Closing the Gap Between Business Risk and Cybersecurity Risk
A common refrain I hear from enterprises when they deploy a new security control is that it adds an operational burden in exchange for providing a new set of security results.
On the one hand, enterprises deploy innovative security controls to get the best security efficacy possible for the attack surfaces being protected. They can also better meet their cybersecurity posture and compliance requirements.
On the other hand, by deploying a new tool, they also increase the volume of security results that need to be monitored and remediated. The volume continues to grow as they implement digital transformation projects, move to multi-cloud environments, support hybrid work, and secure connected IoT devices.
What happens to the results detected by all these tools: indicators of compromise, vulnerabilities, in-progress attacks, malware, misconfigurations, and user behavior anomalies? They are typically forwarded as an alert or log event to another tool. In the case of active threats, that system can be a Security Information and Event Management (SIEM). For vulnerabilities, there is often a dedicated process to keep the OS and application software up to date. Based on the security issues and their criticality, the security operations team will conduct follow-up investigations, remediations, and incident responses.
As you are probably already aware, the number of security issues generated daily is overwhelming and beyond the capacity of the resource-constrained security operations team. Fortunately, for vulnerability detection, traditional vulnerability management tools have built-in workflows to improve operational efficiency. For example, there are workflows to automate remediation tasks like patching software and checking that the patch process is completed.
For threat detection, existing tools improve operational efficiency. SIEM and extended detection and response (XDR) are used to perform advanced analytics to simplify threats and anomaly detection across security controls and speed up investigations, while security orchestration, automation, and response (SOAR) tools provide workflow automation.
However, security teams still struggle to prioritize the results. This problem is particularly acute when security teams manually prioritize the security results and the impacted assets to be fixed. A big reason is that prioritization is based on the severity of the security issue. With regards to vulnerability management, prioritization is often limited to the severity and threat level scores for common vulnerabilities and exposures (CVE) and derived for non-CVE vulnerabilities. This is usually inadequate as there can be hundreds of high-severity vulnerabilities each impacting hundreds of assets. Moreover, new vulnerabilities come in daily.
Security results could also be prioritized based on business impact, but there hasn’t been an easy way to incorporate business impact. This is where the Balbix platform comes in. The Balbix platform is the first vulnerability management tool I’ve seen that closes the gap between security issues and the corresponding business impact. It does this with automated cyber risk quantification (CRQ) by building a security risk model of the enterprise based on its assets and security risks.
The image below shows the Balbix dashboard. The top row displays the overall breach risk for the enterprise. It is composed of breach likelihood (the probability that a breach attempt will be successful) multiplied by breach impact (the impact on the business in monetary terms if the assets are breached). In this case, breach impact is $312 million but breach likelihood is only 7%, so the resulting breach risk is $21.6 million.
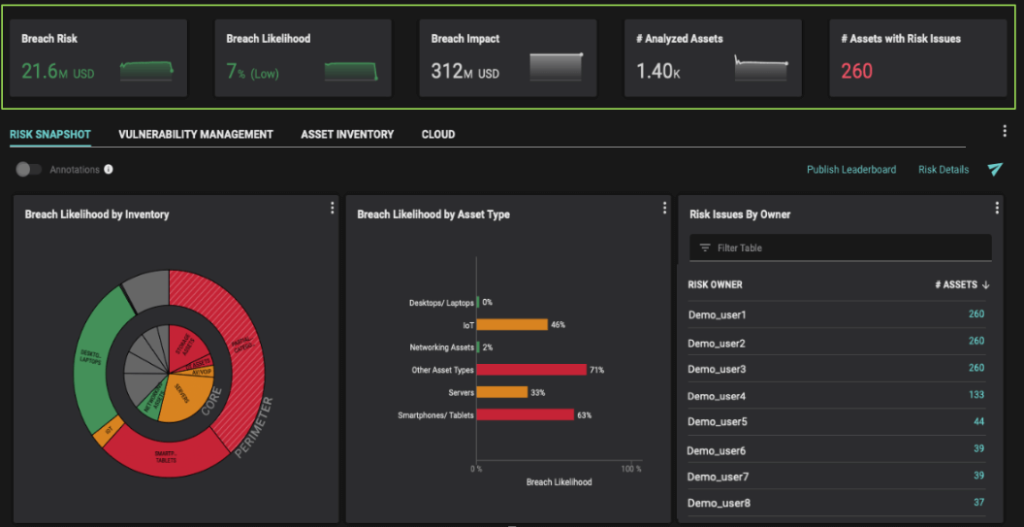
Breach risk represents the overall business impact on the enterprise in the event a breach occurs and it is based on aggregation of risk across all the assets and security issues. Being able to measure the impact of risk in monetary terms helps with the prioritization of security issues.
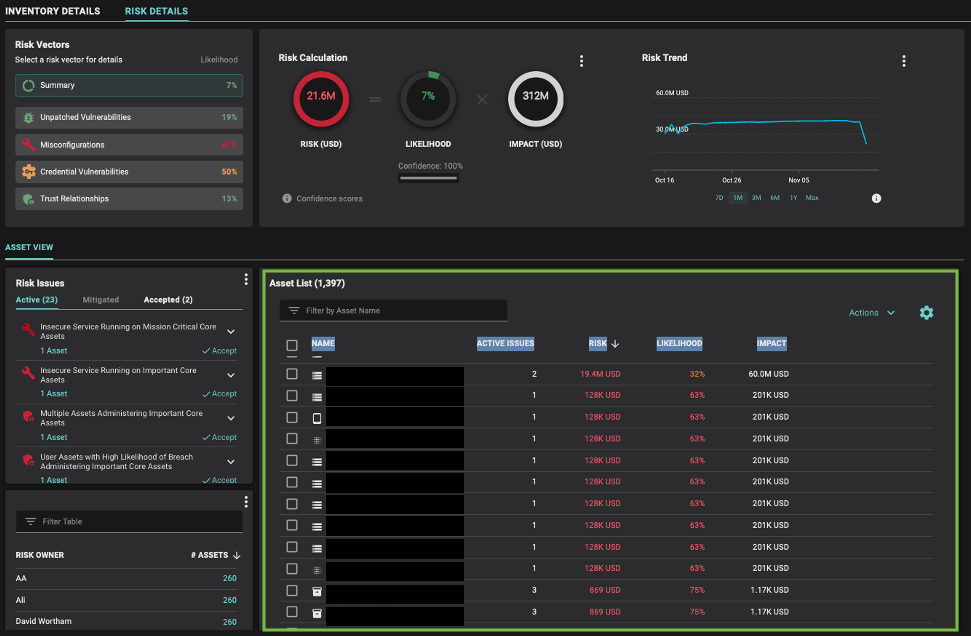
Balbix users can use CRQ to drill down to see the list of assets ranked by breach risk along with the number of security issues associated with each asset. This is shown in the diagram below. Using CRQ, prioritization now becomes straightforward for the security operations team.
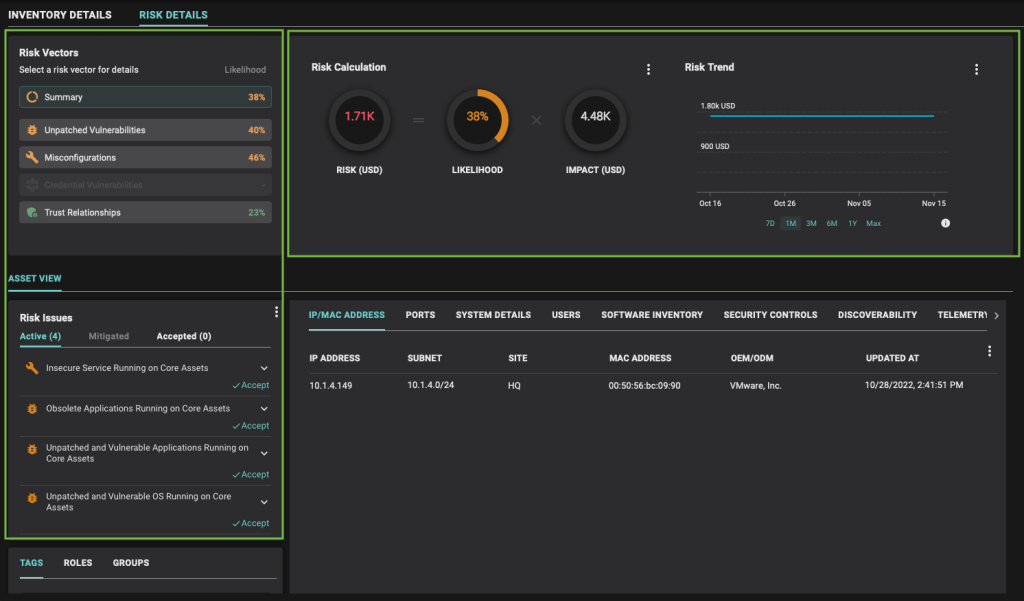
Going one step further, users can drill down to a specific asset and see all of its security issues, along with the asset’s overall breach risk, as shown in the image below. They can choose to remediate or accept the security risks. They can also use the risk trend graphic to monitor how breach risk changes over time due to new security issues being detected and remediations being carried out.
CRQ also provides additional benefits besides simplifying prioritization for security issues. Benefits include: justifying new security initiatives and budget, reporting to executive leadership and board of directors so that they can understand which parts of the enterprise are at risk, quantifying how current security projects are impacting the enterprise breach risk, and assisting with cybersecurity risk transfer strategy.
In summary, Balbix is leading the way in quantifying security risk so that enterprises can make security risk decisions based on their business outcomes. I am excited to be part of this journey.
*** This is a Security Bloggers Network syndicated blog from Blog – Balbix authored by Leena Merciline. Read the original post at: https://www.balbix.com/blog/closing-the-gap-between-business-risk-and-cybersecurity-risk/





