Synopsys Action introduces GitHub Actions integration for developers
GitHub Actions integrates AST capabilities into development workflows and CI/CD pipelines to provide instant, actionable insights into risks.
Today, the nature of technology and its accelerated time to market require organizations to extend security practices to development and engineering teams. Security teams retain their role as central observers of security risk posture while also becoming coaches and advocates of best practices to those further left along the software development life cycle (SDLC) and continuous integration / continuous delivery (CI/CD) pipelines. These teams favor fast, lightweight, inline solutions over large, heavyweight security solutions that cause deviations from established workflows.
That means application security testing (AST) tools—such as those analyzing code (static application security testing (SAST) and open source software (software composition analysis (SCA)—need to be integrated in multiple points along DevOps workflows and CI/CD pipelines.
Securing code in GitHub with integrated tools
Setting aside early linters, the first generation of modern SAST and other testing tools focused primarily on generating relevant, actionable results with a good signal-to-noise ratio. While this is still important, most tools have evolved to the point where they are adequate at minimizing risk exposure across the software landscape of an average organization.
While the quality of results remains an important factor in the success of an AppSec program, a new focus has emerged in making the tools work for developers: incorporating security risk awareness into development toolkits instead of making developers go to the testing tool. This new focus is due to the increased security responsibilities being placed on development and engineering teams, in addition to their main role of quickly producing reliable, resilient software. Development teams get the most value from solutions that fit natively into their existing workflows, without proprietary interfaces or workflows that negatively impact release velocity.
To accomplish this, security testing tools must be able to function natively with one of the most prominent and capable DevOps tools: GitHub.
Why GitHub Actions are essential for DevSecOps
It is not an understatement to say that Git revolutionized how source code management is done. Unlike centralized version management systems, Git branches are cheap and easy to manage. Today, pull (or merge) requests are the norm, and peer code reviews have become standard operating procedure for many. For many software organizations, GitHub has become a catalyst for change among application security testing tools.
Extracting and delivering the right information, at the right time, directly into the hands of developers operating within the GitHub ecosystem is often best achieved with GitHub Actions. GitHub Actions provides the ability to configure automated or manual processes that fit smoothly into CI/CD pipelines. Synopsys preconfigured GitHub Actions integration, Synopsys Action, allows development teams to integrate AST capabilities into their development workflows and CI/CD pipelines. For developers, this means a single entry point for development activities and security responsibilities, only one integration to configure, and a consistent look and feel with their native tools and workflows.
The primary challenge we set out to solve with Synopsys Action was making application security testing a native part of the pull request workflow, automatically performing fast and deep analysis of source code, open source components, infrastructure-as-code (IaC) templates, APIs, and binaries. To achieve this, Synopsys solutions needed to provide feedback to developers as though it came from a peer code review, with clear and actionable insight, and without deviating from established development workflows. Synopsys Action provides developers with instant feedback about issues that would either require refactoring at later stages or become risks in production.
How to use GitHub Actions to run security tests with Synopsys
Developers expect that by the time they receive feedback from peer review or the decision-maker inspects a code change, security testing findings will be annotated so informed prioritization and remediation can occur. Synopsys Action meets this expectation and provides actionable feedback on risks and remediation guidance in code review comments, effectively functioning as an automated peer code review. It’s important to note, for many focused on unobstructed DevSecOps, that this is not required to be a gate that imposes itself on workflows. It is, however, possible to configure Synopsys policies for automatic enforcement based on failure to adhere to security risk tolerances.
In the step-by-step breakdown, we examine a developer workflow using Synopsys Action in GitHub to find and fix security issues in code.
Configuring GitHub Actions to find security issues
Synopsys Action is easily set up and deployed in workflows like other GitHub Actions. Here is an example configuration code snippet of using it with Polaris Software Integrity Platform®.
- name: Synopsys Action
uses: synopsys-sig/synopsys-action@<version>
with:
polaris_serverUrl: ${{ secrets.POLARIS_SEVER_URL }}
polaris_accessToken: ${{ secrets.POLARIS_ACCESS_TOKEN }}
polaris_application_name: "testapp1"
polaris_project_name: "testproj1"
polaris_assessment_types: "SAST"
Security risk analysis at code check-in
When a developer checks in code, performs a pull request, or performs a post-merge push, some form of security analysis occurs (e.g., SAST, SCA). This analysis can be understood as a “delta scan,” enabling rapid analysis of only what changed during the development branch, as opposed to a lengthy scan of the larger body of work. Synopsys testing tools generate results describing potential security or quality issues within the code and offering insight on how to fix them. These results are presented in pull requests within GitHub.
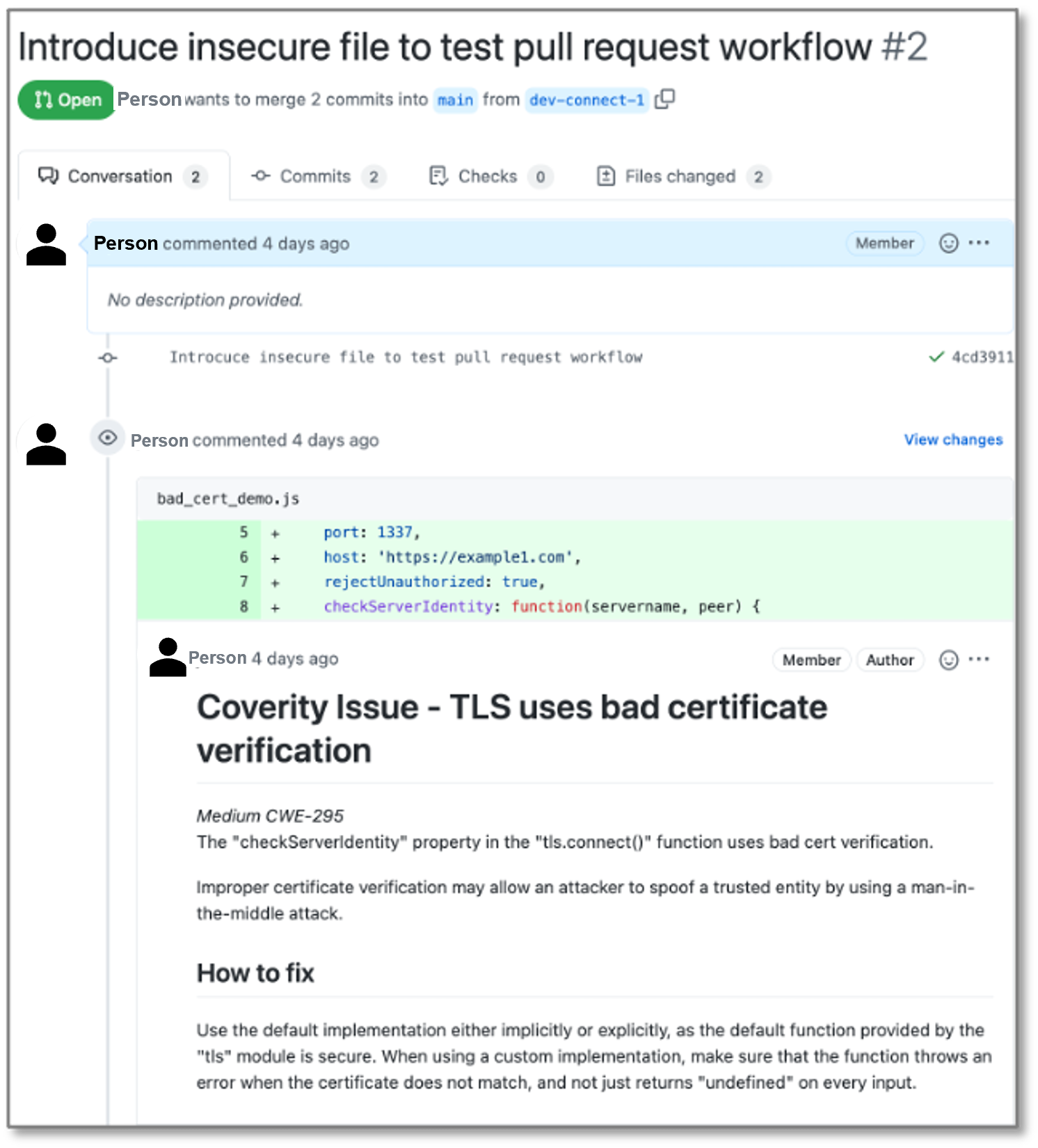
When run on a pull request, actionable feedback is provided to the developer as code review feedback on their change.
When run on a pull request, actionable feedback is provided to the developer as code review feedback on their change.
Security policies can be enforced
If policies are configured within the Synopsys suite of AST solutions, software artifacts and code changes that violate policy are identified in pull requests within GitHub.
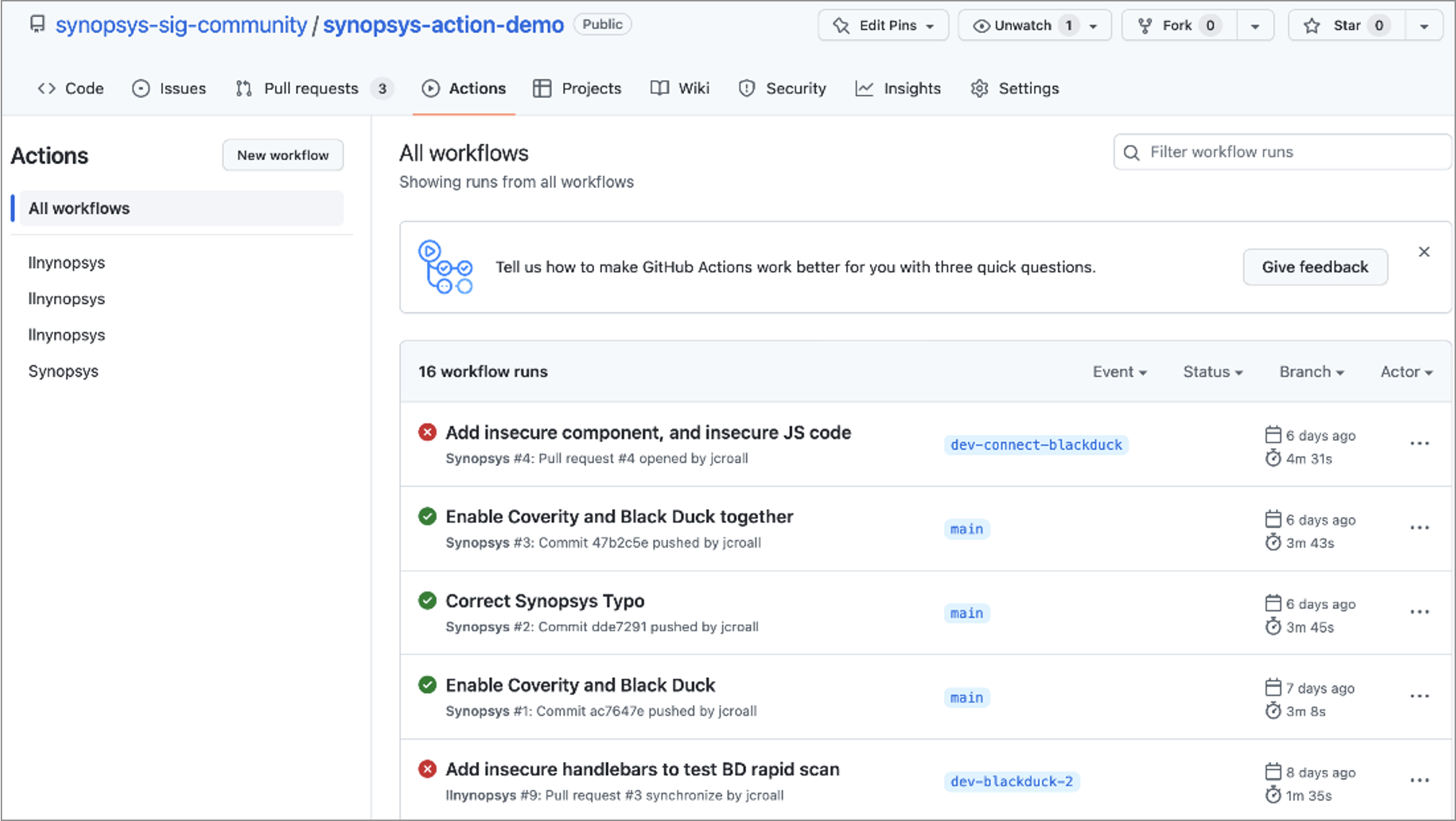
Use Synopsys Action today
Whether you are on development or engineering teams or part of security and DevOps teams, Synopsys Action is available for use today from the GitHub Marketplace. If you are a current user of Synopsys solutions, you may perform SAST and SCA using Synopsys Coverity®, Synopsys Black Duck®, and Synopsys Polaris as part of your GitHub workflows today.
*** This is a Security Bloggers Network syndicated blog from Application Security Blog authored by Steven Zimmerman. Read the original post at: https://www.synopsys.com/blogs/software-security/synopsys-action-github/





