Phishing vs Spam: How to protect your business from both
Phishing vs Spam: One thing we can all agree on is that everyone hates both types of emails more than having a dentist’s appointment on their birthday. But there’s a big difference between the two: Phishing is a much bigger danger to your business than the other.
So where is the line that divides phishing and spam? And how do you protect your business from both? Read the full blog to see which tactic comes out on top and how to protect yourself and your employees from both.
What does phishing mean?
Phishing is a type of cyber attack that uses email or text messages to trick victims into clicking on dangerous links or attachments, or sharing personal information. Phishers (the attackers who send those phishing emails) will often pose as a reputable company or familiar individual in order to gain the trust of their victims. They may also use scare tactics or create a sense of urgency in order to get victims to click on the link or send information (or money directly) without thinking twice.

“It’s been a “super-fantastic” experience to see people learning and talking about security threats.”
For just $325 USD, you can run a 6 week, automated program for gamified phishing awareness training and challenges. (Limited time offer. Normally valued at $999 USD)
Use Promo Code: 6WEEKS
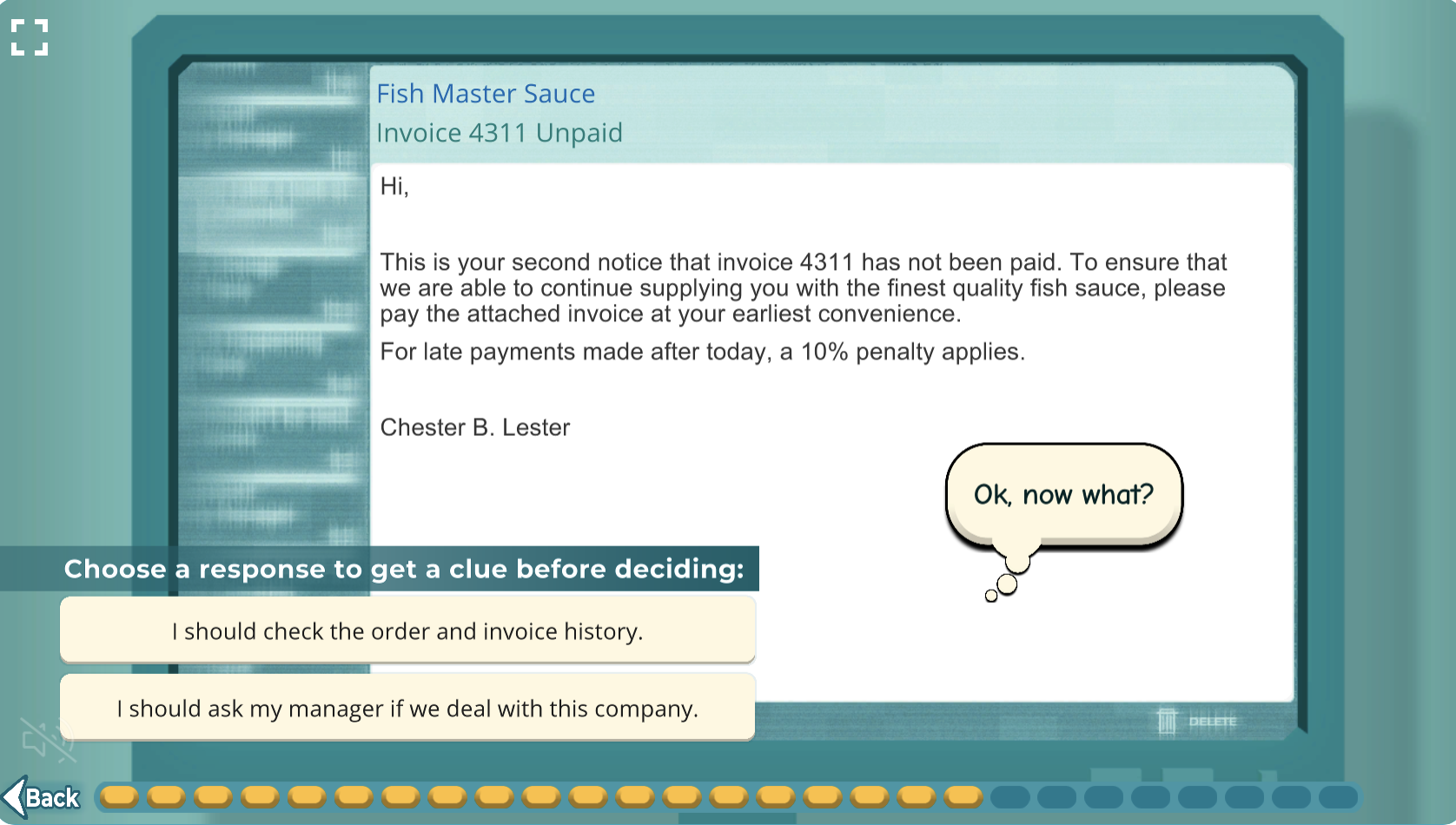
One well-known example of a phishing attack occurred between 2013 and 2015 when employees of several large companies—including Google and Facebook—were targeted with spear phishing emails posing as Quanta Computer Inc., one of Apple’s suppliers. The emails contained fake invoices that lead to these companies paying over $100 million to the fake company’s bank accounts.
The types of phishing
There are different ways an attacker may use phishing to target you or your business. Here are the four main types:
- Email Phishing: This is the most common type of phishing attack. It involves using spoofed emails with malicious links or attachments to trick victims into revealing personal information or downloading malware.
- Spear Phishing: Spear phishing attacks are phishing messages targeted at specific individuals or organizations. The attacker will use publicly available information—such as social media profiles—to create personalized emails that appear to come from a trusted source. They spend more time crafting these because they can get a bigger reward for making you take action.
- Clone Phishing: Clone phishing occurs when an attacker takes an existing email—one that may have already been sent by the target—and replaces any attachments with malicious versions. The email will then be resent to the original recipient with the hope that they will click on the malicious attachment without realizing it has been replaced.
- Whaling: Whaling attacks are similar to spear phishing attacks, but they target high-profile individuals such as CEOs, CFOs, and other executives. These attacks usually involve more sophisticated techniques and can result in much more damage if successful.
Signs you are being phished
Phishing can be hard to identify as attackers are getting sneakier and smarter every year. There are several signs that you can look for to identify a phishing message. If you receive an email or text message that…
- Asks for personal information such as your Social Security number, credit card number, or bank account number
- Asks you to verify account information by clicking on a link
- Contains typos or grammatical errors
- Is from an unknown sender
- Creates a sense of urgency or fear
…then it’s likely that you are being targeted by a phisher. If you’re ever unsure whether an email or text message is legitimate, do not click on any links! Instead, contact the company or friend that they are claiming to be directly using a phone number or email address that you know to be real (try going to their actual website on Google and double-checking there).
What does spam mean?
Spam is unsolicited email messages sent in bulk for commercial purposes. These messages are typically sent by businesses trying to sell products or services, but they can also be sent by individuals for other reasons—such as spreading malware or conducting fraud. So, email can be both phishing and spam at the same time if the goals are to sell you something and also infect your computer or steal information from you at the same time.
A common example of a spam message is an unwanted email about medications at a discounted price. Another example includes texts that you probably received yourself on your cell phone. These messages may use a “made up situation” called a “pretext” such as claiming that you’ve won a prize and should click a link, or they may alert you that something is wrong with an account and they need a payment from you or your SIN.
Signs that a message you received is spam
Spam is usually easier to detect than phishing because it’s sent in bulk and therefore not tailored directly to you. There are some other key signs you can look for to identify spam:
- It’s unsolicited (i.e., you didn’t sign up to receive it)
- It’s sent in bulk (If you Google this spam message do others report seeing it as well?)
- It contains generic content (maybe only vaguely relevant to you)
- It has poor grammar/spelling (this is often a dead giveaway that it’s spam)
Phishing vs. Spam: What’s the key difference?
The main differentiator for phishing vs. spam is the fact that phishing is carefully crafted to trick certain victims while spam messages are sent out in large quantities hoping that someone will fall for them. Spam is a “numbers game” in that it is cheap for a spammer to send thousands or millions of email messages, and it only takes a few responses to make it worthwhile for them. Phishing is more targeted, with an expectation that you will fall for a more complex trick or scam.
If you think about it in terms of a real fishing analogy, email phishing is using certain bait to catch certain fish while spam is putting out a large net and catching whatever they can.
How to protect yourself – and your employees – from both phishing and spam
Phishing
To protect from phishing, you need to take steps to ensure that you (or your employees, if you are a manager) are educated about cyber security threats and trained in how to spot them, and how to report them. Many organizations have a “Report Phish” button in your email program, which helps the security team identify potentially dangerous messages and block them or remove them from employees’ inboxes before they are triggered.
Using Click Armor gamified training provides an engaging and interactive environment for learning about phishing, and creates a more positive security culture within your organization. It shows employees what real phishing messages can look like in a real life. Our “Virtual Inbox Phishing Simulator™” is a safe place to practice spotting many different types of phishing threats.
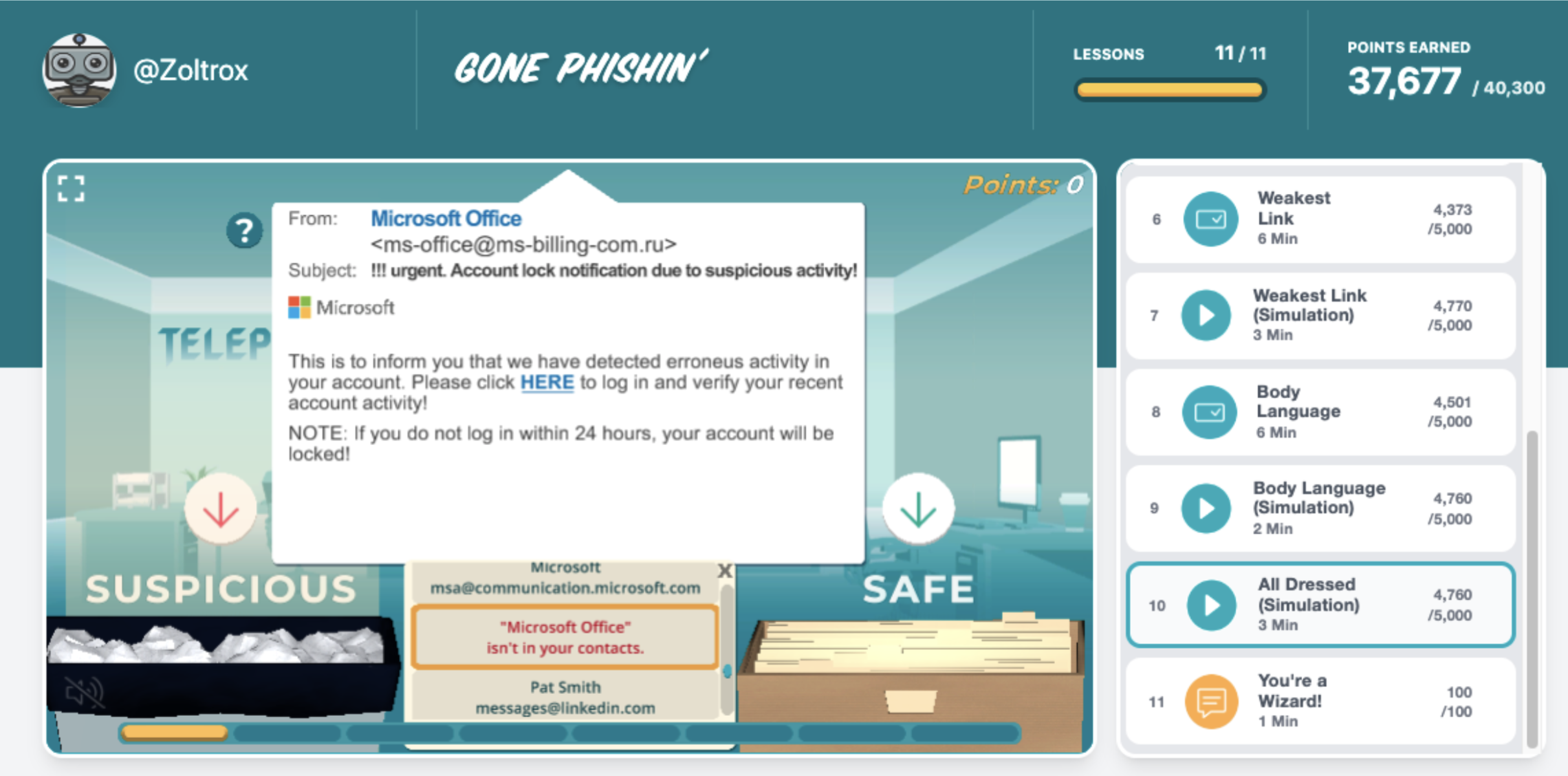
You can book a call with us to get a demonstration or a free trial for your business.
Spam
The best way to protect yourself and your business from spam is to try to avoid it from the beginning. You can do this by being careful about who you give your email address and by using spam filters when setting up your email account. If you’re already receiving spam emails, there’s not much you can do besides delete them.
There is a common tendancy for people to want to “unsubscribe” from spam. However, this is actually not a good idea, if it is really spam. Using the unsubscribe link results in the spammer learning that your email address is “still active”. That makes it more likely that you will get more spam from them, and they can sell your “freshly validated” email address to other spammers.
What may be helpful is for you to simply mark the email message as “Spam” or “Junk” in your email program. This often tells your email provider that the sender is unwanted, and in future these messages may be filtered out.
If you know that a sender is legitimate, and you don’t want to receive their “marketing newsletters” (which you may consider to be spam), then it is usually effective to unsubscribe from them if they are following the anti-spam regulations.
Regardless of whether you think a message is phishing or spam, you shouldn’t click on any links or attachments in them.
So, armed with this information, hopefully you won’t feel like you’re at the dentist every day. You and your colleagues can become more comfortable and confident in how to deal with both phishing and spam, with minimal impact on your productivity.
Scott Wright is CEO of Click Armor, the gamified simulation platform that helps businesses avoid breaches by engaging employees to improve their proficiency in making decisions for cyber security risk and corporate compliance. He has over 20 years of cyber security coaching experience and was creator of the Honey Stick Project for Smartphones as a demonstration in measuring human vulnerabilities.
The post Phishing vs Spam: How to protect your business from both appeared first on Click Armor.
*** This is a Security Bloggers Network syndicated blog from Click Armor authored by Scott Wright. Read the original post at: https://clickarmor.ca/2023/02/phishing-vs-spam-how-to-protect-your-business-from-both/





