SafeBreach Coverage for US-CERT Alert (AA22-264A) – HomeLand Justice Threat Group
On September 21, the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) issued a joint advisory highlighting the recent cyber operations against the Government of Albania by Iranian state threat actors identifying themselves as “HomeLand Justice”. According to the advisory, HomeLand Justice conducted these operations in July and September 2022 and used encryption and wiper attacks to render government websites and services unavailable. Additional details about these threat actors and their associated tactics, techniques, and procedures (TTPs) are available in US-CERT Alert (AA22-264A) Iranian State Actors Conduct Cyber Operations Against the Government of Albania
Attack Timeline
The advisory provides a good timeline of the threat actor activity. The investigation by FBI revealed that the Iranian threat actors gained initial access to the victim network approximately 14 months before launching the destructive cyber-attack that included a ransomware-style file encryptor and disk wiping malware.
- May–June 2022: The threat actors leveraged this period to move laterally and conduct reconnaissance activities within the Albanian government’s network with the objective of stealing credentials. The HomeLand Justice threat actors also created a website and multiple social media profiles posting anti-Mujahideen E-Khalq (MEK) messages.
- July 2022: The HomeLand Justice threat actors launched ransomware attacks on the Albanian government networks, leaving anti-MEK messages on desktops. When security teams tried to respond, the threat actors deployed a variation of the ZeroCleare destructive malware. Later in the month, they posted videos of the attack on their website, thereby claiming credit for the attack.
- Early August 2022: Social media accounts associated with HomeLand Justice continually posted polls asking their respondents to choose which stolen Albanian government information should they release. Based on the results of the poll, they would then release the stolen information either as a zip file or a video of the screen recording of the stolen documents.
- September 2022: The threat actors launched another wave of attacks against the Albanian government using TTPs similar to the July attacks. These retaliatory attacks were in response to the severed diplomatic relations between Albania and Iran.
Additional Technical Details
- Initial Access – According to the advisory, the threat actors gained initial access to the victim network approximately 14-months prior to the encryption and the wiper attacks. This access was gained by exploiting a Microsoft SharePoint vulnerability – CVE-2019-0604.
- Persistence and Lateral Movement – This phase of the attack started several days to two months after gaining initial access. Several [dot]aspx webshells were used to maintain persistence. The threat actors also used RDP, SMB, and FTP to move laterally within the victim network.
- Compromise of the Exchange server – The exchange server was compromised approximately 1-6 months after gaining initial access. This compromised exchange server was used to run several searches including, for administrator accounts. The compromised account was also used to create another exchange account and add it to the organization management workgroup.
- Likely Email Exfiltration – This data exfiltration happened approximately 8 months after initial access. The compromised servers were observed transferring between 3 to 20 GB of data.
- VPN Activity – nearly a year after initial access and approximately 60 days prior to launching the disruptive attack, attackers leveraged two compromised accounts and made several connection requests to the compromised organizational VPN.
- File Cryptor – To successfully encrypt the organizational data, the attackers logged into the organizational print server via remote desktop and kicked off a process (mellona.exe) which would propagate the GoXml.exe encryptor throughout the network to a list of internal machines along with a persistence script. GoXml.exe continued to encrypt files and folders in the network leaving behind a ransom note titled “how_to_unlock_myfiles.txt” in each of the encrypted folders.
- Wiper Attack – The final phase of the attack commenced 14 months after initial access was gained. This led to raw disk drives being wiped with the Disk Wiper tool (cl.exe)
It is important to note the coordinated and unique nature of this attack by nation-state threat actors. Microsoft security determined with high confidence that multiple threat actors were responsible for each of the distinct phases of the attack. Note – according to Microsoft the “DEV-####” designation is a temporary name given to an unknown, emerging, or a developing cluster of threat activity.
- DEV-0842 deployed the ransomware and wiper malware
- DEV-0861 gained initial access and exfiltrated data
- DEV-0166 exfiltrated data
- DEV-0133 probed victim infrastructure
Diplomatic Fallout
After the attack was discovered, the Albanian government asked the entire Iranian Embassy staff to leave the country within 24 hours. It led to the severance of diplomatic relations between Iran and Albania.
Important Note for SafeBreach Customers – Coverage for AA22-264A
As soon as details and IOCs for the ongoing exploitation of Vice Society were made available, corresponding new attacks were immediately added to the SafeBreach Hacker’s Playbook on September 22nd. It is important to note that some of the attack TTPs used by HomeLand Justice were already available in the SafeBreach playbook. SafeBreach customers already had an existing level of protection against these threat actors if their security controls were validated against these known TTPs.
on September 22nd. It is important to note that some of the attack TTPs used by HomeLand Justice were already available in the SafeBreach playbook. SafeBreach customers already had an existing level of protection against these threat actors if their security controls were validated against these known TTPs.
11 newly added playbook methods for US-CERT Alert AA22-264A:
- #7640 – Write GoXML malware to disk (Host-Level)
- #7641 – Transfer of GoXML malware over HTTP/S (Lateral Movement)
- #7642 – Transfer of GoXML malware over HTTP/S (Infiltration)
- #7643 – Email GoXML malware as a ZIP attachment (Lateral Movement)
- #7644 – Email GoXML malware as a ZIP attachment (Infiltration)
- #7645 – Pre-execution phase of raw disk wiper malware (Host-Level)
- #7646 – Write raw disk wiper malware to disk (Host-Level)
- #7647 – Transfer of raw disk wiper malware over HTTP/S (Lateral Movement)
- #7648 – Transfer of raw disk wiper malware over HTTP/S (Infiltration)
- #7649 – Email raw disk wiper malware as a ZIP attachment (Lateral Movement)
- #7650 – Email raw disk wiper malware as a ZIP attachment (Infiltration)
12 previously available playbook attacks for AA22-264A:
- #7000 – Change the desktop wallpaper (Windows)
- #214 – Scheduled task creation over SMB
- #240 – Upload File over SMB
- #6127 – Extract LSASS memory dump using PowerShell and Rundll32
- #6473 – Agentless lateral movement via RDP
- #6483 – Agentless lateral movement via SMB and RCE, using Token duplication
- #6513 – Agentless lateral movement via SMB and RCE, using Mimikatz
- #6550 – Agentless lateral movement via SMB and RCE, using Impersonated user
- #6909 – RDP Connection Between 2 Simulators
- #6910 – RDP Tunneling
- #7000 – Change the desktop wallpaper (Windows)
- #794 – Extract Login Information using Mimikatz
What You Should Do Now
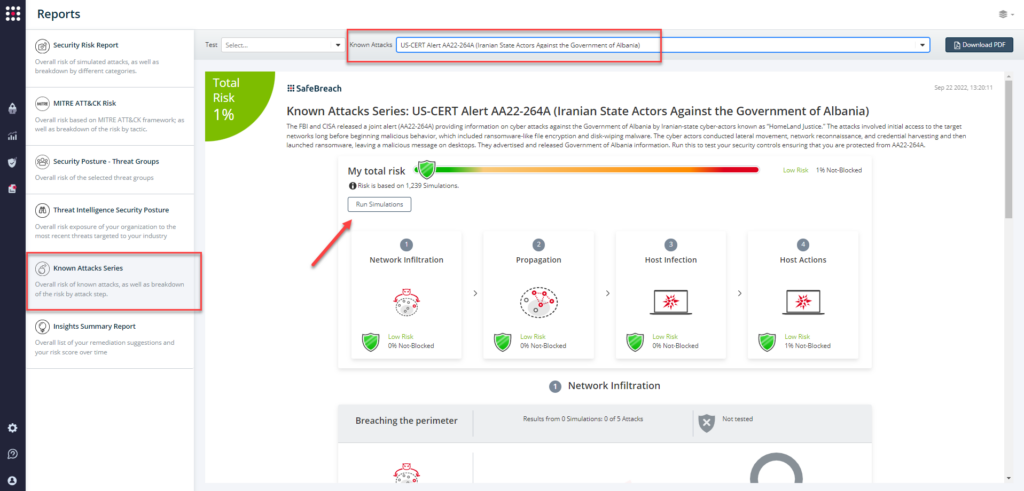
Attack methods related to US-CERT Alert AA22-264A are ready to run across your simulators. The Known Attack Series report has been updated so you can run the specific attacks from this US-CERT alert. From the Known Attack Series report, select the US-CERT Alert AA22-264A (Iranian State Actors Against the Government of Albania) report and select Run Simulations which will run all attack methods.
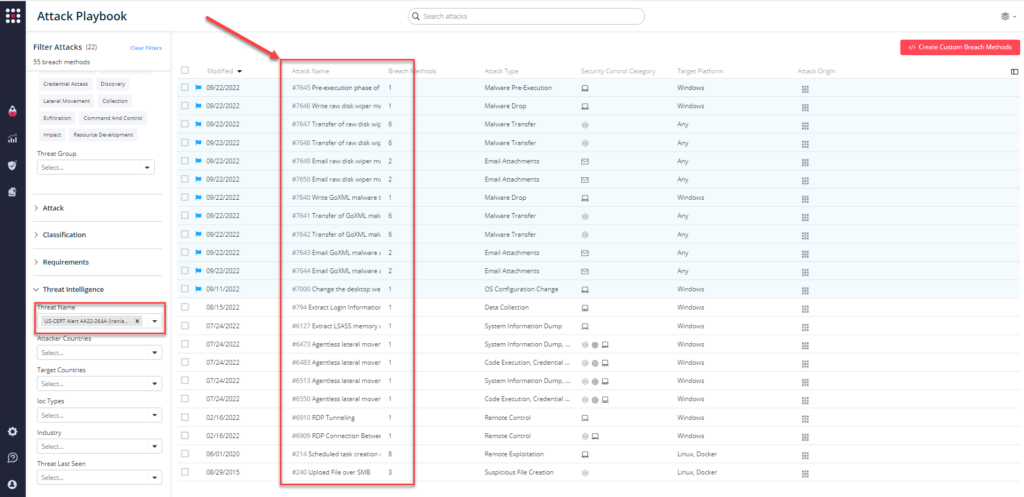
You can also select all the attacks related to US-CERT Alert AA22-264A by going to the SafeBreach Playbook and filtering by Threat Name – US-CERT Alert AA22-264A (Iranian State Actors Against the Government of Albania)
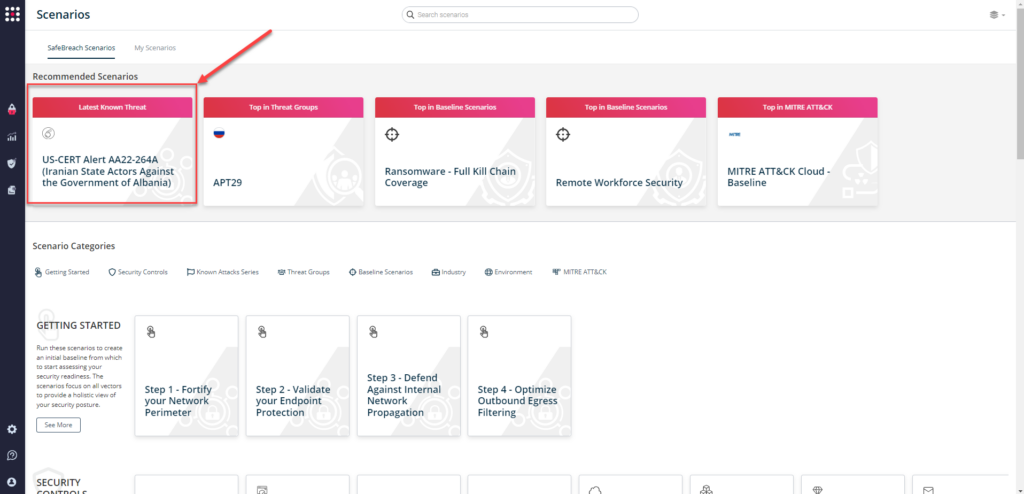
or you can go to “SafeBreach Scenarios” page and choose the US-CERT Alert AA22-264A (Iranian State Actors Against Government of Albania) scenario from the list of available scenarios.
NOTE: The following actions have been recommended by to mitigate any threat arising from threat actors targeting the Albanian Government:
- Ensure anti-virus and anti-malware software is enabled and signature definitions are updated regularly and in a timely manner.
- Adopt threat reputation services at the network device, operating system, application, and email service levels.
- If your organization is employing certain types of software and appliances vulnerable to known Common Vulnerabilities and Exposures (CVEs), ensure those vulnerabilities are patched. Prioritize patching known exploited vulnerabilities.
- Monitor for unusually large amounts of data (i.e. several GB) being transferred from a Microsoft Exchange server.
- Check the host-based indications, including web shells, for positive hits within your environment.
- Maintain and test an incident response plan.
- Properly configure and secure internet-facing network devices.
- Adopt zero-trust principles and architecture.
The post SafeBreach Coverage for US-CERT Alert (AA22-264A) – HomeLand Justice Threat Group appeared first on SafeBreach.
*** This is a Security Bloggers Network syndicated blog from SafeBreach authored by Kaustubh Jagtap. Read the original post at: https://www.safebreach.com/resources/blog/safebreach-coverage-for-us-cert-alert-aa22-264a-homeland-justice-threat-group/





