Control Web Panel Vulnerability, CVE-2022-44877, Actively Exploited in the Wild
This post offers details on the Control Web Panel Vulnerability, CVE-2022-44877, which is actively being exploited in the wild.
If you are using Control Web Panel in any version below 0.9.8.1147, make sure to patch as soon as possible.
While CVE-2022-44877, a critical vulnerability affecting Control Web Panel (a popular free, closed-source, web-hosting interface), has received an official patch on October 25th 2022, evidence of active exploitation of the vulnerability are starting to accumulate.
Over the last week, starting January 6th, adversaries appear to be scanning for unpatched instances running Control Web Panel (CWP) as well as actively attempting to exploit them.
Currently, according to threat intelligence platform GreyNoise, there are at least four different IP addresses actively targeting the vulnerability.
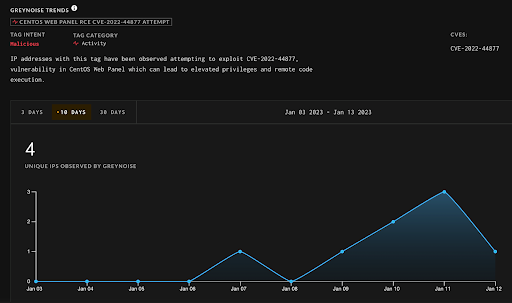
Image: greynoise.io
This came soon after the release of Proof of Concept (PoC) exploit code published on Github by security researcher Numan Türle on January 5th.
The Vulnerability: CVE-2022-44877
CVE-2022-44877, is a remote code execution vulnerability that stems from a single line of code in the /login/index.php file which allows unauthenticated attackers to execute code on the machine running the Control Web Panel.
The problematic line uses the following structure in order to log errors:
echo "incorrect entry, IP address, HTTP_REQUEST_URI"
The fact that the logging functionality relies on bash (via the echo command), and the HTTP_REQUEST_URI parameter is user controlled, allows an attacker to take advantage of a built in bash feature called Command Substitution by crafting a “malicous” HTTP request containing system commands.
How does it work?
Command substitution, according to the bash man pages, allows executing commands using the following syntax: $(<COMMAND TO EXECUTE>)
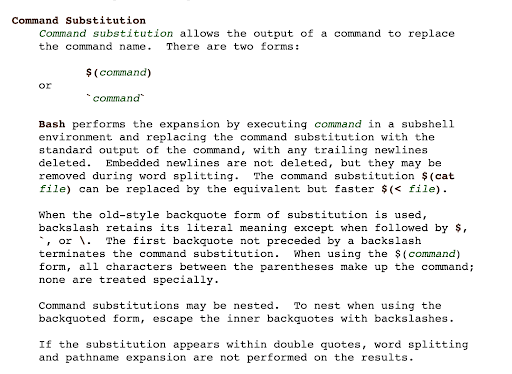
Hence, all an attacker has to do in order to take advantage of this built-in bash functionality is simply to send a request such as:
POST /login/index.php?login=$(<some_command>)
With the appropriate headers and the command will be executed with its output logged into a CWP log file.
As you can see, this makes exploitation of the vulnerability trivial.
Scope of CVE-2022-44877
Although some source claimed that the number of publicly facing instances running CWP is over 400,000, Rezilion analysis found just a few over 50,000 vulnerable servers:
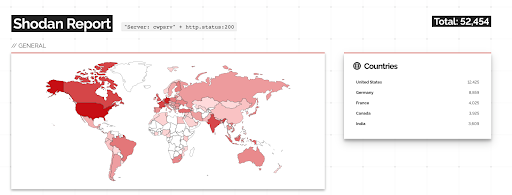
Source: shodan.io
This statistic more closely aligns with data collected by the ShadowServer foundation, identifying just a bit over 38,000 exposed servers running CWP:
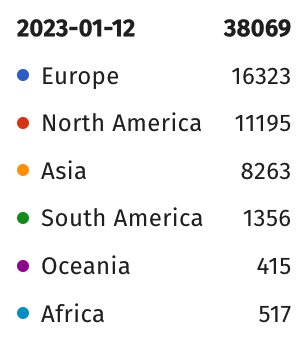
It is important to note that at least some portion of these instances have already patched their systems and hence are no longer exploitable.
Remediation for CVE-2022-44877
If you are using Control Web Panel, running any version below 0.9.8.1147 make sure to upgrade to the latest version as soon as possible. We also advise examining your application logs for any abnormalities.
The post Control Web Panel Vulnerability, CVE-2022-44877, Actively Exploited in the Wild appeared first on Rezilion.
*** This is a Security Bloggers Network syndicated blog from Rezilion authored by Yotam Perkal. Read the original post at: https://www.rezilion.com/blog/control-web-panel-vulnerability-cve-2022-44877-actively-exploited-in-the-wild/





