Become a cloud security hero
On March 14, 2023, security expert, Nicolau Lawand, led a session discussing how Solvo helps organizations identify and mitigate cloud misconfigurations and vulnerabilities by providing contextual visibility into applications, user behavior, cloud infrastructure resources, and associated data.
We touched on a lot of great topics during the live session but there were still a lot of questions left to answer with little time to spare. So, we decided to put together a blog for easy consumption.
Also, for those who were unable to make it or had to leave early, you can directly access the recording by visiting our website resource center.
Enjoy!
Q: What is the difference between a solution that does CIEM like the AWS IAM Analyzer to verify resource accounts/entitlements versus Solvo’s solution?
A: AWS Access Analyzer builds IAM permissions templates based on Cloud Trail activity. It gives reliable suggestions only to the services they support, and the accuracy of the policy depends on available and granular logs. By design, this service will leave blank spots for the user to specify things like resource names. Solvo’s solution gives a granular security policy, including specifying the “blanks” that are left in the Access Analyzer results. This is an accurate, scalable end-to-end solution and fits better for organizations that are looking to reduce manual work.
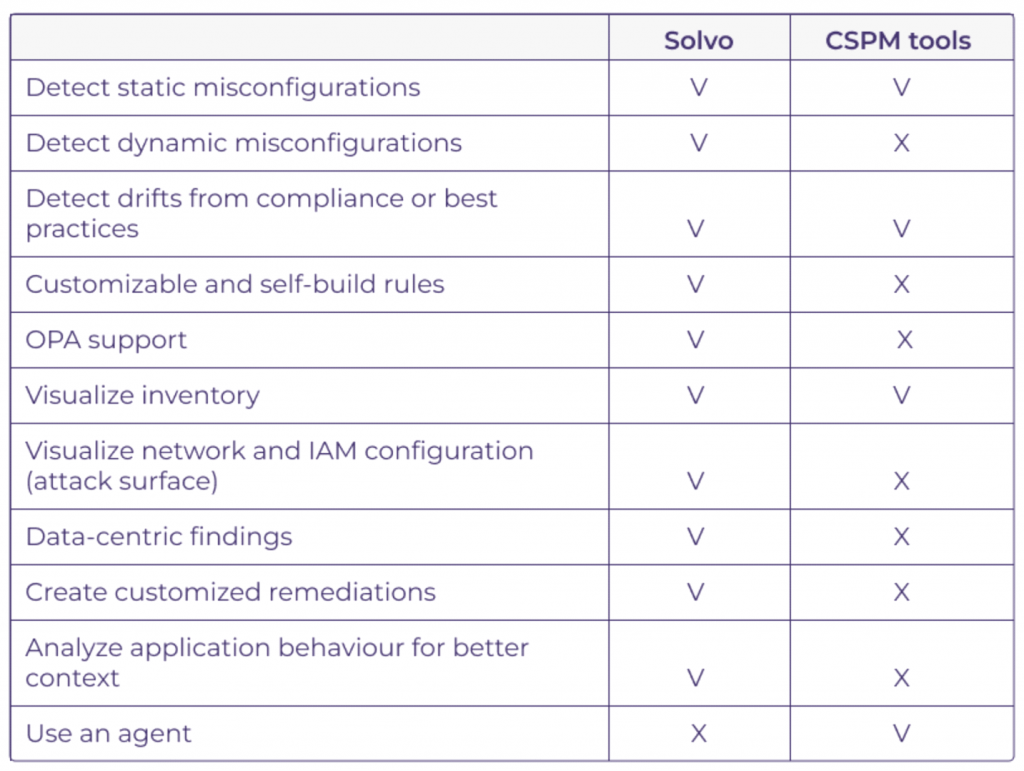
Q: What is the difference in the solution compared to other CSPM solutions on the market, such as Prisma from Palo Alto and Netskope, for example?
A: The differences are shown below. If we look at the core differences, these would be the application analysis provided by Solvo, along with the accurate remediation that saves time and reduces risks.
Q: Can the solution check for IAM accounts across account roles and across organizations of CSPs?
A: Absolutely, with the IAMagnifier you can review cross-account roles that have any kind of access to your account, understand what kind of access they have, and see for yourself if they need this access. In addition, in Solvo’s dashboard, you can review access granted to 3rd parties and time of last use, to make it easier for you to remove unnecessary access.
Q: What types of compliance reports does the solution deliver? Ex. CIS Controls, NIST CSF, among other frameworks?
A: Solvo supports CIS, GDPR, HIPAA, ISO 27001, SOC2, PCI-DSS, CCPA, and NIST 800-171. New frameworks are added weekly so make sure to check our Compliance Manager from time to time. Of course, in addition to that, we enable high flexibility in building your own rules using OPA, or import to Solvo other rules community members shared.
Q: Is it possible to apply the suggested policy in a simple way? Like a single click? Or is customization or approval in levels required?
A: Right now enforcement is enabled using Terraform, Cloud Formation, or CLI commands, and integrations with your CI/CD pipeline.
Q: Is it possible to check for weaknesses/vulnerabilities in CWPP workloads?
A: Solvo doesn’t scan for vulnerabilities itself. However, we provide integrations with other products and open source tools. If your organization already uses one of them, Solvo can utilize its findings and provide a comprehensive posture view along with remediation support.
Q: How is the solution supported? Are there already partners in other countries such as Brazil?
A: Solvo provides support via email and Slack channels to our customers, 24/7. To make our support more helpful to Brazilian customers, we partnered with local companies that help us deliver automated cloud security solutions, without the language barrier.
Q: Does the solution also address SSPM (SaaS Security Posture Management) or just the CSPM (Cloud Security Posture Management) part?
A: Solvo provides Solutions in the CIEM, CSPM, and CNAPP categories and delivers the most holistic solution for cloud-native applications. We currently don’t provide SaaS security solutions.
Q: Does the solution address the Cloud Miter Framework to learn the types of attacks and forms of defense that the solution helps to mitigate?
A: Yes, we mapped the MITRE attack framework to cloud-related vectors and the related security permissions that could enable these vectors. This information is available in our console.
Q: Does it scan and sort this data? If yes, how? Or is this just done manually?
A: Solvo discovers data resources, analyzes their security permissions, and creates the context of these resources as part of the cloud application. Then, Solvo builds a bigger picture around these resources, understanding the security posture of the data resources, and the impact of other resources on the risk to these resources. Solvo will prioritize the findings based on the severity and impact of the findings, will present them and their graphs, and suggest a remediation.
Q: Is Solvo a solution that supports the compliance team?
A: Yes, Solvo supports the compliance team from end-to-end related to the data, cloud infrastructure, and user entitlements. In our Compliance Manager, the compliance team can:
⦁ Use the compliance dashboard to get an overall compliance posture overview and get an idea of overall compliance status.
⦁ Choose the frameworks relevant to your organization and check their boxes.
⦁ Build or import into Solvo OPA rules that you or the community built and you find relevant.
⦁ Handle violations based on severity.
⦁ Govern the entire cloud environment, resources, users, and configurations.
The post Become a cloud security hero first appeared on Solvo.
*** This is a Security Bloggers Network syndicated blog from Solvo authored by Dishant Patel. Read the original post at: https://www.solvo.cloud/blog/become-a-cloud-security-hero/





