API Security Meets Government Regulators
The Australian Cyber Security Centre (ACSC) leads the Australian Government’s efforts to improve cyber security and recent data breaches and the potential theft of private data, have put a spotlight on API security.
API Abuses and Related Data Breaches
The ACSC provides a valuable service as businesses continue to move more of their operations to the cloud and more data moves through APIs. As these trends continue so to is an increase in API-based attacks. The Optus breach is only the latest example. Gartner predicts that by 2024, API abuses and related data breaches will double.
This recent string of API security incidents and data breaches highlights how attackers are leveraging Open Web Application Security Project (OWASP) categorized security gaps to execute their attacks. The techniques observed in these incidents mimic those outlined in the API Protection Report where attackers are actively mixing and matching the OWASP API security categorized threats to bypass common security controls.
A New Control to Ensure Clients Are Authenticated
As a potentially proactive step to help mitigate API threats, the ACSC had added API vulnerabilities to its influential Information Security Manual (ISM). The latest edition of the ISM, published by the ACSC, adds a new control “to ensure clients are authenticated when calling web application programming interfaces that facilitate access to data not authorized for release into the public domain.”
Attackers Performing New Levels of Analysis
These new controls are directly related to trying to prevent attackers using a combination of three different tactics to exploit APIs listed in the OWASP API Top Ten – Broken User Authentication (API2), Excessive Data Exposure (API3) and Improper Assets Management (API9) – to bypass common security controls and achieve their end goal. The increased combination of these three threats indicates that attackers will be performing new levels of analysis to understand how each API works – including how they interact with one another and what the expected result will be.
Shadow APIs and API Security Controls
What complicates matters is security controls will only help if an organization is aware of all APIs used by the business. The challenge is that many companies have unknown or shadow APIs that are hosted by third parties, or are in use by developers, but not visible to the rest of the organization. New research by the Cequence CQ Prime Threat Research team confirms shadow APIs are the top threat challenging the industry with 31%, or 5 billion malicious transactions observed in the first half of 2022 targeted unknown, unmanaged and unprotected APIs, commonly referred to as shadow APIs.
That is because shadow APIs are easy for attackers to discover by analyzing an organization’s exposed APIs and then simply fuzzing or modifying the values, enumerating through other API endpoints on different versions, under different hostnames to find other API variants.
Unified and Integrated Approach to API Protection
To combat the ever-present risk evident with APIs requires a unified and fully integrated approach that works across the entire API protection lifecycle, protecting all APIs, across all API implementations, channels, and infrastructure environments, and all user groups and business use cases.
Cequence has taken the approach that an effective API protection solution should protect APIs across the entire lifecycle, leveraging a collaborative effort that includes developers, application owners and the security team to accomplish the following:
- Outside-in discovery: Gain an understanding of your public-facing API footprint to see what an attacker may see.
- Inside-out inventory: Complement an external view of your APIs and related resources with a comprehensive inside-out API inventory, including all existing APIs and connections.
- Compliance monitoring: Continually analyze existing and new APIs to keep them in compliance with specifications such as the OpenAPI specification and ensure high API coding quality, consistency, and governance.
- Threat detection: Even perfectly coded APIs can be attacked, so it’s critical to continuously scanning your entire API inventory for threats, including subtle business logic abuses and malicious activity that has not yet been observed.
- Threat prevention: It’s critical to be able to respond quickly and natively with countermeasures such as alerts, real-time blocking and even deception, without the need for added third-party data security tools.
- Ongoing API testing: Integrate API protection into development to complement API security efforts defined by shift left efforts within the organization, so risky code doesn’t go live.
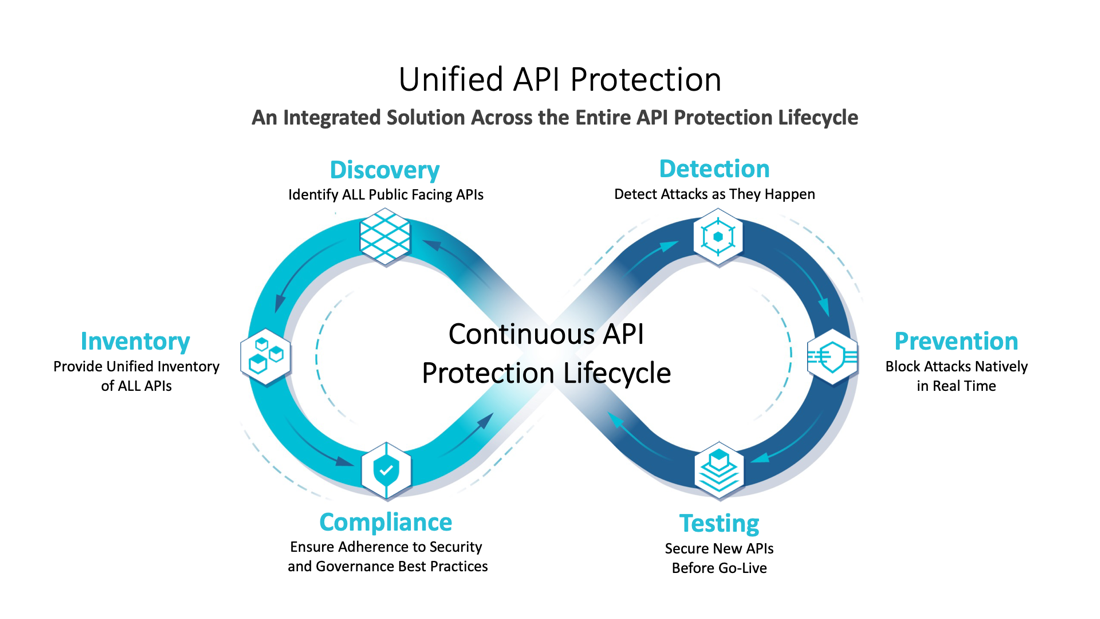
Security teams deploying Cequence Unified API Protection enable their organizations to help comply with regulations, industry requirements and security controls. Cequence improves visibility and protection while reducing cost, minimizing fraud, business abuse, data losses and non-compliance while creating attack futility, failure, and fatigue for even the most relentless of attackers.
Get Started Today with the Cequence Unified API Protection solution
The post API Security Meets Government Regulators appeared first on Cequence Security.
*** This is a Security Bloggers Network syndicated blog from Cequence Security authored by Tony Bailey. Read the original post at: https://www.cequence.ai/blog/api-security/api-security-meets-government-regulators/





