API Protection and Cloud-native Application Protection Platforms (CNAPP)
Security Solutions for APIs and Cloud Applications
Organizations have gained many benefits by developing applications in the cloud that include flexibility, agility, scalability, and speed – but it’s also created security problems that are not easily solved by just any one solution. These problems become more complicated when considering APIs, which are the glue that make mobile and web applications work. APIs, which by their nature are highly visible and well-defined doorways into the data and business processes of organizations, are now the number one attack surface exploited by cyber criminals. Even the most compliant and secure APIs can be exploited by attackers in the form of business logic abuse and automated threats resulting in data loss, fraud, and business disruption.
CNAPP for DevOps Teams
While a new category of cloud security vendors named CNAPP (Cloud-native Application Protection Platform) by Gartner will provide some coverage for application security such as scanning application code for OWASP vulnerabilities and enabling DevOps teams to remediate security issues, API protection solutions deliver a different set of capabilities. Together, these solutions provide organizations a complementary approach that can reinforce their overall cloud native security, and API and application security posture.
CNAPP – Focusing on Cloud Native Application Security
When looking at cloud security for applications deployed in the cloud, it’s important to consider that an application will require different components such as virtual workload, data-store, network, and identity services that are used to support its function in the cloud. These components and the effort to secure applications deployed in the cloud have created a patchwork of security solutions resulting in a disjointed and complex deployment that lacks a centralized view (management?). The lack of a unified view means customers are presented with isolated silos of information leading to blind spots between different security products that could potentially enable attackers to exploit your application or infrastructure.
CNAPP – Cloud Security Challenges
The goal of CNAPP solutions is to simplify the underlying complexity of existing cloud security products by combining the functionality of existing products such as Cloud Security Posture Management (CSPM), Cloud Workload Protection Platforms (CWPP), Cloud Infrastructure Entitlement Management (CIEM), and Cloud Service Network Security (CSNS) into one solution. CNAPP offerings are geared towards addressing the following cloud security challenges:
- Increased Management Complexity: As the cloud has become more complex, a variety of security products have been deployed to lock down various segments of cloud infrastructure that are vulnerable to exploits, complicating day-to-day management.
- Security Blind Spots: The disparate and fragmented nature of deployed cloud security products has resulted in security blind spots and loss of visibility across cloud deployments, making it difficult for security and DevOps teams to understand where they are vulnerable.
- Cloud Misconfigurations: Constant changes often lead to human error that can result in misconfigurations of security groups, ACLs, network and security policies, mistakes that can lead to exploitation. Identifies deviations from desired security posture that include identifying vulnerable components, unused workloads, identify areas of application misuse and attack.
- DevOps Productivity: Increasing developer and DevOps team productivity by identifying misconfigurations and potential threats in the CI/CD pipeline phases, reducing the number of bug fixes and merge/pull requests.
- Vulnerability Testing: Performing periodic security scans across cloud components such as containers, serverless environments, and VMs to preempt any security issues that can be missed or exploited
API Protection Capabilities that Complement CNAPP
While a CNAPP approach can provide a unified view between different security products that could potentially prevent attackers from exploiting your application or infrastructure, protecting APIs requires a different approach. The following are some of the areas for providing API protection that complement CNAPP to help secure and defend against cyber-attacks that target API-based and cloud-native applications.
- Real-time Threat Detection & Mitigation: An API protection solution will accurately detect and mitigate malicious traffic with industry leading, high efficacy rates. This ensures that business critical transactions are processed without any risk of being blocked due to inaccurate threat detection. This complements CNAPPs by ensuring real-time threat detection and mitigation for organizations who require their applications to have real-time API protection for applications that might be accessible to malicious entities.
- Shadow API Discovery: The greatest threat to organizations are unknown APIs used by applications deployed by internal groups but who never notify the security team of their existence. These APIs may have vulnerabilities that have not been corrected and can be a quick and easy target for cybercriminals. This discovery capability complements CNAPP, helping protect unknown APIs and cloud components while CNAPP focuses on known applications and cloud infrastructure.
- Rapid Application Code Changes: API applications deployed in the cloud often adhere to agile development methodologies that constantly introduce changes to API specifications that if not monitored can lead to compliance or data exposure issues. OWASP API Security Top 10 vulnerabilities that are introduced during the development cycle can be potentially exploited by attackers. This requires constant inventory and compliance checks to identify and mitigate the vulnerabilities before they can lead to exploitation. Rapid application changes that can lead to deviations from an original API specification that can introduce vulnerabilities that can be exploited by cybercriminals are not something provided by CNAPP approaches.
- Direct Access to Sensitive Data: API endpoints tend to have direct access to sensitive data stored in the backend of applications. An API endpoint containing an OWASP API Top 10 vulnerability might be compromised by a cyber-attack that can lead to direct access to sensitive data. Since API applications are constantly changing, this is a never-ending problem that requires constant monitoring. API protection solutions can surface sensitive data access providing insight into how API endpoints access data in the backend. This is a critical piece in protecting any API applications since sensitive data is often the ultimate target of cybercriminals.
API Protection and Six Stages of Continuous API Lifecycle
When it comes to protecting APIs, an API protection solution should address each of the six stages of a continuous API lifecycle. By addressing these stages, security teams can ensure a unified approach to API protection, that most effectively complements a CNAPP solution.
API protection solutions such as the Cequence Unified API Protection (UAP) solution allow customers to properly address all six stages of the API lifecycle so that organizations can have a complete and continuous understanding of their API attack surface as the state of their APIs changes.
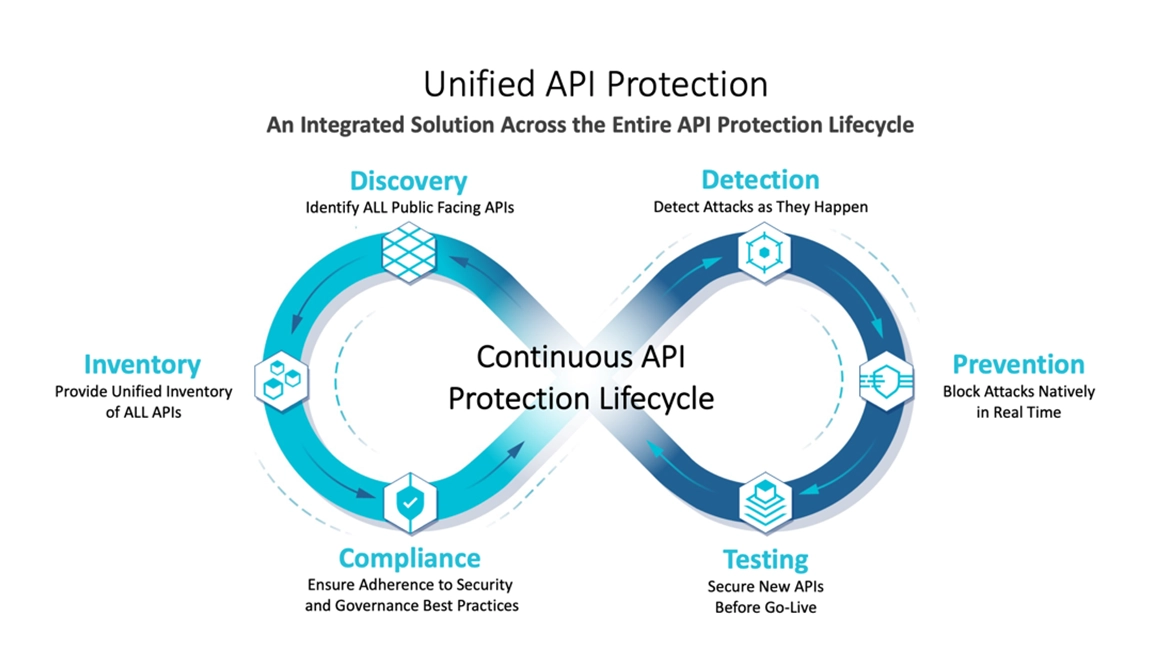
Figure: Unified API Protection
- Discovery: Enables the continuous discovery of an organization’s API attack surface. This is not limited to just APIs discovered through local traffic flows but discovering unknown shadow APIs that are implemented without any security oversight.
- Inventory: Allows for the inventory of both managed and unmanaged APIs, ensuring that security teams can manage their entire API inventory from a single location.
- Compliance: Ensures that your APIs are compliant with your organization’s security policy and industry best practices. Development teams are notified of non-compliant APIs and can prioritize critical security issues that require immediate remediation.
- Detection: Detects real-time API threats that target your application with extremely low false positive rates without the need for agents, mobile SDK, or instrumentation.
- Prevention: Provides real-time inline prevention of API cyber-attacks that target your mission-critical applications without the need to rely on 3rd party infrastructure to mitigate threats.
- Testing: Enables customers to test their APIs for conformance, risks, and sensitive data exposure before they are pushed into production.
Conclusion
CNAPP vendors serve a critical purpose in simplifying and managing critical cloud native security and cloud security posture issues that have been afflicting organizations for years. These vendors can help security and DevOps teams continuously monitor their cloud infrastructure ensuring that critical security issues are remedied before attackers exploit them. Cloud native security-focused vendors serve as a purposeful and complementary solution to API Protection solutions as CNAPPs do not fully extend up the stack to securing mission-critical API applications.
For API application protection, organizations also need to focus on implementing security solutions that understand how APIs are built, deployed, and exploited that unnecessarily expose their applications to cybercriminal activity. This often requires a separate and focused approach that understands the end-to-end API lifecycle and how to properly secure each stage, ensuring continuous API Protection for an organization’s mission-critical applications. A proper API protection solution can enable your organization to have an always-on approach that ensures that your mission-critical applications do not fall prey to a successful API attack.
Get a Free API Security Assessment of Your API Attack Surface
The post API Protection and Cloud-native Application Protection Platforms (CNAPP) appeared first on Cequence Security.
*** This is a Security Bloggers Network syndicated blog from Cequence Security authored by Muzaffer Pasha. Read the original post at: https://www.cequence.ai/blog/api-security/api-protection-and-cloud-native-application-protection-platforms-cnapp/




