Is Dark Web Monitoring Vital? How does it work?
The recent data from August 2022 states that 97 Million Records are breached in the cyber world. These stats are quite alarming because according to the survey we can feel that nothing is safe in the online world. Even the top search engine Yahoo once had a significant data breach with 3 billion user accounts. It’s one of the largest data breach cases we have seen.
But have you ever thought about where this leaked data ended up? It all goes to the dark web where all the lost data is put up for sale and all this data then gets under the control of buyers. They can only access them. As a result, private data gets public and possess significant risks. Fraudsters can use this data to commit financial fraud and identity theft, among other things.
So, continue reading this blog and get detailed insights about the dark web, how it works and how you can protect your data from identity theft.
What is Dark Web Monitoring?
The dark web is a part of the internet with no IP addresses, no domain names, and is not searchable on Google. The only way you can access this hidden part of the internet is through an encrypted browser called TOR. It’s also known as the darknet or deep web.
Many popular websites exist only on the dark web, such as Silk Road, a black market for illegal drugs which closed in 2013 after the FBI took it down and arrested its founder Ross Ulbricht. A popular site today is Dream Market, created by drug dealers in 2016 because they were dissatisfied with the closure of Silk Road.
People use Tor because they want to remain anonymous from surveillance from their government or other organizations. One example would be whistle-blowers who reveal essential information about corruption within large corporations.
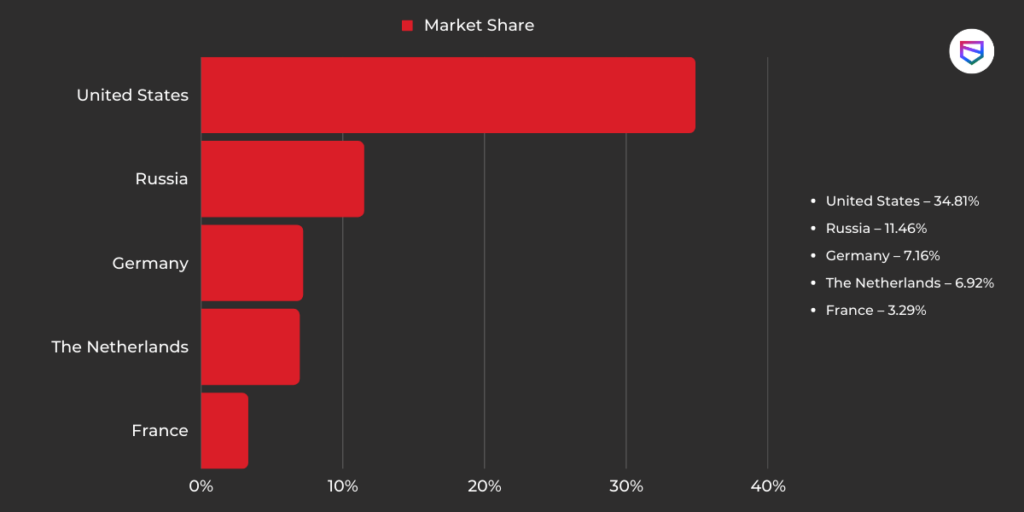
The dark web has 2.5 million daily active users accessing underground sites. It accounts for only 6% of the internet which it shares with the surface net and deep web. More and more citizens are lured by the opportunities that lie in this hidden cyberspace. Here is a list of top dark web users per country and their respective market shares:
What Type of Data Do Dark Web Monitoring Tools Look For?
Below is a list of the types of personal information that dark web monitoring tools usually look out for:
- Financial records (such as bank account numbers and credit card statements)
- Passwords
- Credit/debit card details
- Social security numbers
- Medical records and identification numbers
- Phone numbers
- E-mail addresses and passwords
Exposing such data types can cause significant damage to individuals.
How Does Dark Web Monitoring Work?
Dark web monitoring tools continuously scan through the websites and online forums that hackers often use to trade or share stolen private information. They depend on various processes to explore the dark web for data, which includes scanning, scraping, and crawling.
Dark web monitoring tools primarily seek to match a user’s personal information with the data on dark web databases. If there’s a match, the user receives an alert.
These web monitoring tools have evolved, and many great options exist. The best dark web monitoring tools available today are mainly automatic. They constantly scan for leaked online data and send actionable alerts.
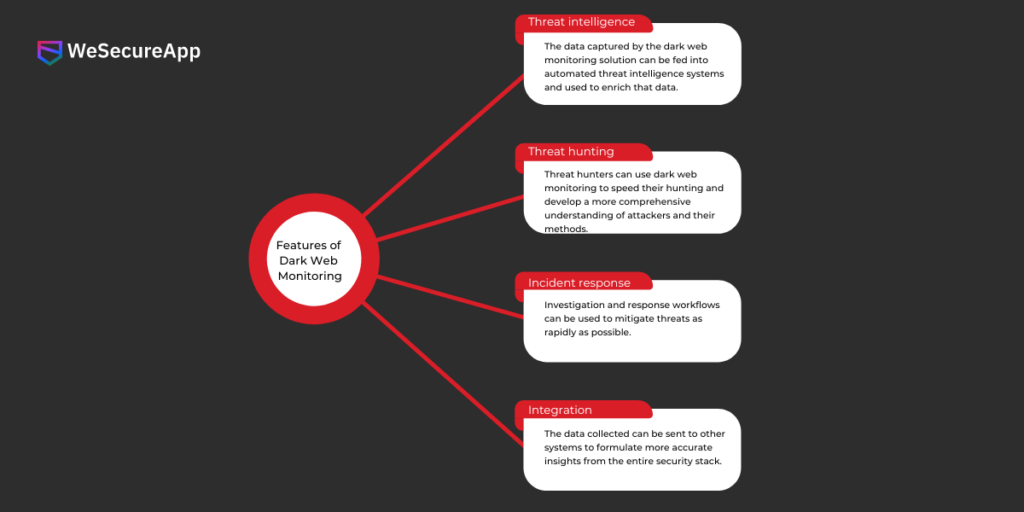
Features of Dark Web Monitoring
Tips for Keeping Your Private Information Off the Dark Web
1. Use a Strong Password
To stay safe online, it’s essential to use strong passwords. Weak passwords are easily hacked and can give criminals access to sensitive information, like bank account numbers and social security numbers.
Password strength is based on how long the password is, how many different types of characters it has (letters, numbers, symbols), and how easy it is to remember. Generally speaking, a password should have at least eight characters and a mix of letters, numbers, and symbols. Keep in mind that you’ll need to make your password memorable, so you don’t forget it or store it somewhere insecure.
2. Regular Password Updates
Identity Watch provides a variety of ways to keep your information safe, but one of the most important is using a strong password. Using strong and unique passwords for each website or service can avoid phishing scams and hacking attempts on your accounts. Plus, by updating your passwords regularly (every 90-120 days), you are reducing the likelihood that someone could find out if they were somehow able to access any of your passwords.
The last step in our three-step security strategy involves keeping your information as private as possible. Privacy settings allow you to restrict what other people can see about you so only people who need to see it will be able to access it.
3. Use VPN Services
VPN Services offer a great way to protect your identity and stay safe online. VPNs encrypt all of the data in your connection, so hackers or other malicious actors cannot intercept it. It also bypasses content filters and firewalls, which can help you get around geographic restrictions on content.
For example, if you want to watch U.S. Netflix while traveling abroad, simply connect with a VPN server based in the U.S., and watch as Netflix lets you log in without any issue whatsoever! There are many free options available for this service – such as Hotspot Shield – but we recommend investing money into a paid service that offers high speeds and unlimited bandwidth for use with multiple devices simultaneously.
4. Visit Secure Websites
Secure Websites offers a variety of Dark Web Monitoring Services with Identity Watch. These services monitor your personal information, such as credit card numbers, social security numbers, and any other sensitive data that you might have in your possession. This way, you can be assured that it is not stolen from you or used in fraudulent activities.
5. Report Suspicious Activity
Identity Watch provides users with dark web monitoring and alerts you when their personal information has been found online. This allows you to either alert the company or delete your account, which will protect your identity. There is no need for anyone to fear an active cyber-attack on their accounts. You can stay safe by knowing how it is used against you and taking these steps.
Conclusion
Ultimately, the dark web can make or break your identity if you haven’t followed the right security measures. Better to keep your data safe from this dark web or consult an expert to guide you better – Contact Us
Recommended Reading
Top 5 Myths Of Cyber Security Debunked
Devil for Modern Security: RANSOMWARE
Social Engineering Attacks – Manipulating your thoughts to fall in trap
The post Is Dark Web Monitoring Vital? How does it work? appeared first on WeSecureApp :: Simplifying Enterprise Security!.
*** This is a Security Bloggers Network syndicated blog from WeSecureApp :: Simplifying Enterprise Security! authored by Mahima Jaiswal. Read the original post at: https://wesecureapp.com/blog/is-dark-web-monitoring-vital-how-does-it-work/




