Q4 2022 Analytic Co-Pilot Use Cases
LogRhythm’s Analytic Co-Pilot Services work with customers every single day to develop, implement, and optimize security use cases that matter to their organizations. Since our last quarterly update, we created new content and research against the latest threats discovered in the security world! This blog covers several examples of security use cases we contrived in Q4 2022.
When we work with our customers during weekly sessions, we often come across interesting use cases that can apply to other environments. Rules that we find helpful get shared to all our customers and the wider InfoSec community so that we can spread the wealth of knowledge and tactics needed to fight cybercrime! This quarter, we have seven new security use cases to share.
Seven security use cases from Q4 2022
To understand the complexity of a use case and how it may apply to your environment, we provide a key at the start of each one to explain:
- Which Module the use case aligns to
- The log sources required to successfully implement a use case
- Difficulty score to set up the use case and how complex it may be
- Impact rating to assess how a use case can positively impact threat monitoring
1. PuTTY usage for SSH
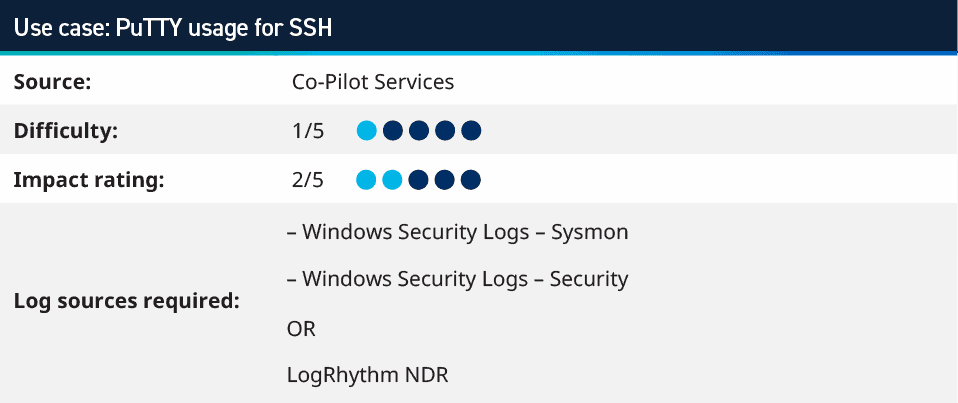
One of our Analytic Co-Pilot customers implemented a new privileged access management (PAM) solution and connected the servers to it to better manage administrators and track user credentials. To track policy violations, we helped our customer set up a rule to monitor for PuTTY (a popular tool for SSH connections) starting and then making a connection to the server. This rule can be expanded upon to monitor for other remote access tools that may be used in an environment.
It can take time and effort to change staff habits from using existing products to a new PAM tool. To ensure the best security around privileged access, it’s important to monitor the use of the legacy tools as well.
This use case can be monitored in LogRhythm SIEM, as well as in LogRhythm NDR using the search below to look for the client type of PuTTY (which again can be built out further for other applications or switched to look for anything that is not the PAM client).
entry_type:Ssh AND client:/.*PuTTY.*/
Learn more in our Security Spotlight video:
2. Different suspicious or malicious command line parameters
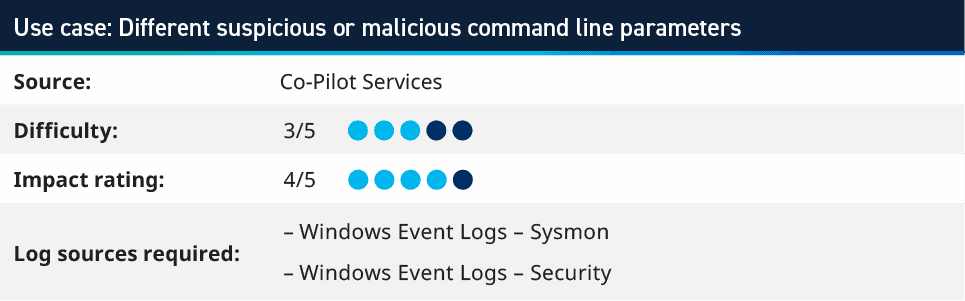
A tweet from a respected security practitioner inspired one of the Analytic Co-Pilots to create a use case as a proof of concept. The tweet asks if you had access to an unknown security information and event management (SIEM), what would you look for in ten minutes?
Imagine you’d get access to an unknown SIEM of a new customer & would be given 10min to find malicious activity by using keyword searches on raw data, what would you search for?
I’ll start
‘.dmp full’
‘whoami’
‘delete shadows’
‘FromBase64String’
‘save HKLM\SAM’
‘ -w hidden ‘— Florian Roth ⚡ (@cyb3rops) November 16, 2022
This inspired a proof of concept rule to look for Commands in Windows Security and Sysmon logs that could be considered suspicious or malicious. The list of commands was taken from Florian Roth’s Godmode Sigma Rule on Github and converted into RegEx for the command fields within an AI Engine rule, but also saved as a Saved Search in the Web Console, where it can run ad-hoc.
This is a list of commands which would seem unlikely to be in a production environment, however this may require some investigations and tuning of the regex to work effectively in your environment. One example we found on customer environments is the “-ma” switch was triggering on too may commands and needed to be removed to reduce the number of false positives.
3. Detecting Raspberry Pi connecting to network
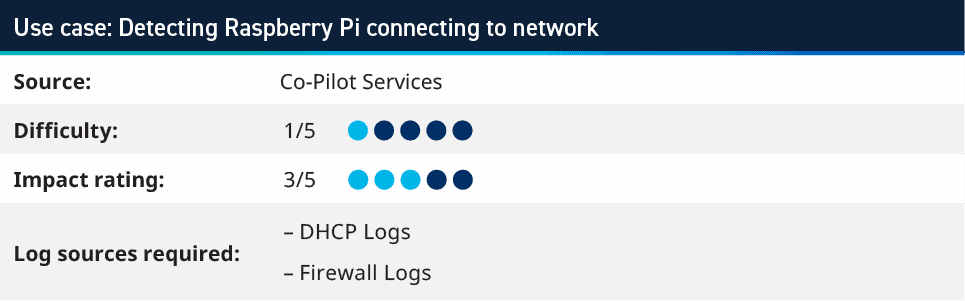
Raspberry Pi’s are USB-powered systems which on a small device, can contain powerful hardware. With Gigabit Ethernet, up to 8GB of RAM and even 4k HDMI output, these systems can be used for desktop and teaching programming; however, they can also be used as network plants to maintain access to an environment. Monitoring for these can use the DHCP Server logs to look for leases obtained from systems with MAC Addresses matching the organizationally unique identifier (OID) of the Raspberry Pi. The MAC address is broken down into two parts, where the first 24-bits of the MAC address are the OID and the last 24-bits are the unique address of that device.
By using the known OIDs of Raspberry Pi’s, you can create an AI Engine rule where you look for MAC Address Impacted as the following Regex:
- ^(b827eb).*
- ^(dca632).*
- ^(28cdc1).*
- ^(e45f01).*
This rule can expand further to look for other device OIDs that you would not expect in your network. For example, other micro-PC vendors or manufacturers that are not authorized to be used. This rule was initially created to look for these logs in DHCP logs; however, if your Firewalls or other network devices also provide the MAC Address information of the clients on their L2 network, then this can also be used to monitor. Although, you need to ensure that you are monitoring on each layer 2 network, as the MAC address changes in the network frame on each hop across the network. If your user networks are routed two or three times before getting to the Firewall that reports MAC Addresses, it will only monitor the network it is directly attached to, and not the initiator of the packet.
4. Hoaxshell reverse shell
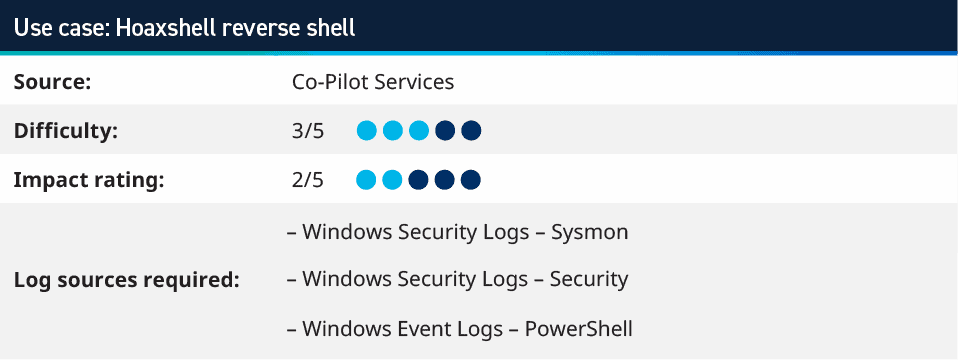
Hoaxshell is an unconventional Windows reverse shell, initially undetected by Microsoft Defender and other AV solutions, solely based on http(s) traffic. The tool is easy to use, it generates its own PowerShell payload, and it supports encryption (SSL). We tested the exploit against fully updated Windows 11 Enterprise, Windows Server 2016 Datacenter, and Windows 10 Pro boxes — and found these systems were vulnerable to an attack. When this was originally released in September to October 2022, it was not detected by most AV solutions, but it eventually was added to these solutions, and can now be detected in its raw form; however, it still could be obfuscated to bypass such detections. The payload runs an encoded PowerShell command to create a reverse shell that uses HTTP or HTTPS to communicate and allows for a reverse shell to be created from the victim’s machine to the attacker’s system.
To detect the payload from PowerShell logs, we created an AI Engine rule to look for the de-obfuscated string which we would get from the PowerShell logs and monitoring for this regex string:
\$s=’?\d+\.\d+\.\d+\.\d+:\d+’;\$i=’\w+-\w+-\w+’?;\$p='(http|https)://’;\$v=invoke-webrequest.*
Learn more in our Security Spotlight video:
5. Domain account creation
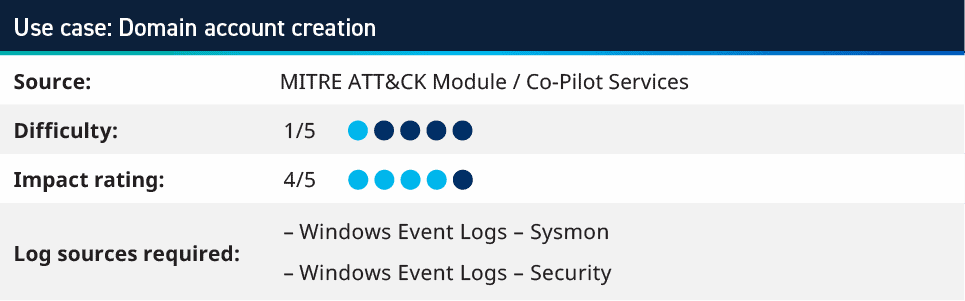
If an attacker gains access to elevated credentials within an environment, they may look to create one or more accounts that can be used for persistent access. Whereby, if the account that they have compromised is found and the password is changed or the account is disabled, then having back up accounts provides great value for them to continue attacking your environment.
This rule looks for accounts being created via PowerShell in the domain, as this could be the actions of a script or preferred method of attackers because it allows for multiple accounts to be created quickly. The rule looks for logs where the command includes things such as “net user/add.”
6. Mark-of-the-Web (MOTW) Evasion as Virtual Containers
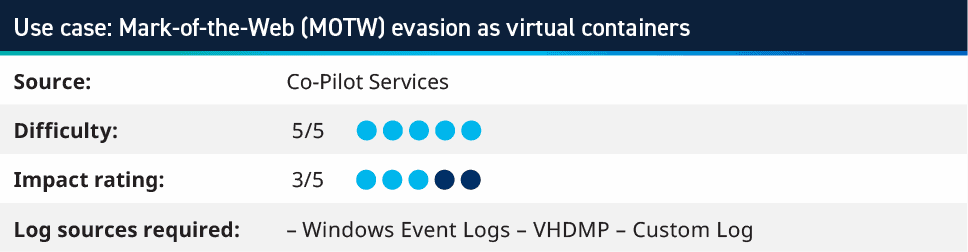
This is a slightly tricker use case, as it involves collecting a log from the Microsoft-Windows-VHDMP-Operational log source within Windows, which monitors for the use of Virtual Hard Disks. This use case can be used to monitor for phishing campaigns in which the initial payload is delivered via virtual images such as .iso, .img, or .vhd being mounted and containing various creative execution methods, including malicious .chm and .lnk.
This has been leveraged as part of the attack chain that adversaries use, and we’ve seen an uptick in activity in recent months. The increase in popularity among adversaries is due to this method of delivering the initial malware payload in image containers evades being tagged with the Mark-of-the-Web (MOTW). The MOTW can frustrate attackers attempts at gaining an initial foothold via email campaigns; however, virtual image containers have been used successfully to subvert this security control.
Here are examples of groups leveraging virtual images as a means of initial payload delivery:
- Bumblebee ransomware
- Quantum ranswomware
- AgentTesla
- ChromeLoader
Looking for Event ID 1 and/or 23 where the object that is being mounted is .iso, .vhd or .img can be an indicator that this attack method is being used, especially if mounting of virtual images is uncommon within your environment. This can be further built upon if the user is not an admin account or is a non-IT employee.
7. Process injection: Process hollowing
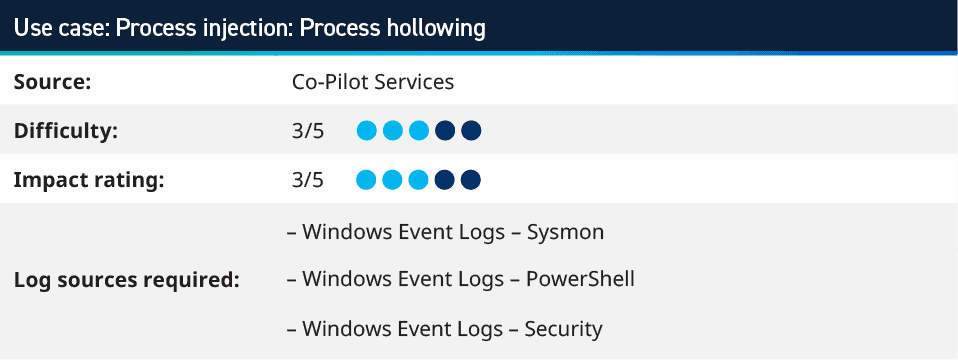
Process hollowing is where adversaries inject malicious code into suspended and hollowed processes to evade process-based defenses. It is a method of executing arbitrary code in the address space of a separate live process. Process hollowing is commonly performed by creating a process in a suspended state then unmapping/hollowing its memory, which can then be replaced with malicious code. A victim process can be created with native Windows API calls such as CreateProcess, which includes a flag to suspend the processes primary thread. At this point the process can be unmapped using APIs calls such as ZwUnmapViewOfSection or NtUnmapViewOfSection before being written to, realigned to the injected code, and resumed via VirtualAllocEx, WriteProcessMemory, SetThreadContext, then ResumeThread respectively. Visit MITRE ATT&CK to learn more information about Process hollowing.
To monitor against these attacks, the LogRhythm Co-Pilot team created three rules to look for the activity expected around this behavior.
- The first rule looks as the start-hollow script that can be used to conduct the process hollowing within PowerShell.
- The Second rule looks at the evidence of the script being downloaded via PowerShell and then invoked as a Macro to conduct the process hollowing.
- The third rule looks at office applications (such as Windword.exe) spawning other processes which are not winword.exe; for example, winword.exe launching Notepad (as used in our non-destructive testing), however, notepad.exe could be malicious applications or scripts.
Learn more in our Security Spotlight video:
More Analytic Co-Pilot use cases and resources
Our team is happy to share more use cases that we worked on with our Analytic Co-Pilot customers. Over this last quarter, we have had several customers focus on ransomware attacks, reverse shells, use account creation, detecting PuTTY usage after implementing a PAM solution, and more! To glimpse over other use cases our Co-Pilot team has worked on in previous quarters, visit the following blogs below:
To learn more about our Analytic Co-Pilot Services and how we can improve your threat detection and response, learn more here. If you are a customer and you have questions, reach out to your customer success manager or account team to get more information about how we can help with your use cases and analytics!
The post Q4 2022 Analytic Co-Pilot Use Cases appeared first on LogRhythm.
*** This is a Security Bloggers Network syndicated blog from LogRhythm authored by Kelsey Gast. Read the original post at: https://logrhythm.com/blog/q4-2022-analytic-co-pilot-use-cases/





