Misdelivery: The Often Overlooked Data Security Threat
According to the Verizon 2022 Data Breach Investigations Report (DBIR), 22% of the investigated security incidents in 2021 resulted in a data breach. One data breach that figures prominently in this report is “misdelivery.” A misdelivery occurs when a user sends personally identifiable information (PII) or protected health information (PHI) to an unintended recipient via email or other communications channel.
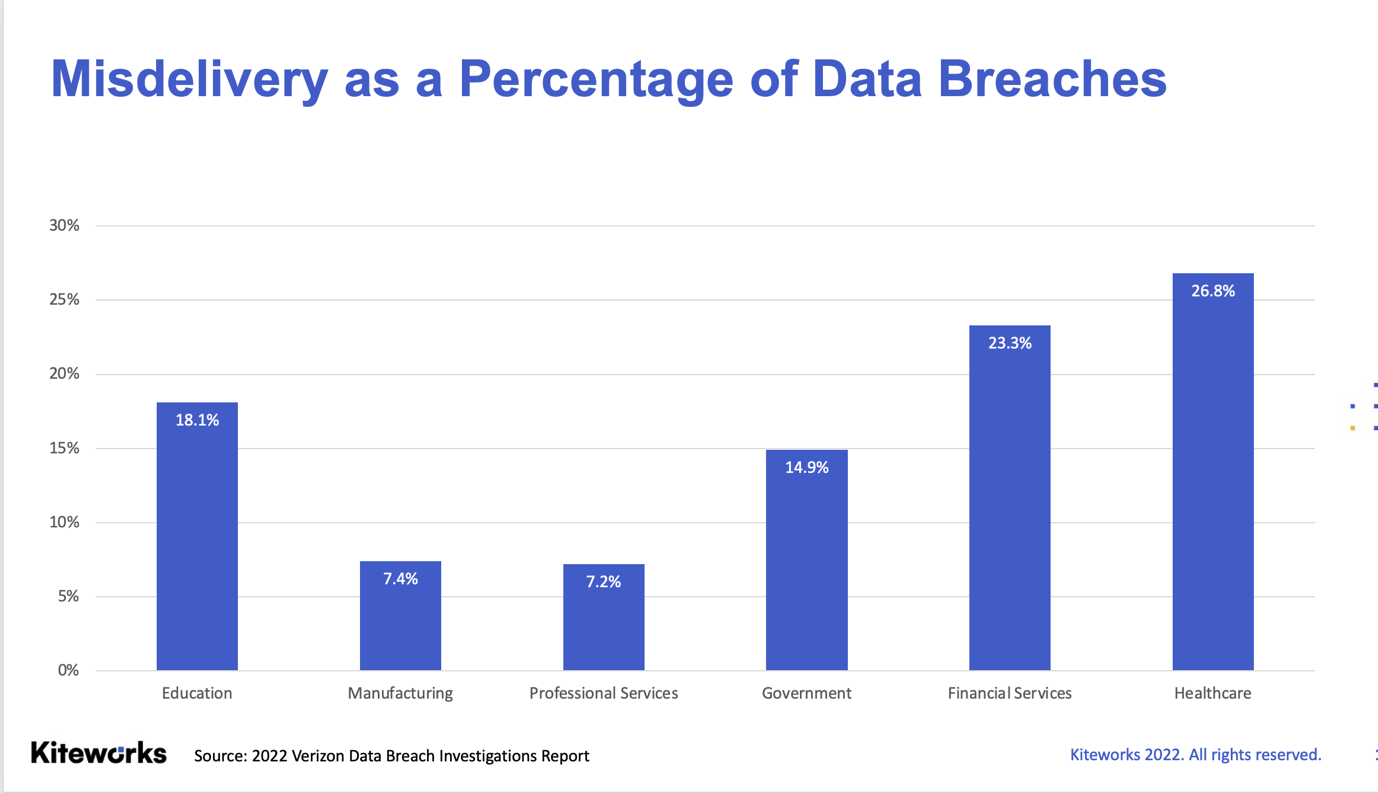
Misdelivery played a role in 715 incidents, 708 of which resulted in a data breach. This means that 13.5% of all data breaches involved someone accidentally sending sensitive information to the wrong recipient!
What Is Misdelivery?
To be clear, misdelivery is a data breach. The absence of malice is irrelevant; once sensitive information intended for authorized users has been delivered to an unauthorized recipient, the damage is done. Unfortunately, with so many people working remotely, the risk of misdelivery is higher than ever. Why?
First, employees are rarely in the same office anymore, so they have to communicate over email and collaboration tools. Second, many are suffering from notification overload. Between Teams or Slack, email, and text, it’s easy for employees to get overwhelmed and inadvertently share data with the wrong person.
It’s Probably Already Happened to You
Some industries are more susceptible to misdelivery than others. Employees in Financial Services, for example, are three times more likely to share sensitive information erroneously, according to the Verizon 2022 DBIR.
Financial Services firms, and Professional Services firms more broadly, typically have large client bases and therefore extensive and frequent client communications. It’s not uncommon for an employee in a client relations or consulting role to send up to a hundred emails every day to clients, colleagues, and partners.
While Healthcare led other key industries in misdelivery incidents in 2021, the number of incidents actually declined relative to previous years. By contrast, misdelivery increased in these other industries over the same time period.
In their haste to provide exemplary customer service, these employees occasionally send proprietary and sensitive information to the wrong recipient, either by email or through shared folders. Email cache and auto-fill unfortunately increase the likelihood of misdelivery significantly.
An employee types “Jan” in the email “To” box or “Share With” within a file sharing application with every intention of sending a contract to Jan Vincent but Jan Valentino auto fills the box instead. The names are so close that it’s easy to overlook; easy but costly.
When misdelivery of sensitive information happens, it usually leads to a data breach. A data breach can cost an organization millions in lost revenues and litigation. Worse, customer churn and brand erosion typically follow.
Best Practices to Mitigate the Risk of Misdelivery
By applying the following practices and solutions, employees can mitigate the risk of a misdelivery-related data breach:
Update corporate security policy
Any organization’s security policy should clearly outline how to handle critical data, who can access it, and how to share it externally (if and when needed).
The use of a data loss prevention (DLP) solution, for example, is very important. DLP incorporates technology but also policies and procedures to help prevent data leakage, including misdelivery. It helps organizations mitigate other insider threats like theft and sabotage. It also helps organizations monitor critical file movements and demonstrate compliance with data privacy regulations and regulatory standards.
Use the principle of least privilege
Using zero-trust security to build, maintain, and utilize an IT system is a very secure approach to protecting sensitive content from unauthorized access.
Zero-trust security can be loosely defined as a design practice that requires system users to be authenticated, authorized, or continuously validated prior to accessing a system that holds or handles sensitive information. Access is privileged and granted on a case basis. Zero-trust security significantly mitigates the risk of unauthorized access to an organization’s PII, PHI, or intellectual property (IP).
Offer regular training
Technology is in a state of constant advancement. Unfortunately, so is cybercrime. Organizations and their employees must therefore keep up with changes in both arenas to stay competitive as well as protect their organization’s intellectual property.
Humans need not be the weakest link in data protection. Providing employees with periodic trainings for data storage and file transfer management solutions can help employees stay up to date with evolving systems and technologies, as well as minimize the risk of unauthorized access, like misdelivery, that could result in a data leak.
Consider managed file transfer
Managed file transfer (MFT) centralizes many of the features and protocols of other file sharing mechanisms into one platform for secure, efficient, and legally compliant file transfers across an organization or between organizations.
Furthermore, MFT platforms are designed in such a way that they ensure compliance with relevant regulations such as Health Insurance Portability and Accountability Act (HIPAA), General Data Protection Regulation (GDPR), Payment Card Industry Data Security Standard (PCI DSS), and Gramm-Leach-Bliley Act (GLBA). When organizations automate their file transfers, they minimize the risk of human errors, such as misdelivery, that can lead to a data breach.
Prevent Misdelivery-related Data Leaks With Kiteworks
Organizations mitigate the risk of misdelivery whenever they share PII, PHI, IP, or other sensitive information using the Kiteworks private content network (PCN).
If an employee accidentally emails a file to Bill Smith rather than Bill Smithers using Kiteworks secure email, the employee can withdraw the file before Bill Smith accesses it. In the event multiple files were sent, the employee can choose which files to remove.
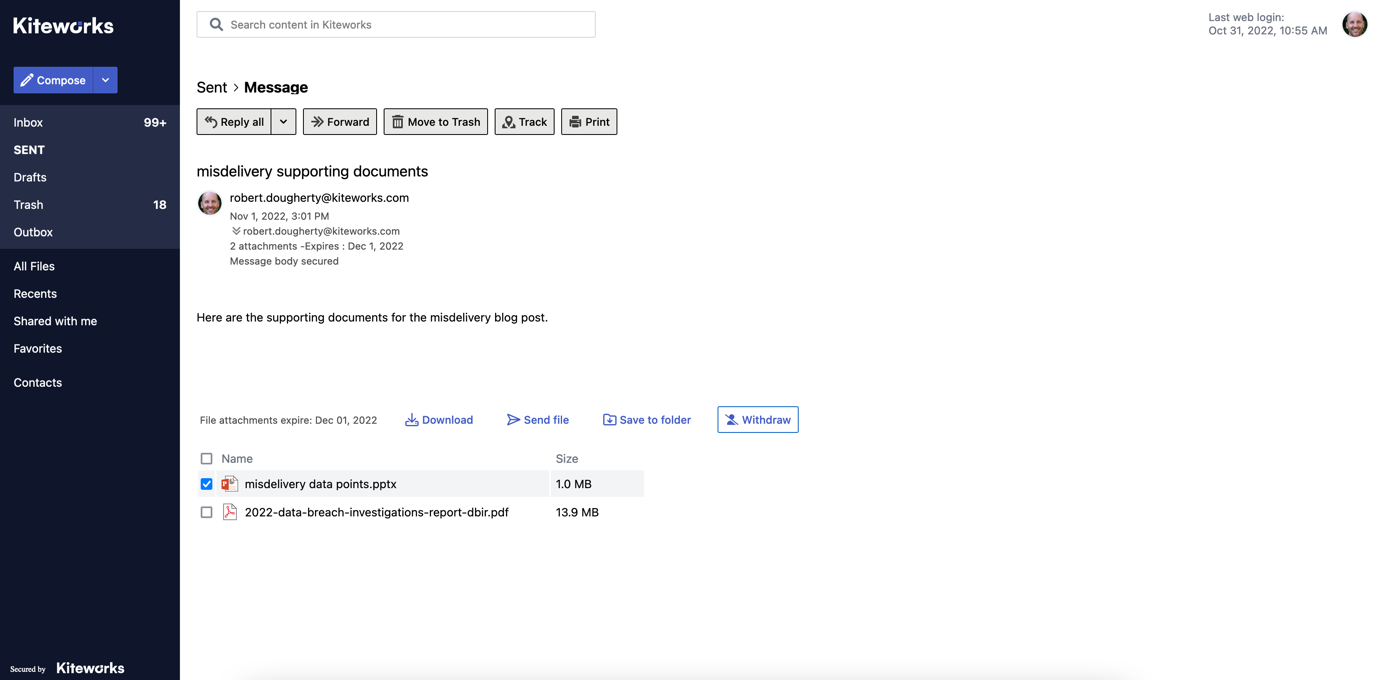
If an employee accidentally sends files to an unintended recipient using Kiteworks, s/he can withdraw and remove the file in question with just a few clicks. (source: Kiteworks)
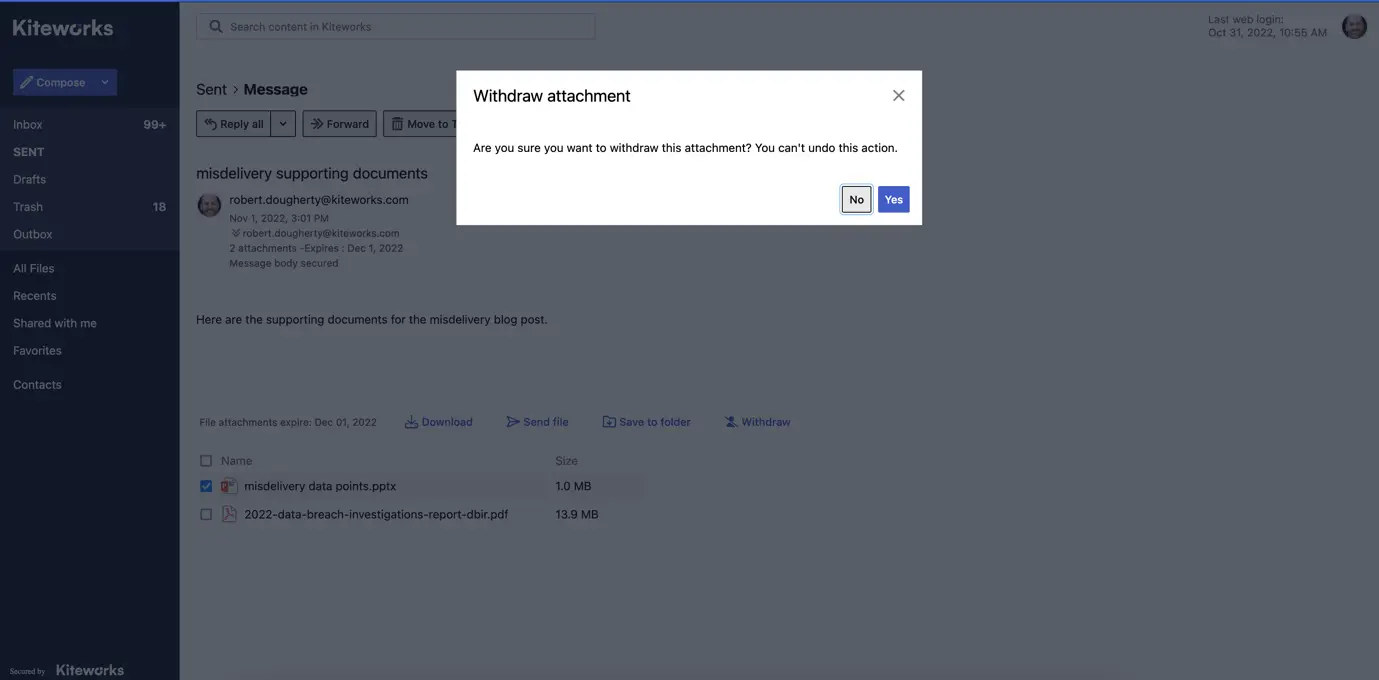
The Kiteworks user is then prompted to approve the file removal. (source: Kiteworks)
Kiteworks secure file sharing also gives users the control to set and change who has access to sensitive content. If an employee invites Michael Johnson instead of Michelle Johnson to access a folder containing sensitive files about a pending merger, the employee can revoke Michael’s permissions, preventing Michael from accessing any of the files in the folder.
Final Thoughts
The Kiteworks PCN protects organizations’ most sensitive content whenever employees share it externally, even in the event an employee sends that information to an unintended recipient. The file and recipient withdraw capabilities in secure email and secure file sharing, respectively, ensure organizations’ PII, PHI, and IP stay private at all times.
With Kiteworks, organizations also:
- Unify secure content communication channels like email, file sharing, SFTP, MFT, and web forms. This includes natively extending standard email clients to promote a seamless user experience and protect every email containing sensitive content sent through these clients.
- Track content, metadata, user activity, and system events to boost security operations center (SOC) effectiveness, report on third-party access, and easily meet regulatory compliance reporting requirements.
- Control content access and functional rules matched to risk profiles and user roles. Leverage centralized administration to protect content in emails, web forms, MFT, and secure file sharing for comprehensive governance and compliance with internal and external audits.
- Secure data through encryption of content at rest and in motion and integrations with single sign on (SSO), multi-factor authentication (MFA), anti-virus (AV), advanced threat protection (ATP), and data loss prevention (DLP), to mitigate the risk of unintended exposure of sensitive information, like misdelivery.
Additional Resources
- Blog Post Prime Cyber Targets According to the 2022 Verizon DBIR
- Blog Post What Is Email Security? How To Protect Your Enterprise Email
- Blog Post Evaluating Sensitive Content Communications Through the Lens of Data Breach Costs
*** This is a Security Bloggers Network syndicated blog from Cyber Security on Security Boulevard Archives - Kiteworks authored by Robert Dougherty. Read the original post at: https://www.kiteworks.com/cybersecurity-risk-management/misdelivery-the-often-overlooked-data-security-threat/