FedRAMP: Time to Authorization
One of the biggest questions in the quest for a Federal Risk and Authorization Management Program (FedRAMP Authorization is “how much time will it take?” The correct answer to this question is… “it depends.” From low to high estimates, the journey can take anywhere from six months to two-plus years, with most efforts falling somewhere in between. The good news is the emergence of FedRAMP acceleration solutions (including compliant infrastructure as-a-service (IaaS) and platform as-a-service (PaaS) offerings) means cloud solutions are no longer starting from scratch when establishing FedRAMP compliance.
Notional Timeline for FedRAMP ATO Journey:
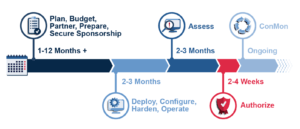
There are several factors that impact the end-to-end schedule at each phase in the process.
1 – Plan, budget, partner, prepare and secure sponsorship (1-12+ Months)
The most variable phase in a FedRAMP journey timeline, and therefore the most difficult to scope in terms of timing, is the one that precedes deployment and assessment. Before embarking down the FedRAMP Authorization path, assessment, there is much work that needs to be done.
- Planning – A FedRAMP journey has organization-wide impacts. Cloud Service Providers (CSPs) need to invest in adequate planning time, preferably with the support of a trusted FedRAMP advisor, before making a decision when and if to proceed.
- Budgeting – FedRAMP compliance requires budgetary commitments that are not insignificant. Hosting, licensing, engineering efforts and required 3rd Party Assessment Organization (3PAO) costs add up quickly.
- Partnering – Finding the right partners and formalizing relationships can be a daunting task. Third-party tools, technologies, and consultants, including an assessment 3PAO, should be in place.
- Preparing – Analyzing gaps in human resources, processes and technologies must be done to establish the right remediations.. Technical preparation may be the longest pole in the tent during this first phase, depending on the as-is state of a Cloud Service Offering (CSO) at the onset. Some gaps can be remedied quickly and inexpensively, while some can take months or even years to fully implement.
- Securing Sponsorship –For CSPs who have existing, committed government customers that are willing to sponsor, there will be little to no effort here. However, for the majority of CSPs without this existing relationship, securing a sponsor can take months if not years. A government agency must have enough buy-in to the CSO that they are willing to invest the time and effort into being a sponsor. There is always the possibility, for sponsor-less CSPs, to obtain a Joint Authorization Board (JAB) sponsorship. However, JAB sponsorship opportunities are very difficult to secure. Many CSPs without a clear path to an agency sponsor choose to pursue a “FedRAMP Ready” status by undergoing a Readiness Assessment performed by a 3PAO. While “FedRAMP Ready” is not sufficient to grant an ATO or obtain full FedRAMP Authorization, it can a CSP listed on the FedRAMP marketplace, increase overall traffic to and awareness of the CSO, and may help secure a sponsor since there is a proven commitment to the FedRAMP Authorization process.
2 – Deploy, configure, harden and operate (2-3 Months)
The process of deploying a CSO in a compliant environment and configuring and hardening that CSO once it is operational, can be a somewhat fast process, depending on the absence of FedRAMP show-stoppers and willingness and ability of the CSO to leverage FedRAMP authorized systems and services. Additionally, moving quickly in this phase will likely require a CSO to leverage Infrastructure and/or Platform-as-as-Service (IaaS/PaaS) security stack built specifically for compliance. This phase also includes the authoring of system documentation, including but not limited to, policies and procedures, system security plans (SSPs), and contingency management plans.. Regardless of how quickly a CSO can be stood up, documented, and brought into compliance, there must be 90 days (3 months) worth of monitoring logs and vulnerability scanning records for a 3PAO to complete their full assessment. This means that this phase must be 90 days long, or nearly 90 days depending on the needs and requirements of the specific 3PAO.
3 – Assessment (2-3 Months)
Assuming the CSOis in good shape from a compliance standpoint and all things run smoothly, the assessment can feasibly be completed in 2-3 months. This timeframe assumes the authorizing official (AO) is quick to review and approve the System Assessment Plan (SAP), there are no issues found that require significant time to remedy, and that documentation is clear and complete. The assessment will include interviews, collection and reviews of evidence that supports assessed controls, reviews of documentation, reviews of systems scans, and penetration testing. Since this phase relies on outside 3PAO resources – the schedule may be lengthened depending on the 3PAOs schedule.
4 – Authorize (2-4 Weeks)
Once the 3PAO has completed their assessment, the full security assessment and authorization (SA&A) package will be submitted to the sponsoring agency or JAB for review and approval. There will be a kickoff meeting with the sponsor, and likely some iterative refinements of the system and/or documentation to satisfy the sponsoring agency. Once all parties are , an ATO would be granted. As with the assessment, this phase also depends on outside agency and/or JAB resources, and will be impacted based on the schedules, availability and workload of those resources.
As for time to FedRAMP Authorization , the timelines listed are a notional and assume a “happy path” journey. Ensuring that deployments within the CSO are in order/compliant gives an authorization effort the best chance of a “quick” timeline. That said, it is important to remember that there are multiple players in this journey, all with busy schedules. CSPs have very little control over the schedules of government AOs and 3PAOs. And finally, it is impossible to predict with certainty what an assessor or AO may find unacceptable due to varying interpretations of the baseline controls – so, it is best to hope for a quick/smooth journey, but plan for one that goes a little longer than anticipated.
About stackArmor
stackArmor helps commercial, public sector and government organizations rapidly comply with FedRAMP, FISMA/RMF, DFARS and CMMC compliance requirements by providing a dedicated authorization boundary, NIST compliant security services, package development with policies, procedures and plans as well as post-ATO continuous monitoring services.
*** This is a Security Bloggers Network syndicated blog from Blog Archives - stackArmor authored by stackarm0radm1n14274. Read the original post at: https://stackarmor.com/fedramp-time-to-authorization/





