2023 State of the Threat for eCommerce and Travel
In 2022, Arkose Labs performed a comprehensive analysis of current threats across multiple industries to pinpoint the frequency and types of attacks in today’s landscape. Gain valuable insights into emerging threats for eCommerce and travel, including access to recommended best practices for a more secure future.
The eCommerce industry, including the travel sector, has seen explosive growth in recent years, with more and more consumers choosing to shop online for convenience and variety. But this growth comes with an increased risk of cyber threats and all around security issues. As the eCommerce industry continues to evolve and adapt to changing consumer demands, it is critical to stay vigilant in identifying and addressing potential threats—and to understand the current conditions of the threat landscape.
Our recent state of threat report highlights these emerging threats on a large scale and provides an overview of the shifting security landscape in the most targeted sectors. Here, we go one step further by offering data-driven insights from across the Arkose Labs Global Network to illustrate the specific concerns facing the world of eCommerce and travel today.
to illustrate the specific concerns facing the world of eCommerce and travel today.
Threat Landscape Shifts for eCommerce
Arkose Labs leverages anonymized threat intelligence from over 4.1B IP addresses across a vast global network of customers each year. From day one, Arkose Labs customers benefit from a database of over 4,000 tell-tale fraud patterns. By analyzing billions of sessions that occurred between Jan. 1, 2022 and Dec. 31, 2022 from some of the world’s largest companies, Arkose Labs discovered that over 10% of all sessions were deemed suspicious.
Further investigation was conducted on two distinct types of attack methods:
Automated attacks are a type of cyberattack carried out by bots, which are software applications programmed to perform specific tasks automatically. In the context of cyberattacks, bots can be used to execute various malicious activities, such as account takeover, credential stuffing, and DDoS attacks, among others.
These attacks are typically carried out on a large scale and can exploit vulnerabilities in the target system or application. Automated attacks are a growing concern for businesses and organizations across various industries, including eCommerce, finance, and healthcare, as they can result in significant financial losses, data breaches, and reputational damage.
Fraud farm attacks are a type of cyberattack that involve a network of human fraudsters who work together to carry out various fraudulent activities, often on a large scale. These attacks can target a range of industries, including eCommerce, banking, and finance, among others.
These attacks can be highly organized and sophisticated, with the fraudsters using a range of techniques to evade detection, including IP address spoofing and device fingerprinting. Fraud farm attacks can result in significant financial losses, data breaches, and reputational damage for businesses, highlighting the importance of implementing advanced security measures to protect against these threats.
ECommerce sites are particularly vulnerable to automated attacks, which can be carried out by bots seeking to exploit vulnerabilities in the site’s security infrastructure. Such attacks can result in a range of negative consequences for businesses, including financial losses, damage to reputation, and loss of customer trust. Common types of automated attacks on eCommerce sites include account takeover, card testing, and gift card fraud, all of which can be executed at scale using sophisticated automation tools.
Fraud Farms and Bot Attacks
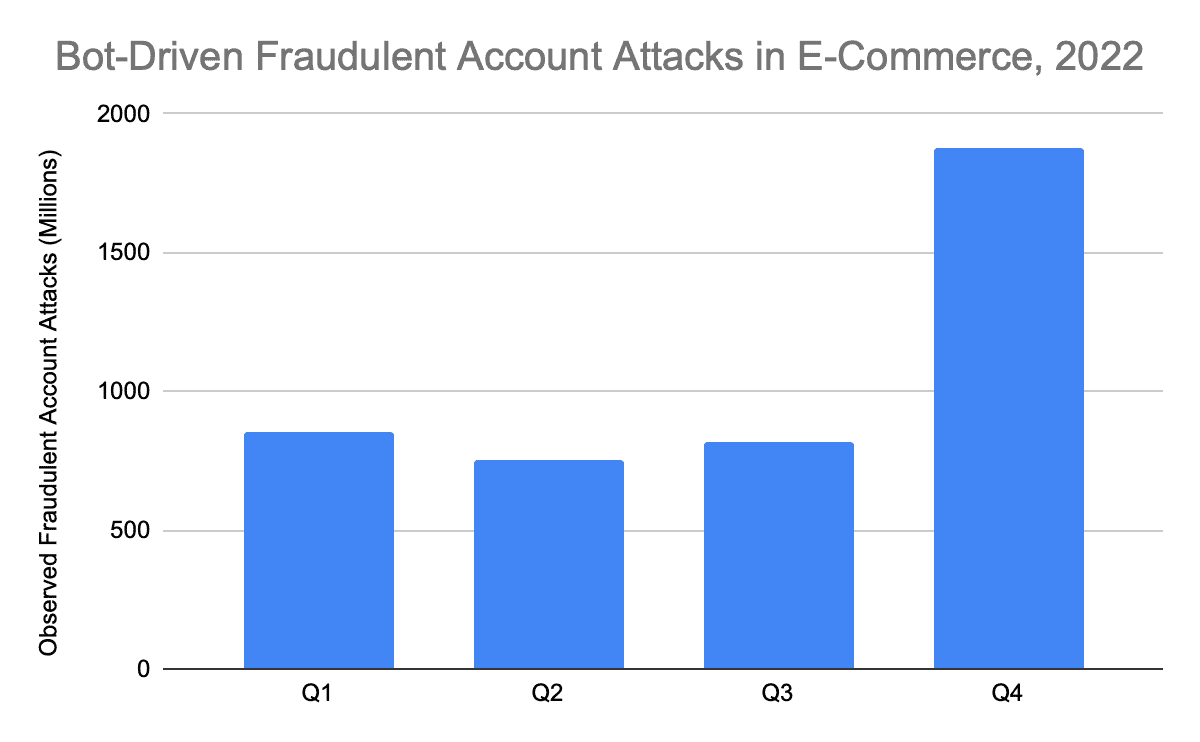
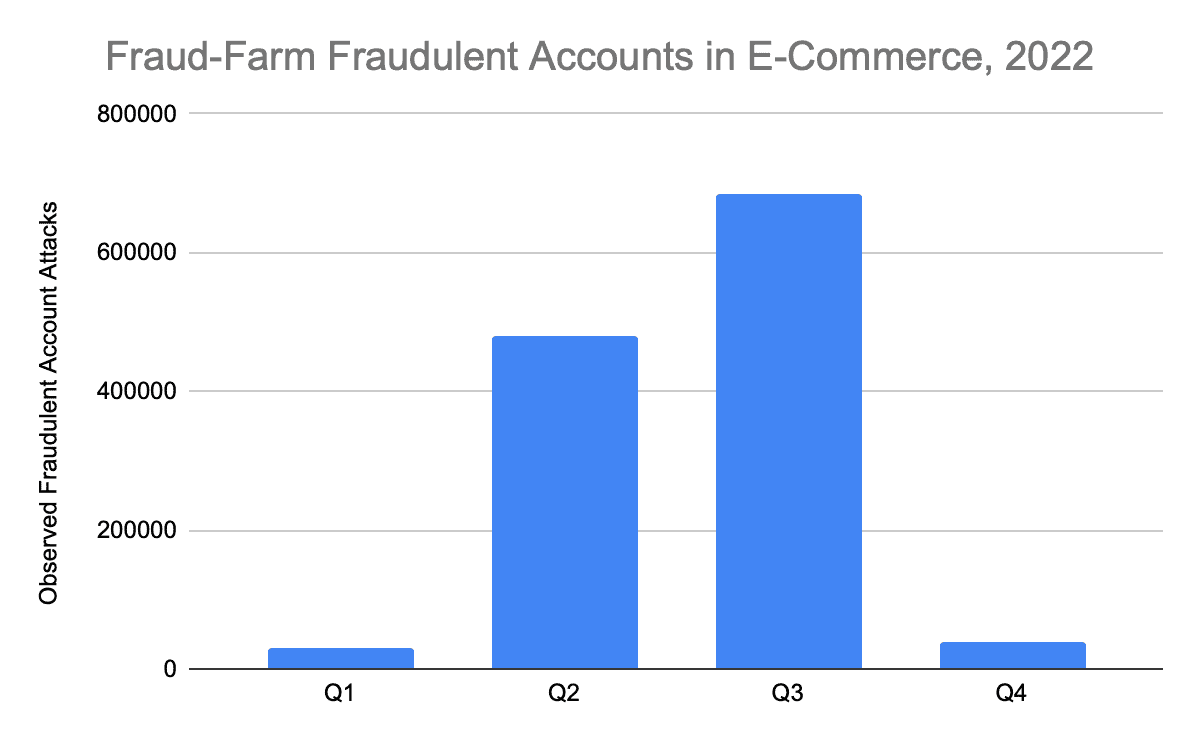
The eCommerce sector has faced increasing threats from cybercriminals in recent years, with the use of automated bot attacks and human fraud farms becoming more prevalent. According to our network research, there has been a notable shift in attack methods in the second half of last year. While the eCommerce sector saw a decline of 14% in automated bot attack volumes during H2, compared with H1, there was a significant surge in human fraud farm attacks, increasing by 44%. Although the overall scale of bot attacks outranks human attacks by many orders of magnitude (10,000x or more), these findings suggest that attackers situationally are adapting their strategies to overcome defensive measures and to exploit particular vulnerabilities in the eCommerce sector.
To protect organizations from these fraud farms and bot attacks, Arkose Labs employs a multifaceted defense approach. Our strategy includes risk-based authentication, utilizing factors like user behavior and device reputation to detect suspicious activity. Our platform implements adaptive challenges that differentiate humans from automated bots, creating friction in the authentication process. By maintaining a global threat intelligence system, Arkose Labs proactively identifies and mitigates emerging threats while leveraging machine learning and behavioral analysis to detect anomalies associated with fraud farms and bots. Through collaboration with other organizations, we share knowledge to stay ahead of evolving threats.
Fake Account Creation on the Rise
While there has been a notable shift in attack methods within the eCommerce sector in recent months, one particular type of attack has shown growth across both automated and fraud farm attacks in the second half of last year—fake account creation. In fact, an Arkose Labs’ customer in the travel sector recently reported fake accounts with fraudulent inventory can feasibly cost their business $75 to $100 per bogus account!
Cybercriminals target the travel sector due to its:
- high transaction volume
- valuable personal information collected from customers
- limited security measures compared to other sectors
- global reach and interconnectedness
- time-sensitive nature
Fake account creation is a type of cyberattack that involves creating fake user accounts on websites or applications with the intent of profiting by hoarding inventory and manipulating prices, creating fake reviews, and abusing promotional incentives. Additionally, cybercriminals use fake accounts to hijack site functionality to carry out malicious activities such as spamming, phishing, or spreading malware. Fake account creation attacks also can be used to carry out payment fraud or to make fraudulent purchases using stolen credentials.
These fake accounts can be created manually or by using automated tools, and they can be difficult to detect. Data from the Arkose Labs global intelligence network shows that bot-driven fraudulent account creation attacks are by far the larger threat. Bot-created accounts vastly outnumber those created by human fraud farms by a factor of 10,000x or more, and represent a more consistent attack vector.
According to Arkose Labs’ threat intelligence, fake account creation has increased in frequency during H2, bucking the overall trend of decreasing attack volumes on e-commerce sites. This finding highlights the importance of businesses remaining vigilant and proactive in their efforts to combat evolving cyber threats, including those targeting fake account creation, which can result in fraudulent purchases, stolen data, and reputational damage.
eCommerce Navigates Attack Traffic
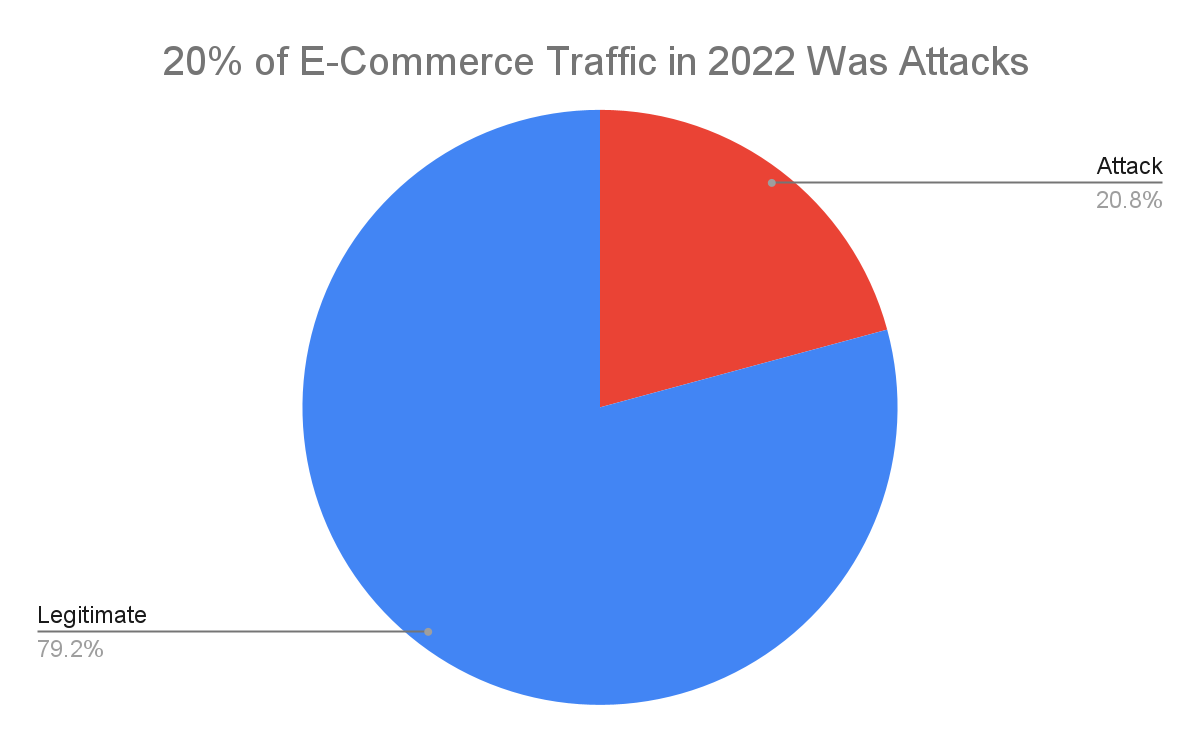
A particularly concerning finding from Arkose Labs’ research highlights that attack traffic has become a significant component of the overall traffic in the eCommerce market. This indicates that the volume of malicious activity targeting the sector has increased in line with its rapid growth.
To combat these threats, it is critical for businesses to prioritize the implementation of advanced security measures that can protect against a wide range of threats, including DDoS attacks, data breaches, and payment fraud. Good cybersecurity hygiene and protecting against this wide range of threats helps build a foundation that allows teams to better defend against the specific attacks discussed here, such as ATOs and fake account creation.
Neglecting to take adequate precautions can result in severe consequences, including significant financial losses, damage to reputation, and loss of customer trust, all of which can have long-lasting impacts for businesses operating in the eCommerce industry.
Interested in hearing more about how to protect eCommerce and travel businesses from cyberattack? Read our recent case study: Arkose Labs Enables eCommerce Giant to Stop New Account Fraud.
How to Protect eCommerce
Protecting eCommerce platforms from ATO attacks and fake account creation requires implementing robust security measures. Here are two key strategies to enhance security in eCommerce:
- Multi-factor authentication (MFA): Implementing MFA adds an extra layer of security by requiring users to provide additional credentials or verification factors during the authentication process. This can include one-time passwords (OTP) sent via SMS or email, biometric authentication, or hardware tokens. By utilizing MFA, even if an attacker manages to obtain a user’s password, they would still require the secondary authentication factor, making it significantly more difficult for them to gain unauthorized access to accounts.
- Robust user verification: Employing stringent user verification processes helps to prevent the creation of fake accounts. This can involve verifying user identities through methods like email or phone number verification, CAPTCHA challenges, or identity verification services. Additionally, implementing risk-based authentication can analyze user behavior, IP reputation, and other factors to identify suspicious account creation attempts. By validating the authenticity of user accounts during the registration process, e-commerce platforms can reduce the risk of fake accounts and deter malicious actors.
In addition to these measures, it is crucial to regularly update and patch e-commerce platforms, conduct security audits, employ encryption for sensitive data, educate users about strong password practices and phishing awareness, and implement robust fraud detection systems. By taking a proactive and comprehensive approach to security, e-commerce platforms can significantly reduce the risk of ATO attacks and fake account creation, enhancing customer trust and ensuring a secure online shopping experience.
Arkose Labs Safeguards eCommerce & Travel
At Arkose Labs, we prioritize long-term account protection and bot prevention for eCommerce and travel by disrupting the economic incentives driving cyberattacks. Our state-of-the-art AI platform is designed to thwart both persistent bot attacks and coordinated human threats that target critical user touch points on eCommerce websites and apps.
Arkose Bot Manager combines highly-transparent detection with targeted attack response to catch fraud early in the customer journey, without impacting good users. Our approach to detection involves multiple layers that combine real-time data from device, network, and behavioral signals, which are then analyzed to identify and prevent both bot and human-driven attacks.
The Arkose Labs’ platform uncovers hidden signs of fraudulent activity, including device and location spoofing, and takes appropriate action to protect against such threats. In addition, we have access to over 70 risk attributes that further enrich our existing models, and our machine learning decisioning process is driven by over 150 global attack signatures. Our 24/7 Security Operations Center (SOC) provides continuous threat analysis and tuning to ensure the highest level of protection for our customers.
Explore Bot Detection for Your Business!
With our invisible risk assessments, legitimate users can easily navigate through the system, while high-risk traffic is carefully evaluated and responded to using our innovative enforcement challenges. By doing so, we not only deter future attempts, but also provide a safer and more secure experience for genuine customers. Trust us to safeguard your online business and protect against emerging threats.
Find out how Arkose Labs can protect your eCommerce business today. Download our newest eBook, Bad Bots and Beyond: 2023 State of the Threat Report or book a demo!
*** This is a Security Bloggers Network syndicated blog from Arkose Labs authored by Ashish Jain. Read the original post at: https://www.arkoselabs.com/blog/2023-state-threat-ecommerce-travel/