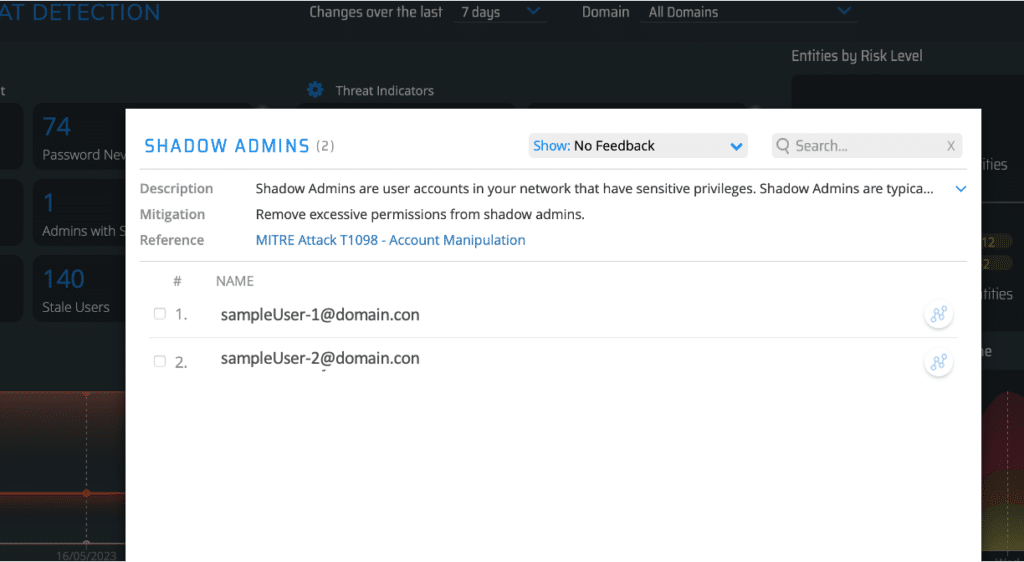
Now that that we have the names of these shadow admins, we can locate them in Active Directory and either remove their extra permissions or delete them altogether.
Continuous monitoring of shadow admins
Purpose: detect new shadow admins as soon as they appear
On Silverfort’s Authentication Logs screen, add a Risk Indicator filter and check Shadow Admins.
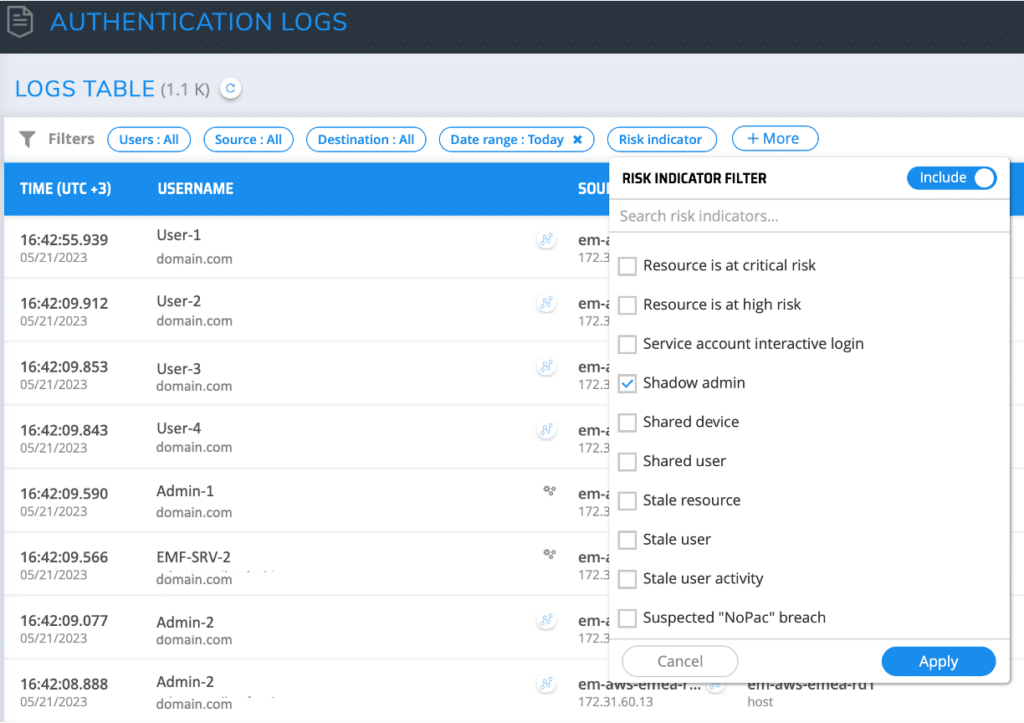
Click Apply and then adjust the time range to fit your monitoring cadence. This will show you all shadow admins that have been added to the environment within this timeframe.
Screen shot #4: discovering newly created shadow admins
Following the discovery, you can click the investigation icon of each account to see exactly which resources it has attempted to access since being created.
Screen shot #5: investigating shadow account’s activity
Next, you can proceed to either delete the account or downgrade its permissions, similar to what’s been described in the section on discovery and removal of shadow admins.
Risk prevention #1: MFA on all shadow admin access
Purpose: prevent shadow admins from connecting to resources without explicit user verification
On Silverfort’s Policies screen, create a new policy. Check Active Directory as the Auth Type
and then check either Kerberos/NTLM or LDAP, depending on your needs (or if both are required then create two policies). Choose Risk Based for the policy type and have it triggered by Risk Indicator. In the Risk Indicators box check Shadow Admin.
Screen shot #6: MFA policy to prevent shadow admins’ access
Once enabled, this policy will enforce MFA verification of any account that Silverfort’s risk engine identifies as a shadow admin. If this account were to become compromised, this policy will deprive an adversary of the ability to use this account for malicious access.
Silverfort is the only solution that can extend MFA protection to this type of authentication.
Risk prevention #2: MFA on shadow admin password reset attempt
Purpose: Prevent adversaries from using a shadow admins to reset the password of other accounts.
As mentioned earlier, the use of a shadow admin to reset the password of additional admin accounts with higher access privileges is common tactic of threat actors.
Silverfort enables users to mitigate this risk in the following way:
In Silverfort’s Policies screen, create a new policy. Check Active Directory as the Auth Type,
then check Kerberos/NTLM,choose Risk Based as the policy type, then check the Shadow Admin risk indicator.
In the Destination field, instead of placing names or groups of machines as in the former policy, choose krbtgt. This will apply the policy to any access attempt to the krbtgt account within the domain controllers in the environment.
Screen shot #7: MFA policy for shadow admin password reset – choosing krbtgt as destination
After choosing krbtgt as the destination, click on it to display the list of services. Check the kadmin/changepw and leave the others blank. (This is the service that performs the password reset.)
Screen shot 8: MFA policy for shadow admin password reset – choosing kadmin/changepw as destination
Enabling the policy will now trigger an MFA whenever any account Silverfort has marked as a shadow admin attempts to reset another account’s password — fully mitigating this risk.
Silverfort is the only solution that can extend MFA protection to this type of authentication.
Automated discovery and real-time protection are the keys to mitigating the risk of shadow admins
Silverfort’s protection against the malicious use of shadow admins is part of its vision of how Identity protection should be designed and practiced. Silverfort is the first solution that provides end-to-end ITDR capabilities across Active Directory environments. By applying continuous monitoring, risk analysis, and active policy enforcement on every authentication and access attempt, Silverfort can both automate the discovery of shadow admins as well as deliver real-time protection against their abuse.
Looking to solve shadow admin challenges in your environment? Reach out to one of our experts here.
The post How Silverfort Protects Against the Risk from Shadow Admins appeared first on Silverfort.
*** This is a Security Bloggers Network syndicated blog from Blog - Silverfort authored by Yiftach Keshet. Read the original post at: https://www.silverfort.com/blog/how-silverfort-protects-against-the-risk-from-shadow-admins/





