The Anatomy of a Scalping Bot: NSB Was Copped!
In recent years, scalping bots have become a growing concern for online retailers. In this two-part blog series, we will analyze the inner workings of the Nike Shoe Bot (NSB) scalping bot, one of the most dangerous scalping bots around. We will take a closer look at the components of NSB, how we investigated the bot, its evasion techniques, and its unique features. Based on the analysis, we hope you’ll learn how to protect your business from this type of advanced bad bot.
In this post, we will present the bot and show how we deobfuscated its source code.
Scalping impact on eCommerce websites
Before we start, let’s talk about scalping in general.
Scalping is an automated threat, defined by the OWASP as “acquisition of goods or services using the application in a manner that a normal user would be unable to undertake manually.” Put simply, it is the use of bots to gain an unfair advantage over legitimate users and to acquire highly sought-after services or physical products. Concert and sporting event tickets, sneakers, limited edition and collectors’ items are just a few examples.
Why are bot operators motivated to acquire these goods and services? They want to sell them to the highest bidder at a significant markup.
While this might not sound harmful or threatening for a business, scalping bots have a detrimental effect on customer experience and a business’ bottom line. By automating the purchase of highly sought-after products, scalping bots make these items inaccessible to human users.
Below are just a few ways that bad bots can negatively impact businesses and consumers:
- Damaged brand reputation
- Loss of revenue
- Loss of brand loyalty
- Increased infrastructure costs
- Slower website speed
- Distorted web metrics
When successful, scalpers proudly share it on the Internet. Human users have become so frustrated with this unfair game that some are even seeking the assistance of scalper bots.
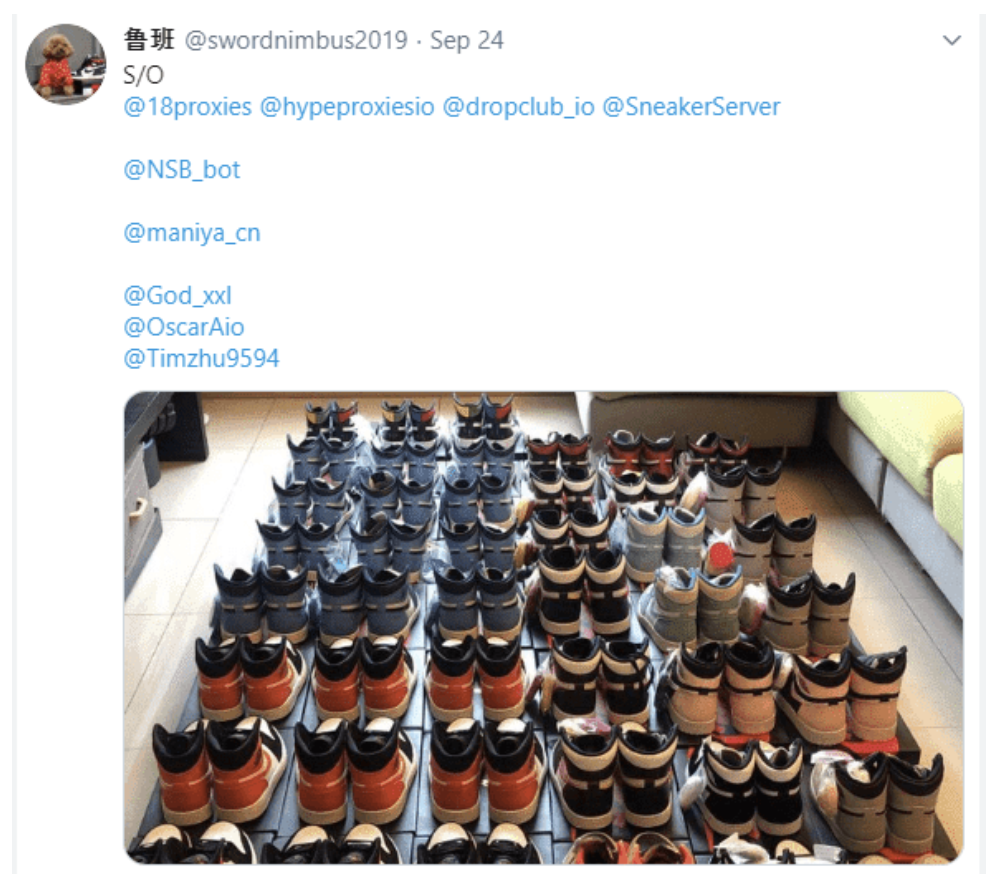
Example of user showing a shoes collection built on automation
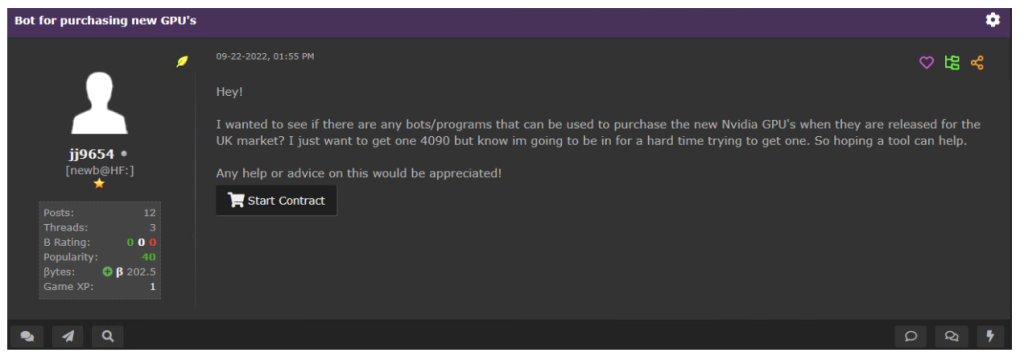
A member of a popular underground forum requesting service for scalping
For more information, read this article about scalping bots.
A leader in the sneaker bot market
For the past eight years, NSB has been used by bot operators to acquire limited edition and hard-to-find items from over 100 online shops. It has a reputation for successfully “copping” releases from Shopify, Nike, Footsites, Demandware, and Supreme. NSB is considered one of the best scalping bots available on the market, with an annual price of $499 for dedicated scalpers.
NSB components
NSB is composed of six components, organized in separate tabs.
- The “Tasks” dashboard shows the current tasks running in the bot. It can also be used to create new tasks. Monitors are additional windows aimed at creating an alert or triggering a purchase task whenever a new item matching a specific keyword appears in a shop.
- The “Proxies” dashboard can be used to add new proxies, an intermediate machine that can be used as a hop to hide one’s own identity.
- The “Billing” dashboard offers a list of billing information of the user that can be attached to any scalping task.
- The “CAPTCHA” dashboard manages third-party service anti-CAPTCHA keys. It gives users the ability to associate the bot with several Gmail accounts, enabling the bot to use them to solve CAPTCHA challenges. Behind the scenes, the bot uses Capmonster and can be integrated with AYCD Autosolve.
- The “Profile” dashboard contains generic information about the bot instance, like license key and bot version.
- The “Copped” tab is list of successful purchases made by the user.
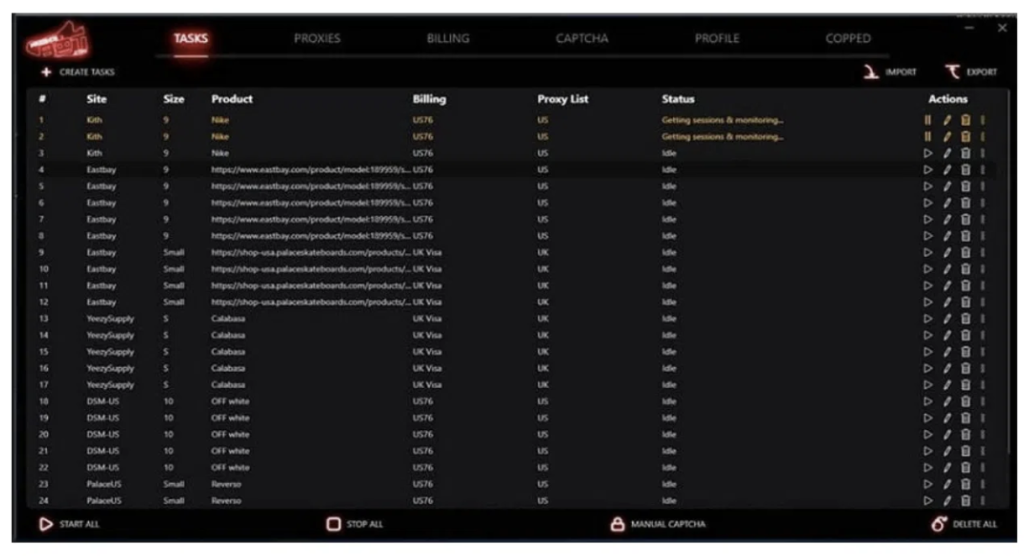
Task dashboard of NSB
Recovery of the source code
This bot is written in JavaScript with Electron framework. As such, it’s possible to extract the asar archive and recover the source code of the bot.
First layer of the folder structure of NSB
Main file deobfuscation
When viewed in a text editor, the contents of the main.js JavaScript file appear to be unreadable.
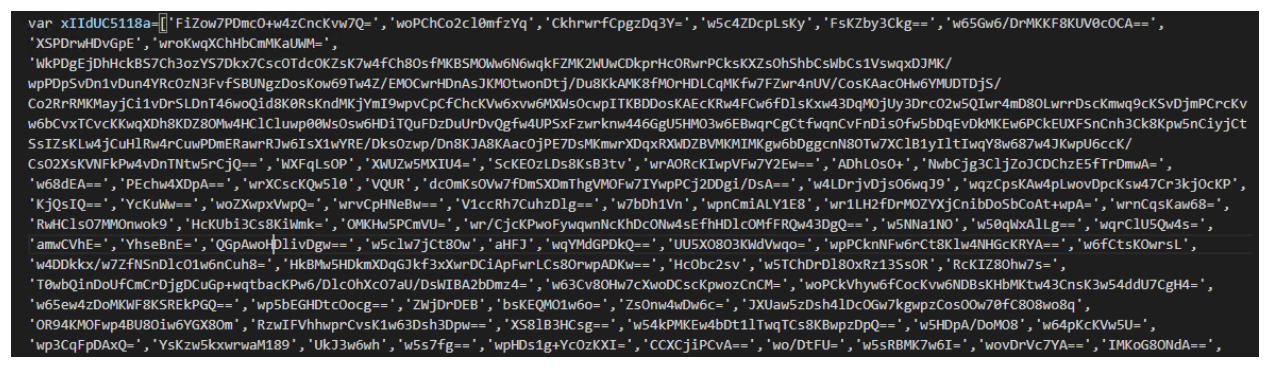
There is a lengthy array of base 64 encoded data at the start of the code. Upon further examination, it appears to be an array of encrypted strings. We will show later how to actually recover the clean strings.
The code looks like it was obfuscated with a tool similar to ObfuscatorIO. The first step I followed in the analysis of this code was to format it with a tool like js-beautify. Unfortunately, no online deobfuscation tool I tested were able to recover the source code.
I encountered the following error message when I tried to run my newly formatted code in the popular debugger, VSCode.
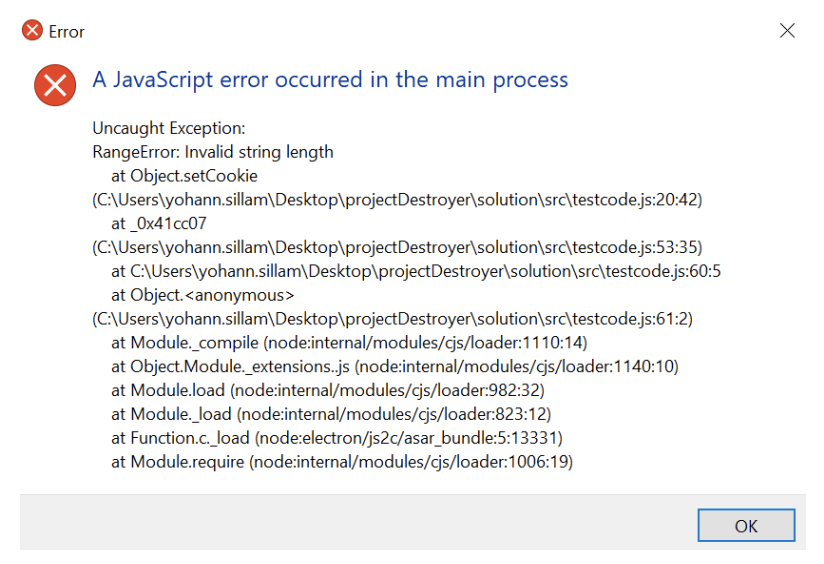
Something strange was going on here. Why couldn’t I debug the code?
This time, I started to debug the source code from the beginning by inserting breakpoints. I eventually reached the following line:

The code was filled with pieces of regular expressions like the one above.
Actually, there were others in the source code like the one below:

After spending more time debugging, I understood that the code was executing those regular expression patterns against the string representation of basic JavaScript objects.
For example, the first regular expression executed was the following:

This pattern was executed against the following string:

And if the code is beautified (like during manual analysis), the function code string representation turned into:

The test fails, the regex doesn’t match, and the flow is redirected to the below setCookie function, which is an infinite loop disguised.
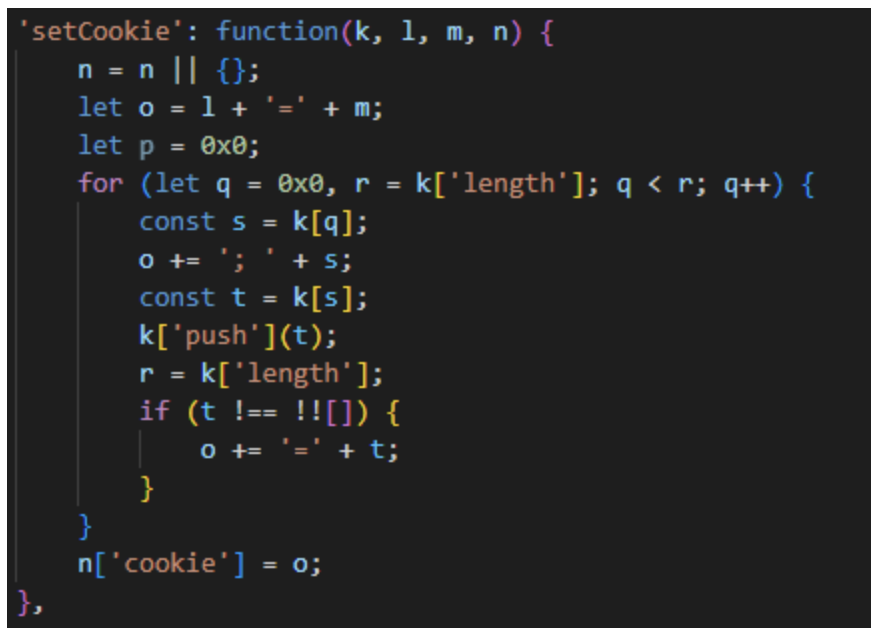
So, the code implemented an anti-debugging technique using regular expressions!
Below is a summary of each regular expression matched against a JavaScript object.

In addition to that, another regular expression was defined:

But, it was not used. This section of code was actually a feint to hide a mechanism to rotate the encrypted strings array via the following function:

Finally, by disabling the regular expression checks, I could debug the code without leading to a crash.
Apart from this anti-debugging feature came the string decryption procedure.
All strings from the code were replaced with the following pattern:

The first number corresponds to the index of the desired string in the rotated array of encrypted strings, and the second argument is the RC4 encryption key used for this specific string.
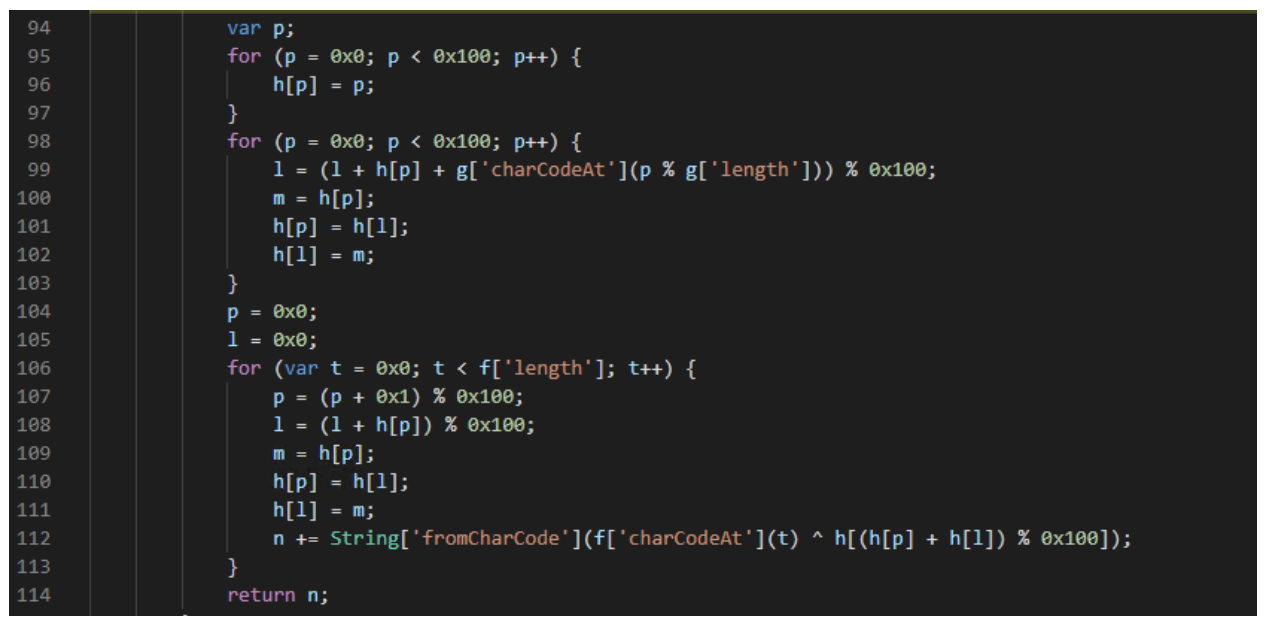
RC4 decryption section
Eventually, I was able to overcome the first obfuscation layer of the bot source code as you can see in the picture below:
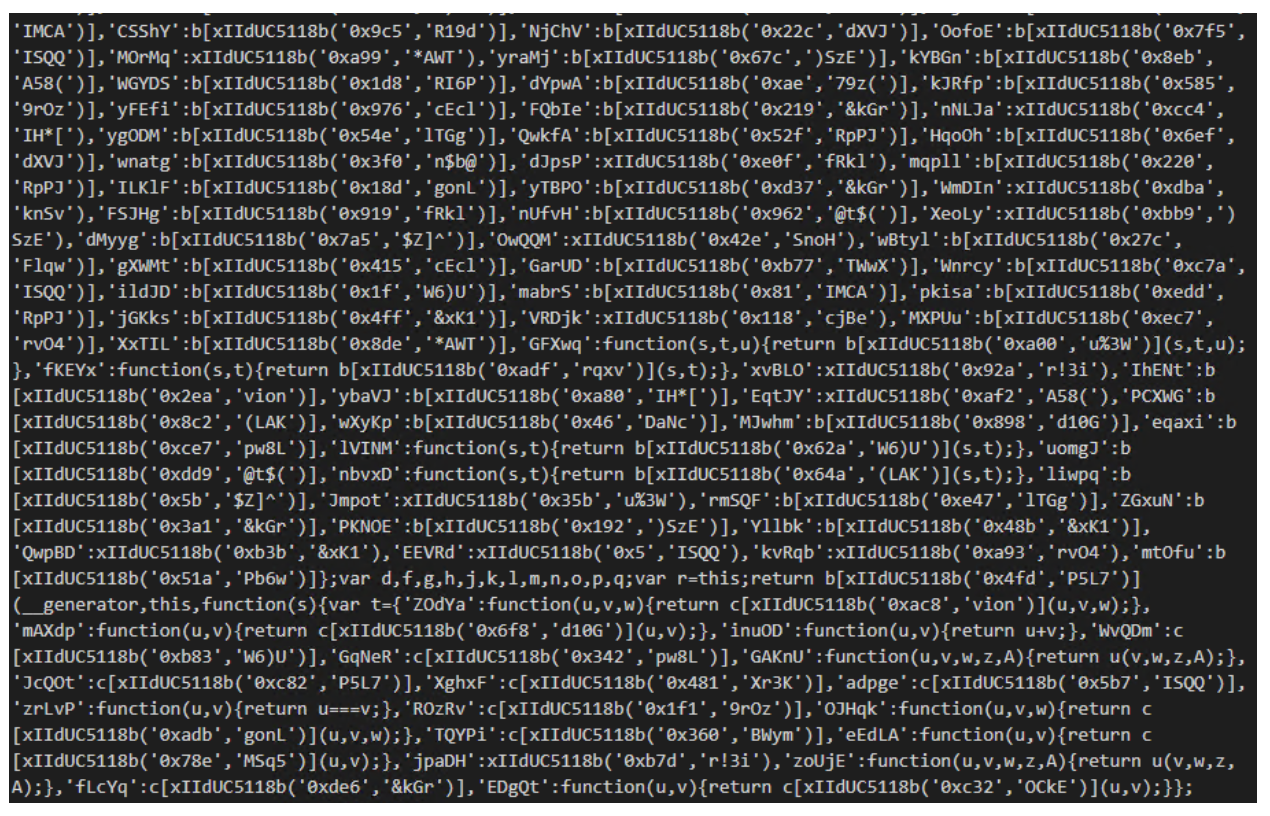
Source code of NSB before first layer deobfuscation
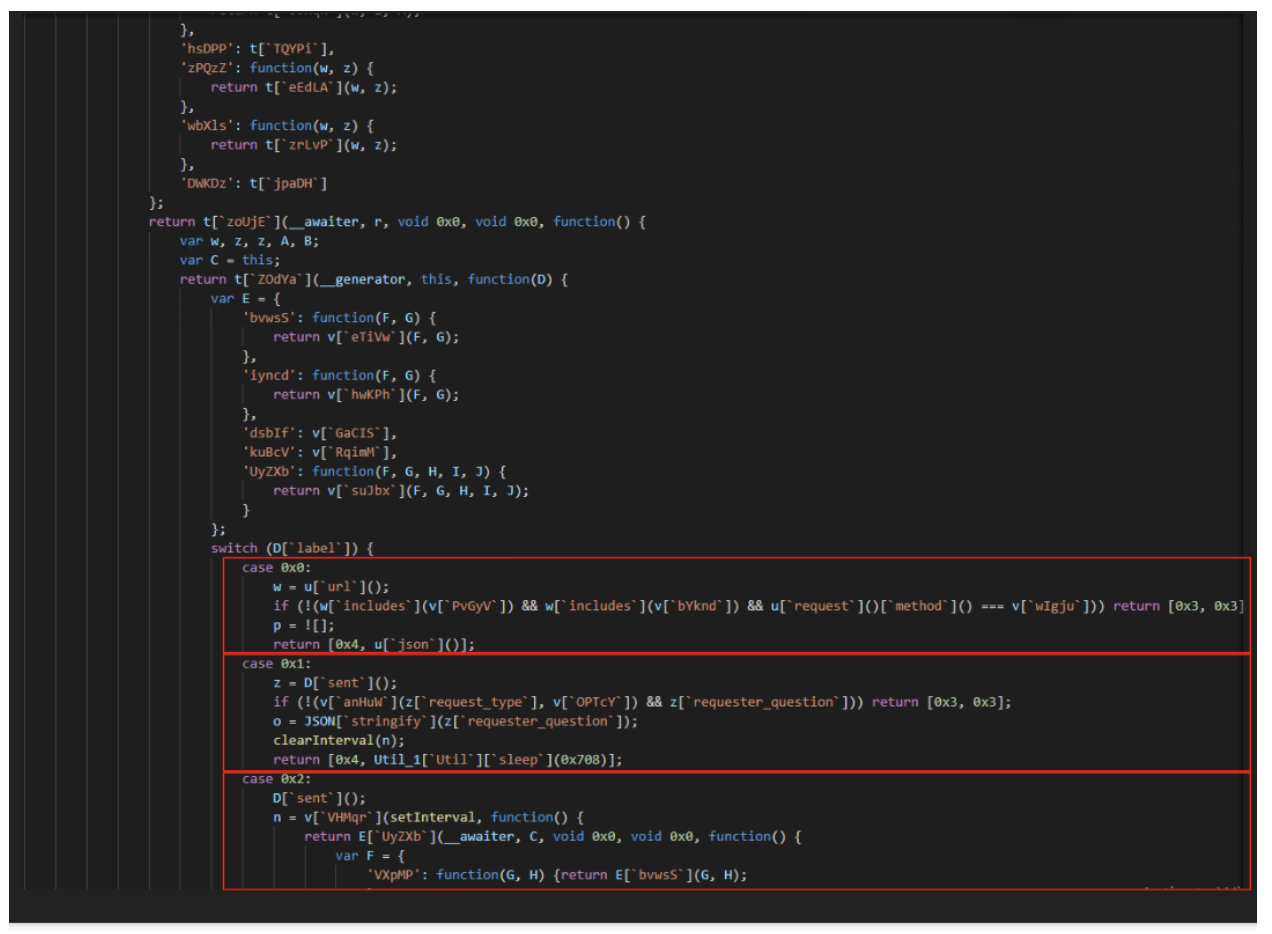
Source code of NSB after first layer deobfuscation
Because a second obfuscation layer was added, the obtained source code was composed of multiple blocks (highlighted in red) that still need to be reordered and the strings need to be replaced, but the hard work was done.
Finally, to finish the de-obfuscation, the blocks (see in red in the above picture) can be reordered according to the pipe separated string at the top of the function definition:
![NSB Blog Pt 1 - The variable a[‘VBjgk’] contains the right order of the blocks](https://www.imperva.com/blog/wp-content/uploads/sites/9/2023/04/Screen-Shot-2023-04-25-at-6.47.07-PM.png)
The variable a[‘VBjgk’] contains the right order of the blocks
After full de-obfuscation, this is how the above snippet of code looks like:
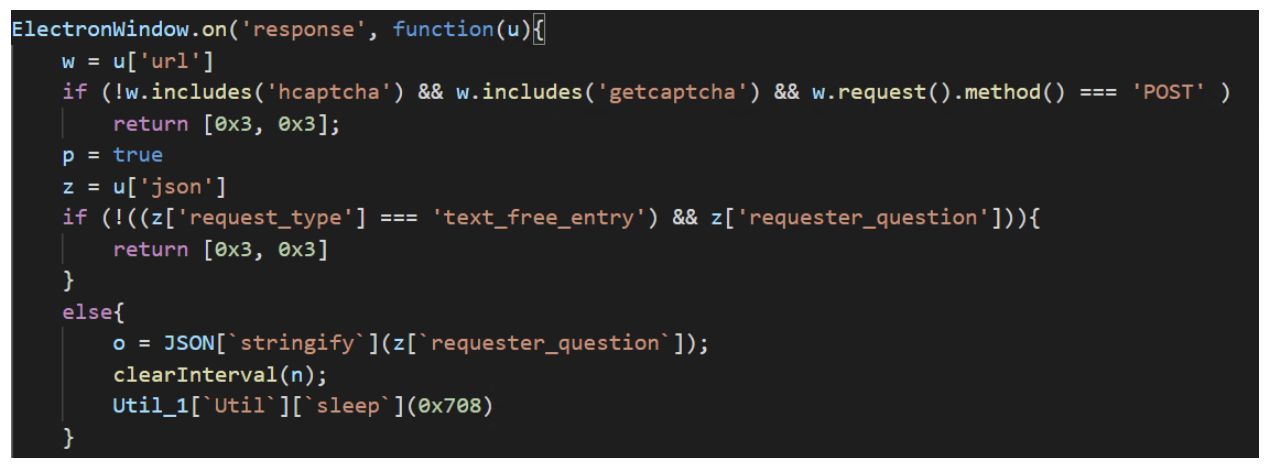

Snippet of code after complete deobfuscation
Conclusion
In this blog post, we examined NSB scalping bot, showed its main components, and had an interesting journey of JavaScript deobfuscation.
In the next blog post, we will go over what can be understood from this code and how the bot avoids detection.
The post The Anatomy of a Scalping Bot: NSB Was Copped! appeared first on Blog.
*** This is a Security Bloggers Network syndicated blog from Blog authored by Vitaly Simonovich. Read the original post at: https://www.imperva.com/blog/the-anatomy-of-a-scalping-bot-nsb-was-copped/





