How Information Stealers Get User Credentials
Throughout 2022, the theft of user credentials continued to blanket the threat landscape. A recent example that illustrates both the simplicity and depth of this tactic is the Uber breach by threat actor Teapot. They bought the illegally harvested user credentials on the Darknet Marketplace (DNM). They then used the stolen credentials to social engineer their way into Uber’s network via an MFA (multi-factor authentication) exhaustion attack.
While Uber certainly isn’t the only credential theft victim out there, their situation highlights a theft process and how threat actors use stolen credentials. Many think cybercrime is a single-sourced operation, but that’s rarely the case. Behind most compromises is an extensive criminal network that includes, among many threat actors, initial and wholesale access brokers who harvest and sell user credentials. This, in turn, fuels additional crimes down the road.
Credential Theft
Threat actors use credential access (TA0006) to acquire user credentials. There are several techniques used to gain access to valid user credentials, such as credential harvesting from password stores (T1555), web session cookie theft (T1539), or the finding of unsecured credentials (T1552). Once acquired, threat actors can log in and access secure networks with minimal detection by leveraging legitimate credentials.
Behind this activity stands a booming underground economy where threat actors buy and sell compromised valid credentials harvested from information stealers. Information stealers are malware that gathers information, such as user credentials from infected devices. Offerings for information-stealing malware range from standalone software packages to full-blown, malware-as-a-service platforms.
Phishing attacks are often the distribution system of choice for information stealers. In them, the threat actor attempts to social engineer users into downloading and deploying a malicious payload. It’s usually accomplished via emails containing malicious attachments. It is conducted via third-party services, as well, such as social media platforms and compromised websites.
Raccoon Stealer
Raccoon Stealer is an information stealer that harvests personal information from compromised devices, including system information, usernames and passwords stored in browsers, Discord session files, credit card information, autofill data and crypto wallets. It also can serve as a loader for additional malicious payloads. Raccoon Stealer is sold as-a-Service via Russian forums for $150 a day or $275 a month. There are options if additional features are needed.
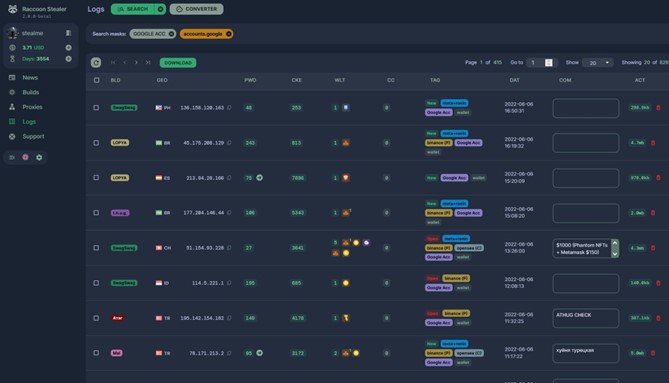
A Recent Raccoon Stealer Example
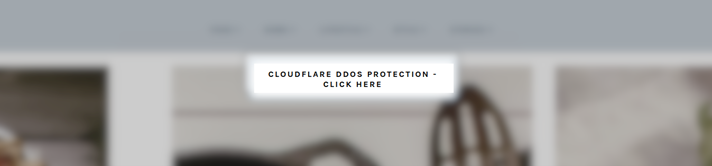
Cybersecurity company Sucuri recently reported that threat actors are using fake Cloudflare DDoS protection prompts to deliver malicious payloads. They’re leveraging a JavaScript injection to target vulnerable WordPress websites to display fake DDoS prompts. Once a user clicks on the prompt, a malicious .iso file downloads, and a new message attempts to further social engineer the user into opening the file containing a NetSupport Remote Access Trojan. This, in turn, deploys Raccoon Stealer.
Redline Stealer
Redline Stealer is another information stealer that harvests personal information from compromised devices, including system information, usernames and passwords stored in browsers, credit card information, autofill data, VPNs, and FTP/IM client data. Customers can also customize a grabber by path, extension, and search. Redline Stealer sells as a monthly subscription service for $100, or $200 for a standalone license. Hacker forums make cracked versions of Redline easily available.
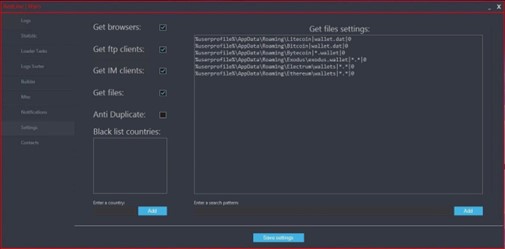
A Recent Redline Stealer Example
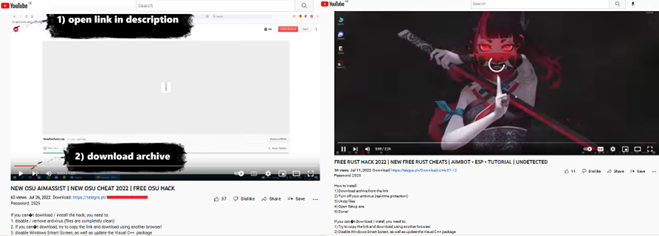
SecureList by global cybersecurity company Kaspersky recently reported on a threat actor that leveraged RedLine to target gamers via YouTube lures. The attack consisted of a RedLine payload hidden inside a malicious file advertised as being about cheats and cracks in a video description. Once infected, the malicious, self-propagating file posts a video to the infected user’s YouTube channel and links to a password-protected archive with a malicious file containing RedLine.
Sadly, It’s A Thriving Underground Economy
Once a threat actor has successfully deployed an information stealer and harvested compromised valid credentials, they often go to their darknet marketplace of choice and sell the logs. Log prices can range from one dollar to several hundred. The price usually reflects the quality of the logs. For example, logs with corporate VPNs, RDPs, CMS gateways, web applications and email services rank the highest and pull in the most money.
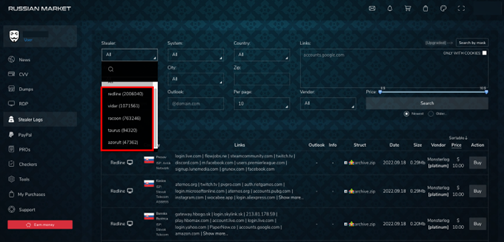
Today, acquiring stolen credentials is far too easy. Buyers can simply create an account and search for stealer logs on various marketplaces. Logs can be filtered for data related to specific types of information stealers, operating systems, counties, corporate links, and more. Stealer logs for sale on the Russian market range from $1-$10 and provide purchasers with cookies and autofill data from browsers, system information, infected users’ passwords, and more.
The Future of Information Stealers
Information stealers that harvest valid user credentials are a major component of the underground cybercrime economy. With nearly a dozen information stealers currently in operation, and potential log buyers ranging from ransomware affiliates to corporate spies, organizations need to extract and leverage actionable intelligence from recent events. Learning from breaches like the one that affected Uber is a great example of how to reinforce your organization’s defensive posture.
As mentioned, credential theft is showing no signs of slowing down. Here’s the thing — it won’t, ever. Sadly, stolen credentials sold on darknet markets are very lucrative. If you want to learn more about the digital underground economy related to credential access, join Radware and CyberSixGill for a special webinar on December 15. In it, we’ll dive into the known forums and marketplaces that sell information stealers and compromised valid credentials.
Credential Access and Impacts Down Range:
BrightTALK: NAM + EMEA
BrightTALK: APAC
*** This is a Security Bloggers Network syndicated blog from Radware Blog authored by Daniel Smith. Read the original post at: https://blog.radware.com/security/threat-intelligence/2022/11/how-information-stealers-get-user-credentials/





