Home » Cybersecurity » Threats & Breaches » Vulnerabilities » Rule Over Your Dependencies and Scan at Your Own Open Source Risk
Rule Over Your Dependencies and Scan at Your Own Open Source Risk
High-impact vulnerabilities generate headlines you cannot ignore. But mere widespread awareness of cases such as Spring4Shell, Log4Shell, and Struts2 will not reduce your relative open source risk.
How do you direct your attention so your organization’s open source vulnerabilities don’t go unnoticed? A good first step: know and understand your dependencies by conducting regular scans of open source you use in your environments.
But what do differences in dependency scanning methodologies mean for your software supply chain?
Scrutinizing scanning
After developers downloaded more than 2.3 trillion open source packages from top ecosystems in 2021, recent efforts seek to help OSS maintainers better manage their projects. With so many open source components in every application, risks can come from anywhere in your codebase.
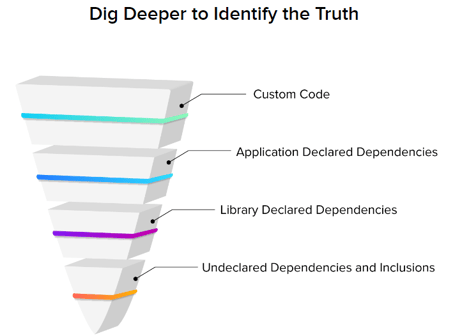
To manage that risk, you need to baseline your existing component usage. You can accomplish this in a linear sequence:
- Identify the components in your application.
- Identify the risk in your existing components.
- Decide if remediation is necessary.
Dependency scanning, as part of your software composition analysis (SCA) toolbox, covers the first two parts of this sequence. A scan captures the components you are using in a list, such as an SBOM, which you check against vulnerability databases to give you detailed information on the potential risks from your dependencies.
Let’s consider two dependency scanning methodologies:
- As-declared
- As-observed (a.k.a. as-deployed)
If you understand the differences between these scanning methodologies, you can take a more holistic approach to managing your open source risk. And if you account for direct versus transitive dependencies in your scanning, you can more proactively identify and, if necessary, remediate.
As-declared
An as-declared scan looks at what is declared in a package’s manifest file—for example, a package.json, setup.py, or even a simple (Read more...)
*** This is a Security Bloggers Network syndicated blog from Sonatype Blog authored by Aaron Linskens. Read the original post at: https://blog.sonatype.com/rule-over-your-dependencies-and-scan-at-your-own-open-source-risk





