4 Expert Tips for Data Center Security
In a market projected to grow to $288.30 billion by 2030, data centers will expand to facilitate more data-driven workloads, including AI and big data. Much of this expansion continues to occur in the cloud, as companies seek to reap the benefits of low-cost infrastructure that they can spin up as needed. In fact, research shows that cloud workloads represented 94% of all data center workloads worldwide in 2021. But in a world of virtualized servers and multi-cloud environments, data center security is becoming increasingly complex.
Threat actors often target valuable information when conducting cyber attacks, and the nature of modern data centers opens up more potential points of compromise. Security considerations need to go beyond on-premises systems to account for virtualized servers and ever-expanding cloud infrastructure. Sounds relatable? Keep reading to get four expert tips for strengthening data center security at your organization.

What is data center security?
Data center security is the protection of data centers against unauthorized access and attacks. The security of data centers depends on a combination of policies, practices, and tools that together protect the critical business workloads, applications, and data that a data center houses.
With physical, self-hosted data centers, security measures typically include restricting access, monitoring entry points, and applying network segmentation so that threats from one part of your network can’t infiltrate data center resources.
When businesses adopt hybrid infrastructure models, they virtualize part of their data centers, often using cloud-based resources. This virtualization makes modern data centers highly scalable—it’s faster, easier, and cheaper to deploy additional cloud-based data center resources without needing to acquire, configure, and maintain extra physical appliances.
It’s also worth bearing in mind that even when you use public cloud resources that aren’t part of your data center infrastructure, these resources live inside the data centers of external companies. Cloud and virtual data centers come with extra security considerations, including access management, configuration, and gaining visibility as workloads move between on-premise and cloud systems.
Data center security also extends to ensuring high availability because incidents that make important resources unavailable can have serious costs and consequences. For example, a DDoS attack on an online banking app means customers can’t check balances or transfer funds, which reduces their trust in critical services. The need for high availability is part of the popular CIA triad model of information security where information security policies are guided by the principles of confidentiality, integrity, and availability.
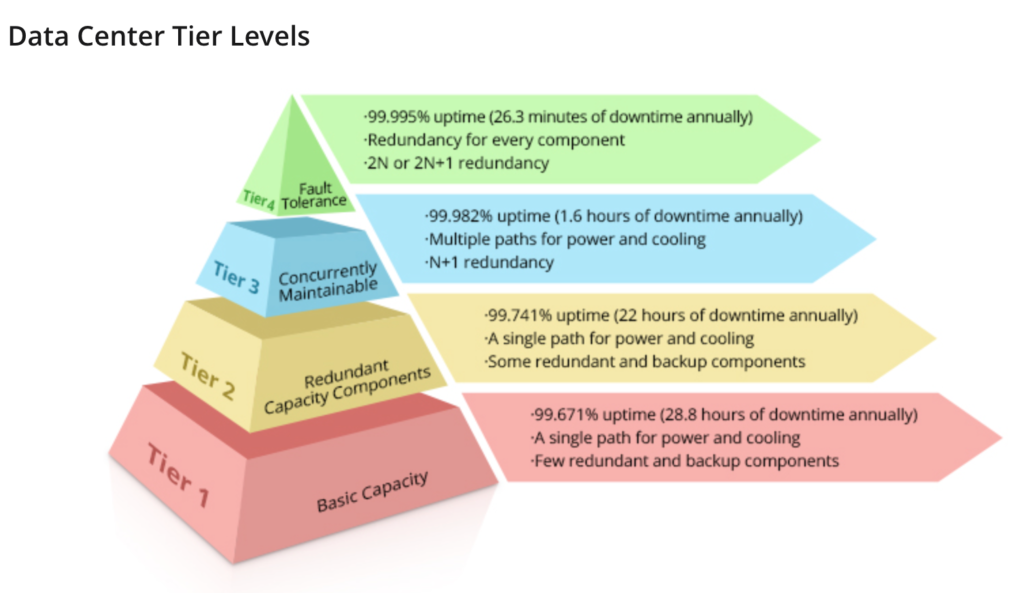
The TIA-942 standard outlines the data center design and security expectations based on different tiers of desired availability:
- Tier 1- Basic – This tier has expected annual downtime of 28.8 hours. There are no minimum dedicated physical security staff requirements, while generators, doors into computer rooms, and fiber vaults have industrial-grade locks.
- Tier 2 – Redundant Components – This tier has annual downtime of 22 hours. A minimum of 2 dedicated security staff guard the physical premises, while intrusion detection systems secure doors into computer rooms, generators, and fiber vaults.
- Tier 3 – Availability – This tier’s data centers have annual downtime of 1.6 hours. Additional security expectations beyond the previous tier include 3 minimum dedicated physical security staff, security and network operations with card access, and CCTV monitoring throughout the location.
- Tier 4 – Fault Tolerant – With annual downtime of just 0.4 hours, this tier adds mostly extra electrical and design minimums to achieve higher uptime.
Interestingly, most major cloud providers don’t specifically adopt or apply these standards. Rather, they take their own custom approach to achieve high uptime.
Why is data center security a must for your company?
Data centers are vulnerable to a wide range of risks that could lead to costly downtime or data breaches. Specific threats include ransomware attacks that encrypt critical information assets, intruders exfiltrating sensitive data after compromising privileged account credentials, denial of service attacks knocking critical apps offline, web application attacks exploiting code weaknesses in critical applications, and more.
Data breaches alone cost companies an average of $4.35 million per breach in 2022. Aside from avoiding these obvious and painful costs, data center security is a must for preserving customer trust and guarding trade secrets, business plans, or other confidential information that provides a competitive advantage.
Why should developers care about data center security?
Developers have a critical role to play in data center security because modern development and DevOps teams essentially hold the keys to cloud security. In the cloud, developers and engineers set and change important security configurations while building and running critical applications on cloud infrastructure.
From coding errors to exposed secrets to configuration mishaps, everything in the cloud is software-driven, and the changing nature of data center infrastructure puts the responsibility for security increasingly on the shoulders of those involved with software development. This responsibility even rings true for securing serverless applications in which the cloud provider takes responsibility for the underlying infrastructure security, but proper security practices still rest on developers for the application code, dependencies, and environment configurations.
4 expert tips for securing your data center
Bearing in mind the increasingly spread out and hybrid nature of modern data centers, monitoring operations and guaranteeing high levels of security can prove challenging. Here are four tips to meet those challenge head on.
1. Take obsolete software seriously
Neglecting to scrutinize data centers for software components that are no longer maintained or updated by the original developers is a big security risk. Legacy software may be intertwined with many functionalities that the data center depends on. In some cases, the firmware that’s embedded in data center computer systems can become obsolete.
One contributing factor that leads companies to downplay the risks is that they don’t want to disrupt critical workflows and apps while they replace obsolete software with an alternative. Downtime can be incredibly expensive to the point that some organizations have zero tolerance for any downtime at all. This lack of downtime tolerance can override security concerns and their seriousness.

Another factor is that some companies don’t even realize their data centers are rife with outdated and risky apps for which updates are no longer available. A prime example is Adobe Flash, which despite hitting its end of life in January 2021, is still regularly found in data centers, where it’s used to present device management information.
An action plan for taking obsolete software seriously must start with screening all data center software assets to identify any firmware and software that might be at their end of life. Instead of relying on old inventories that could themselves be outdated, start a new audit.
Seeking out alternatives to upgrade to and enacting an upgrade plan can be the next step after identifying obsolete code. However, if there are no upgrade options, you may need to isolate systems containing obsolete software inside a demilitarized zone (DMZ) to stop malicious actors from targeting vulnerabilities.
2. Find and fix cloud misconfigurations when developing IaC
With DevOps teams having such an important role to play in cloud security, designing cloud architectures that are inherently secure means finding and fixing misconfigurations of cloud services. Human fallibility can readily lead to errors when managing and provisioning computer data centers through machine-readable definition files (infrastructure as code). Other risky misconfigurations may arise when interacting manually with the control plane of cloud services.
Tips for DevOps teams to secure cloud architectures include:
- Full visibility into cloud environments and software development life cycles. It should be straightforward to see what’s running, how it’s configured, how it’s developed and deployed, and to track changes.
- Integrate secure by design principles into the entire cloud SDLC and environment architectures so that you stand the best chance of finding or preventing misconfigurations.
- Use developer-friendly security tools that don’t get in the way of DevOps workflows. Security tools should provide fast and actionable feedback on misconfigurations without causing slowdowns or bottlenecks in development processes.
- Adopt policy-as-code to align DevOps teams on a single source of truth for cloud security with defined rules and conditions that help to reduce human error and automate decision-making.
- Always strive to measure risks, improve processes, and automate where possible so that the security configurations are less prone to manual errors.
3. Apply patches to systems ASAP
It’s not just obsolete software that presents security risks. Organizations often fall behind or fail to implement an effective patch management program, which puts their data center systems, workloads, and applications at risk. Firmware, server operating systems, mission-critical applications, libraries, and frameworks can all become vulnerable when they don’t get updated on time with the latest security patches.
Aside from the importance of having an up-to-date inventory of all code assets, make sure to scan for vulnerabilities, perhaps as part of a dedicated network vulnerability assessment. Ideally, have some kind of automated solution that reduces the dependence on manual patch deployment.

4. Protect the data itself, not just the data center
While data centers do far more than just store important data, information assets are ultimately one of your most valuable resources. Extra measures focusing on data security rather than just data center security can also prove useful.
In particular, consider the following:
- Encrypt data when stored at rest and in transit across your data center ecosystem
- Enforce granular access control policies that minimize user permissions and resource access to only what’s strictly required for their jobs
- Scan cloud Big Data lakes for security blind spots, such as open storage buckets.
Get more Big Data security tips here
Automatically reinforce and maintain infrastructure security
Data center security may have changed significantly in a short time span, but its importance hasn’t dwindled. In providing shared access to your most crucial data and applications, your data center is a prime target for increasingly voluminous and sophisticated cyber threats.
Securing the data centers of the present and the future must account for the role of DevOps teams, particularly how they can introduce automation to reinforce and maintain infrastructure security. Spectral is a developer-first security solution with hundreds of detectors to help you continuously scan and monitor code, configuration, and binaries in your environment for security weaknesses.
We respect your CI, so Spectral works rapidly (an average-sized repo takes only seconds to scan) to secure your hybrid data center infrastructure without the burden of slowing down development. Learn more here.
The post 4 Expert Tips for Data Center Security appeared first on Spectral.
*** This is a Security Bloggers Network syndicated blog from Security boulevard - Spectral authored by Eyal Katz. Read the original post at: https://spectralops.io/blog/tips-for-data-center-security/



