SafeBreach Coverage for US-CERT Alert (AA23-040A) – DPRK Malicious Cyber Activities
On February 9th, the National Security Agency (NSA), Federal Bureau of Administration (FBI), U.S. Department of Health and Human Services (HHS), the Cybersecurity & Infrastructure Security Agency (CISA), the Republic of Korea (ROK) National Intelligence Service (NIS), and the ROK Defense Security Agency (DSA) released an advisory highlighting the malicious cyber activities carried out by North Korean (DPRK) threat actors against organizations in the Healthcare and Public Health (HPH) Sector and other critical infrastructure entities. Details of this investigation (along with attacker TTPs and IOCs) were made available via US CERT Alert (AA23-040A) #StopRansomware: Ransomware Attacks on Critical Infrastructure Fund DPRK Malicious Cyber Activities.
This alert updates the advisory originally released on July 6, 2022 – North Korean State-Sponsored Cyber Actors Use Maui Ransomware to Target the Healthcare and Public Health Sector. According to the information listed in the latest advisory, threat actors from the Democratic People’s Republic of Korea (DPRK) accessed privileged networks and conducted ransomware operations against several organizations. Ransoms were specifically demanded in cryptocurrency and it is believed that the revenue generated from these operations will be used to support DPRK national-level priorities and objectives, including initiating cyber-attacks against the U.S. and South Korean government targets including Department of Defense Information Networks and Defense Industrial Base member networks.
Additional Technical Details
The investigation revealed that the TTPs associated with these attacks are those typically observed in DPRK ransomware operations. These tactics are intended to hide their involvement and obfuscate their real identities –
- Acquisition of infrastructure – DPRK threat actors generate domains, personas, and accounts; and identify cryptocurrency services to conduct their ransomware operations.
- Identity Obfuscation – DPRK threat actors purposely obfuscate their involvement by operating with or under third-party foreign affiliate identities and using third-party foreign intermediaries to receive ransom payments.
- Purchase of VPNs and VPSs – Threat actors leverage virtual private networks (VPNs) and virtual private servers (VPSs) or third-country IP addresses to appear to be from innocuous locations instead of from DPRK.
- Gain Access to Networks – DPRK actors have exploited common vulnerabilities including CVE-2021-44228 (log4j), CVE-2021-20038 (SonicWall RCE), and CVE-2022-24990 (TerraMaster TOS unauthenticated RCE). Threat actors were also observed spreading malicious code through Trojanized files for “X-Popup” – an open-source messenger commonly used by hospital employees in South Korea.
- Lateral Movement and Discovery – Post initial access, staged payloads with customized malware were used to perform recon activities, upload/ download additional files and executables, and execute shell commands.
- Ransomware Deployment – Privately developed ransomware, such as Maui and H0lyGh0st along with other publicly available encryption tools were observed being used.
- Ransom Demands – Ransom notes/emails demanded the ransom be paid in Bitcoin and threatened the release of proprietary data to competitors if demands were not met.
Important Note for SafeBreach Customers – Coverage for AA23-040A
As soon as details and IOCs were made available, corresponding new attacks were immediately added to the SafeBreach Hacker’s Playbook on February 9th. It is important to note that some of the attack TTPs used by these threat actors were already available in the SafeBreach playbook. SafeBreach customers already had an existing level of protection against these threat actors if their security controls were validated against these known TTPs.
on February 9th. It is important to note that some of the attack TTPs used by these threat actors were already available in the SafeBreach playbook. SafeBreach customers already had an existing level of protection against these threat actors if their security controls were validated against these known TTPs.
Newly added playbook methods for US-CERT Alert AA23-040A:
Malware IOCs:
- #8585 – Write DPRK PopUp Ransomware to disk
- #8586 – Transfer of DPRK PopUp Ransomware over HTTP/S
- #8587 – Transfer of DPRK PopUp Ransomware over HTTP/S
- #8588 – Email DPRK PopUp Ransomware as a ZIP attachment
- #8589 – Email DPRK PopUp Ransomware as a ZIP attachment
- #8590 – Write Maui (9b0e7c) Ransomware to disk
- #8591 – Transfer of Maui (9b0e7c) Ransomware over HTTP/S
- #8592 – Transfer of Maui (9b0e7c) Ransomware over HTTP/S
- #8593 – Email Maui (9b0e7c) Ransomware as a ZIP attachment
- #8594 – Email Maui (9b0e7c) Ransomware as a ZIP attachment
- #8595 – Write H0lyGh0st Ransomware to disk
- #8596 – Pre-execution phase of H0lyGh0st Ransomware (Windows)
- #8597 – Transfer of H0lyGh0st Ransomware over HTTP/S
- #8598 – Transfer of H0lyGh0st Ransomware over HTTP/S
- #8599 – Email H0lyGh0st Ransomware as a ZIP attachment
- #8600 – Email H0lyGh0st Ransomware as a ZIP attachment
- #8601 – Write DTrack Rootkit to disk
- #8602 – Transfer of DTrack Rootkit over HTTP/S
- #8603 – Transfer of DTrack Rootkit over HTTP/S
- #8604 – Email DTrack Rootkit as a ZIP attachment
- #8605 – Email DTrack Rootkit as a ZIP attachment
Previously available playbook attacks for US-CERT Alert AA23-040A:
- Malware IOCs
- #7181 – Write Maui ransomware to disk (host level)
- #7182 – Transfer of Maui ransomware over HTTP/S (lateral movement)
- #7183 – Transfer of Maui ransomware over HTTP/S (infiltration)
- #7184 – Email Maui ransomware as a ZIP attachment (lateral movement)
- #7185 – Email Maui ransomware as a ZIP attachment (infiltration)
- Behavioral Attacks
- #6843 – Communication with a real malicious server exploiting CVE-2021-44228 (log4j) using HTTP (infiltration)
- #6861 – Remote exploitation of Apache Log4j vulnerability CVE-2021-44228 (infiltration)
- #6903 – Malicious payloads of Apache Log4j 2 vulnerability (infiltration)
What You Should Do Now
Several attack methods related to this US-CERT Alert were already present in the SafeBreach Hacker’s Playbook . The playbook has now been updated with attacks that map to the new IOCs and TTPs identified in this US-CERT Alert. SafeBreach customers can now validate their security controls against these TTPs and IOCs in multiple ways.
. The playbook has now been updated with attacks that map to the new IOCs and TTPs identified in this US-CERT Alert. SafeBreach customers can now validate their security controls against these TTPs and IOCs in multiple ways.
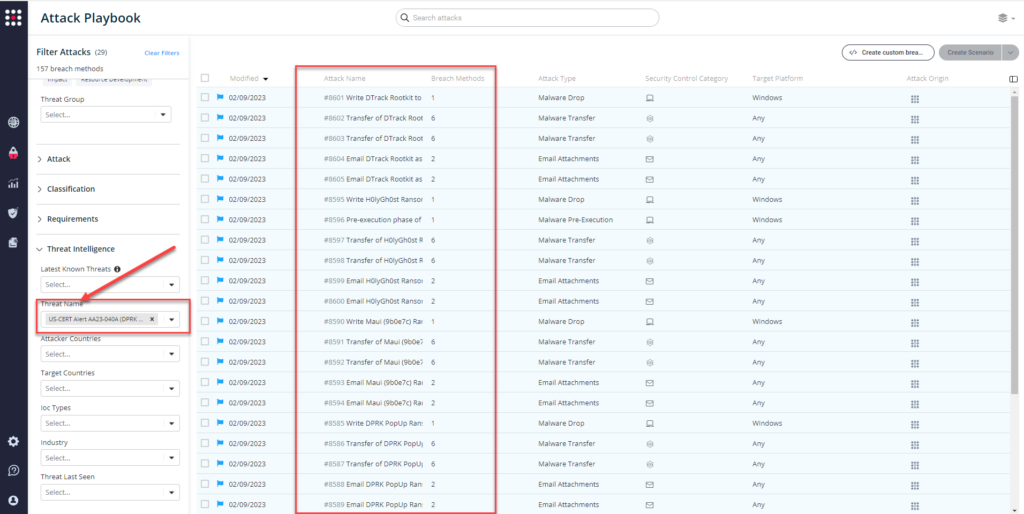
From the Attack Playbook, select and filter attacks related to AA23-040 (DPRK Malicious Cyber Activities).
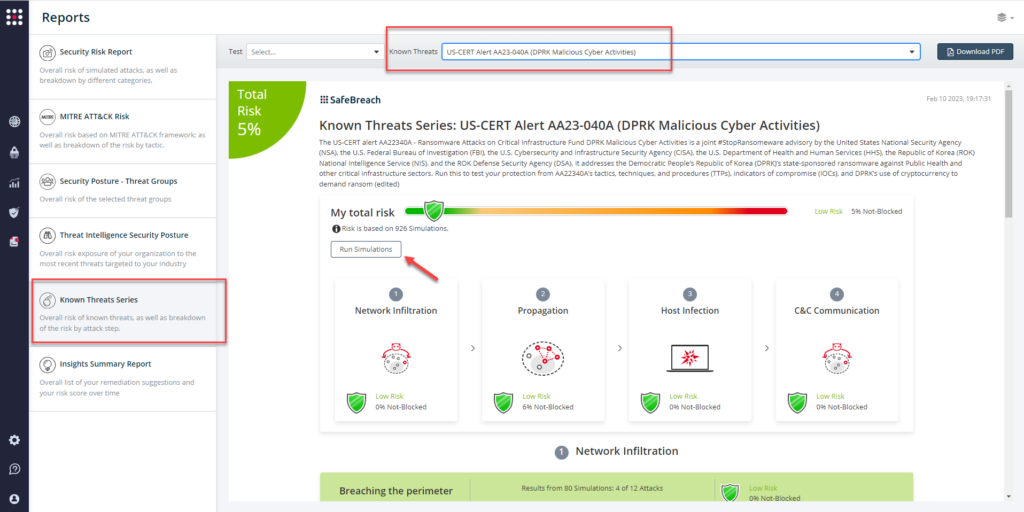
From the Known Attack Series report, select the AA23-040 (DPRK Malicious Cyber Activities) report and select Run Simulations which will run all attack methods.
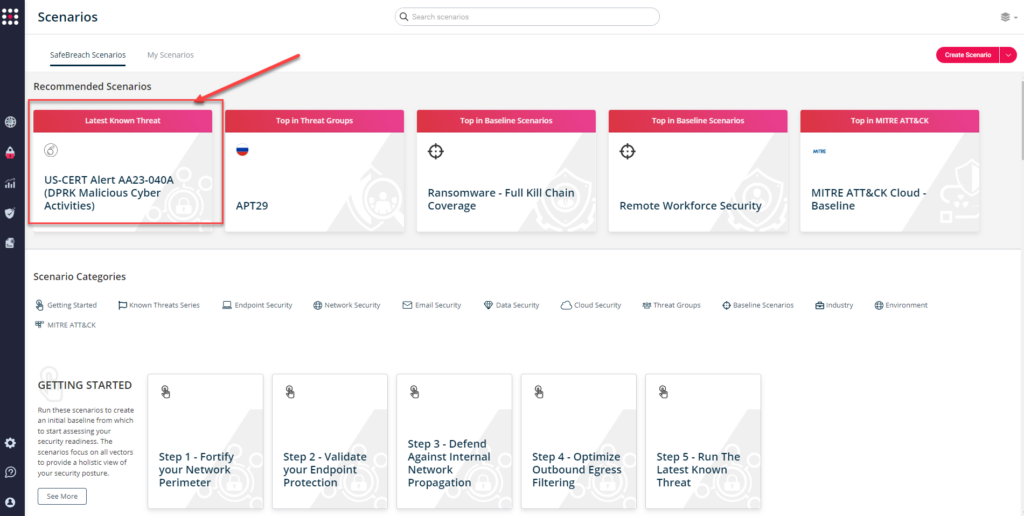
You can also go to the “SafeBreach Scenarios” page and choose the US-CERT Alert AA23-040A (DPRK Malicious Cyber Activities) scenario from the list of available scenarios.
NOTE: The following actions have been recommended for HPH organizations to mitigate any potential threats to their systems:
- Validate Security Controls – CISA and FBI recommend continually testing your security program, at scale, in a production environment to ensure optimal performance against the MITRE ATT&CK techniques identified in this advisory.
- Limit access to data by authenticating and encrypting connections.
- Implement the principle of least privilege by using standard user accounts on internal systems instead of administrative accounts.
- Maintain isolated backups of data, and regularly test backup and restoration.
- Secure the collection, storage, and processing practices for personally identifiable information (PII)/protected health information (PHI).
- Prioritize remediating known exploited vulnerabilities.
- Train users to recognize and report phishing attempts.
- Enable and enforce phishing-resistant multifactor authentication.
Additional Useful Resources
- Stopransomware.gov is a whole-of-government approach that gives one central location for ransomware resources and alerts.
- Stairwell provided a YARA rule to identify Maui ransomware, and a Proof of Concept public RSA key extractor at the following link:
https://www.stairwell.com/news/threat-research-report-maui-ransomware/
You Might Also Be Interested In
The post SafeBreach Coverage for US-CERT Alert (AA23-040A) – DPRK Malicious Cyber Activities appeared first on SafeBreach.
*** This is a Security Bloggers Network syndicated blog from SafeBreach authored by Kaustubh Jagtap. Read the original post at: https://www.safebreach.com/resources/blog/safebreach-coverage-for-us-cert-alert-aa23-040a-dprk-malicious-cyber-activities/