2023 State of the Threat for Financial Services and Banks
Arkose Labs’ extensive analysis in 2022 delved into current threats across various industries, revealing the frequency and types of attacks that plague today’s landscape. Explore valuable insights on emerging threats for financial services and banks, and gain access to recommended best practices for a more secure future.
In the rapidly evolving landscape of financial services, fintechs and online banks are facing a growing number of threats that could compromise their security and disrupt their operations. From cyberattacks and data breaches to regulatory compliance and customer trust, these threats pose significant risks to the stability and longevity of financial institutions.
Fintechs and online banks are particularly vulnerable to cyber threats due to their reliance on digital systems and networks. Further, they are a high value target for scammers, as an account takeover can bring in hefty dollars for a scammer. Both financial models must constantly stay up to date with the latest cybersecurity measures to protect their systems and sensitive customer data from hackers and other malicious actors.
Identifying Threats in Financial Services
Arkose Labs collaborates with a vast global network of customers, using anonymized threat intelligence sourced from over 4.1 billion IP addresses annually to fight cyberattack. From the outset, Arkose Labs provides an extensive database of more than 4,000 characteristic patterns of fraudulent activities.
After scrutinizing billions of sessions conducted by some of the globe’s most prominent corporations between January 1, 2022, and December 31, 2022, we found an onslaught of potential threats. Our report on the state of threats highlights these dangers and offers insights into the sectors that are most targeted by today’s threat actors and bot attacks.
Leveraging data-driven insights from the Arkose Labs Global Network , we aim to identify key trends in cybercrime and online fraud faced by banks, fintechs, and other institutions today and, more importantly, find ways for financial services to overcome them.
, we aim to identify key trends in cybercrime and online fraud faced by banks, fintechs, and other institutions today and, more importantly, find ways for financial services to overcome them.
To learn more, download our new eBook:
Suspicious Traffic Plagues Finance
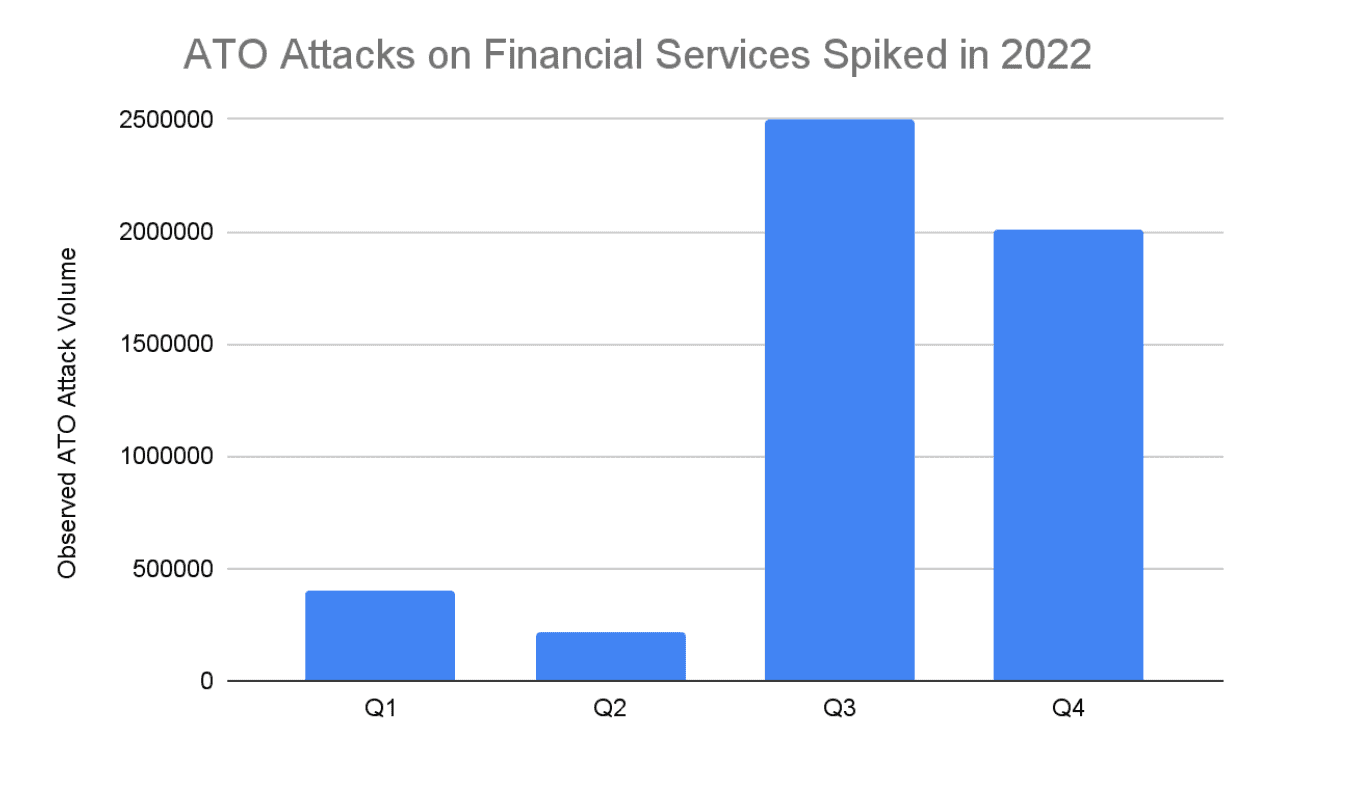
In 2022, the finance sector witnessed a considerable upsurge in suspicious traffic rates. Although fintechs and banks were hit with an onslaught of attacks orchestrated by human fraud farms during Q3 and Q4, which accounted for over twice the volume of attacks seen in Q1 and Q2, the real increase came from a 3.5x surge in automated attacks between the first and second half of the year. These alarming statistics highlight the pressing need for robust and innovative measures to counteract these threats, which continue to evolve in complexity and sophistication.
Our threat research team has been monitoring the financial services sector and uncovered a concerning trend—account takeover (ATO) attacks have become increasingly prevalent. In fact, one out of two attack attempts observed by our team were related to ATO threats. Unauthorized access to a bank account can lead to significant financial loss for the victim, including theft of funds, fraudulent transactions, and unauthorized access to personal information. The actual value of the account takeover will depend on factors such as the account balance, available credit, and any additional linked accounts or financial instruments.
To make matters worse, our team discovered that the frequency of ATO attacks had been on the rise in the financial services sector. Some reasons why include:
Increased value of financial data: The financial services sector holds vast amounts of valuable financial data, including bank account information, credit card details, and personal identification data. This information has become increasingly valuable on the black market, attracting cybercriminals who seek to profit from unauthorized access to bank accounts. As the value of financial data rises, so does the frequency of ATO attacks targeting the financial services sector.
Advancements in hacking techniques: Cybercriminals are continually evolving their tactics and techniques to bypass security measures and gain unauthorized access to bank accounts. They leverage advanced hacking tools, exploit software vulnerabilities, and employ social engineering methods to trick individuals into revealing their login credentials. The constant development and availability of hacking resources contribute to the rising frequency of ATO attacks in the financial services sector.
Global interconnectedness and digitalization: The financial services sector operates within a globally interconnected network, facilitating seamless transactions and account access across borders. While this digitalization brings convenience and efficiency, it also presents opportunities for cybercriminals to exploit vulnerabilities. With the increasing number of online banking platforms, mobile payment systems, and digital wallets, the attack surface for ATO attacks expands, leading to a higher frequency of such attacks in the financial services sector.
The rise in attacks shows that it’s important for the industry to stay alert and take action to protect against these threats. This includes implementing strong authentication and identity verification measures.
Automated Attacks vs. Human Fraud Farms
Automated attacks on businesses are not the same as human-driven fraud. While automated attacks are carried out using automated tools, scripts, and bots, human fraud farms involve groups of individuals working together to create and launch various types of online attacks.
Automated attacks are typically conducted by malicious actors who use software programs to exploit system vulnerabilities, steal data, or carry out other malicious activities without human intervention. Examples of automated attacks include malware infections, DDoS attacks, and automated phishing campaigns. These types of attacks can be launched on a large scale and can be executed rapidly, making them particularly effective at causing widespread damage.
Human fraud farms can comprise dozens or even hundreds of people who are hired by criminal organizations to carry out a range of fraudulent activities, such as creating fake social media profiles, posting fake reviews, engaging in click fraud, or carrying out phishing attacks.
Fraud farms often operate like sweatshops, with workers being paid low wages and forced to work long hours under oppressive conditions. Some workers may not even be aware that they are participating in illegal activities, as they may be misled into believing they are performing legitimate work.
Fraud Farms Are Major Threat to Financial Services Sector
When it comes to payment and monetization-related attacks, our research has shown that the vast majority of these attacks are not automated. In fact, only a minuscule portion of attacks in this category were carried out using automated methods.
Instead, the most prevalent type of attack in the financial category was human fraud farms. These attacks are often carried out by a group of individuals working together to conduct fraudulent activities, including account takeovers, fake purchases, and other forms of financial fraud. The popularity of human-led attacks in this area emphasizes the need for businesses to implement robust measures to detect and prevent such attacks, such as multi-factor authentication, behavior analysis, and other fraud detection mechanisms.
Financial Services vs. A Host of Attacks
Besides human fraud farms, several significant threats to financial services have come on the scene. Some of the biggest threats today include:
Phishing attacks: These attacks involve sending fraudulent emails or messages to individuals, tricking them into revealing their sensitive financial information or clicking on malicious links that can lead to malware infections.
Account takeover attacks: These attacks involve gaining unauthorized access to an individual’s account, usually through stolen or compromised login credentials, and carrying out fraudulent activities.
Malware attacks: These attacks involve infecting a user’s computer or device with malicious software that can steal sensitive financial information or carry out other malicious activities.
DDoS attacks: These attacks involve overwhelming a financial institution’s website or network with traffic, causing it to become unavailable to legitimate users and disrupting normal operations.
Insider threats: These threats involve malicious actions carried out by employees or contractors of financial institutions, such as stealing sensitive data or carrying out unauthorized transactions.
Third-party attacks: These attacks involve exploiting vulnerabilities in third-party service providers that financial institutions rely on, such as payment processors or cloud service providers.
Discover more about protecting financial services in the case study:
RECOMMENDED RESOURCE
Global Online Payment Company Achieves Significant Cost Savings with Arkose Labs
How to Protect Financial Services
There are several strategies that financial services can implement to guard against fraud farms and other online threats:
Multi-factor authentication: Requiring users to provide more than one form of identification, such as a password and a biometric identifier, can help prevent account takeover attacks and unauthorized access.
Real-time monitoring: Implementing real-time monitoring and alert systems can help detect and prevent fraudulent activities as they occur, allowing for rapid response and mitigation.
Behavioral analytics: Analyzing user behavior and identifying anomalies can help detect fraudulent activities, such as unusual login patterns or changes to account information.
Encryption: Implementing strong encryption measures can help protect sensitive data from being intercepted or stolen during transit.
Regular security training: Providing regular security training to employees and customers can help raise awareness of online threats and best practices for staying safe online.
Third-party risk management: Conducting regular security assessments of third-party service providers and ensuring they meet industry security standards can help prevent vulnerabilities that could be exploited by attackers.
Fraud intelligence and collaboration: Sharing threat intelligence and collaborating with other financial institutions and industry partners can help detect and prevent attacks and identify new emerging threats.
By implementing a comprehensive security strategy that includes these and other measures, financial services can better protect themselves and their customers from online threats, including fraud farms.
Arkose Labs Secures Financial Sector
The Arkose Labs platform offers customers in finance and fintechs a platform that uses a combination of advanced analytics and user engagement techniques to detect and prevent bot attacks and human fraud. It works by presenting users with interactive challenges from Arkose MatchKey that are designed to differentiate between human users and bots.
The challenges of Arkose MatchKey are based on a range of factors, including user behavior, device characteristics, and other contextual information. By analyzing how users interact with these challenges, the platform can accurately distinguish between real users and bots or fraudulent actors.
The platform also offers a range of other security features, such as device fingerprinting, IP reputation analysis, and behavioral biometrics. These techniques allow Arkose Labs to build a comprehensive profile of each user, enabling them to detect and prevent fraud and abuse in real-time. As a result, financial services businesses find a highly effective solution for protecting against bot attacks and human fraud, helping to safeguard their assets, reputation, and customers.
Find out how Arkose Labs protects finance and banks—book a demo.
*** This is a Security Bloggers Network syndicated blog from Arkose Labs authored by Jenn Jeffers. Read the original post at: https://www.arkoselabs.com/blog/2023-state-threat-financial-services-banks/