Managing Security Alerts with an Incident Response Platform
The hard truth is that your organization will get breached. You need to have processes, procedures, and solutions in place to reduce the negative impacts.
In most organizations, security operations (SecOps) teams are overwhelmed with such alerts. In fact, the average organization receives more than 11,000 security alerts per day. Nearly half of security teams have seen a 3x increase in the past year alone – way more than any team can effectively manage. As a result, up to 70 percent of alerts are uninvestigated, but even a single ignored alert could lead to major consequences. This is where an incident response platform comes into play.
To protect your organization and prevent data breaches, you need to create an incident response plan and choose a way to triage alerts faster.
Incident response platforms exist to streamline alert triage and execute your IR plan. Having this type of solution allows your team to investigate every alert and ensure that you’re protected from the most advanced threats.
In this article, you’ll learn:
What is an Incident Response Platform?
An incident response platform is security software that automates and supports your incident response processes.
Automating your response to security threats enables your security operations team to triage alarms more effectively, respond to critical events faster, and seamlessly integrate your existing security solutions into a more efficient and comprehensive incident response program.
Key Features of an Incident Response Platform
There are 4 key duties of an incident response software:
-
Security Automation – Automates the manual, repetitive processes of incident response for faster response and resolution. This allows analysts to focus on more sophisticated threats, reduced time spent on false positives and improves response times.
-
Security Orchestration – Centralizes security operations data from multiple sources into a single interface to enable faster decision-making. Seamless integration and orchestration of your disparate security tools let SOC analysts gain visibility across the security ecosystem.
-
Case Management – collects real-time enriched data into a dashboard for easy alert management. This removes the need for analysts to dig for data, and improves processes to enforce standardization and compliance.
-
Reporting – Measuring performance across your tech stack is critical to improving incident response processes. Reporting capabilities give you an in-depth view of staff and tool efficiency, which helps establish ROI.
What is Security Orchestration, Automation and Response (SOAR)?
Security automation is the act of automating portions of your response plan to eliminate tedious and time-consuming manual tasks while allowing your SecOps team to focus on the alerts that really matter. Security orchestration is the coordination and integration of all of your existing security solutions and systems. An incident response platform that utilizes SOAR significantly improves incident response by:
-
Increasing efficiency
-
Gathering comprehensive data for improved threat intelligence
-
Centralizing security operations
-
Automating time-consuming tasks
-
Standardizing and scaling processes
-
Improving mean time to resolution (MTTR)
An incident response platform backed by security automation and SOAR technology can significantly improve alert management.
How to Create an Incident Response Plan
Now that you’ve identified how an incident response platform can help, it’s essential to have a thorough incident response plan in place. With an ever-increasing number of threats, it’s better to be safe than sorry when responding to cyberattacks.
Organizations need to establish an incident response plan and then utilize an incident response platform that can execute portions of the plan automatically to increase efficiency.
Essential Elements in an Incident Response Plan
The National Institute of Standards and Technology (NIST) provides a useful framework to help enterprises establish their own incident response plans.
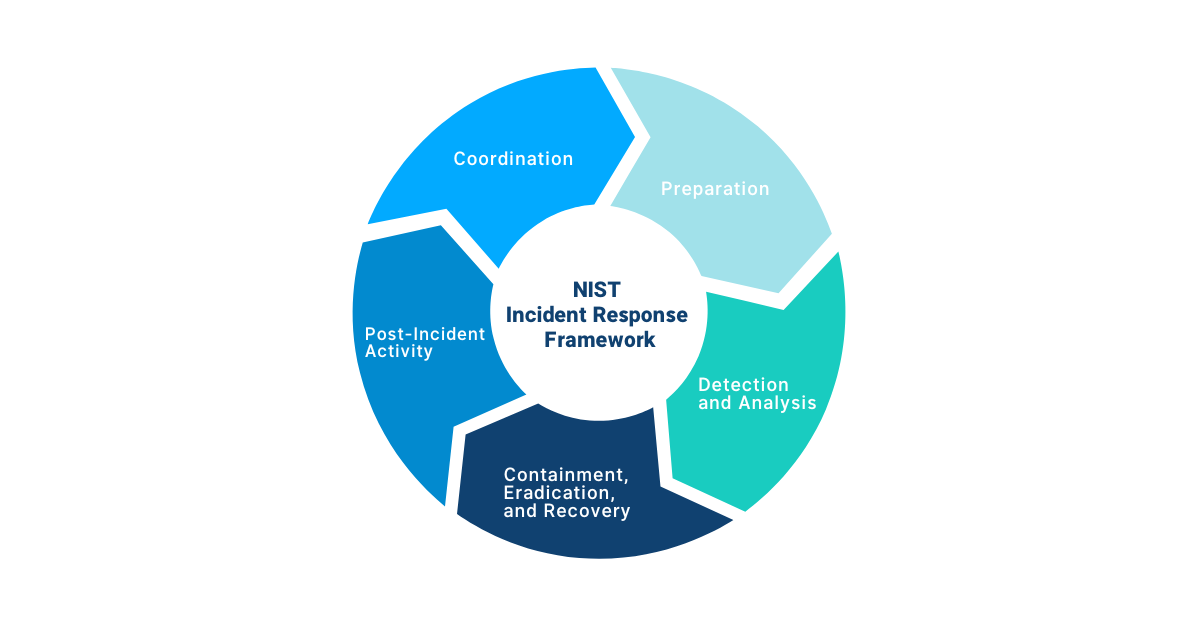
-
Coordination: Regardless of the size of an organization, a successful incident response plan requires the coordination of people, processes, and technology.
-
Preparation: Focus your plan on prevention tactics like anticipating threats and quickly mitigating them with effective countermeasures.
-
Detection and analysis: Unfortunately, in this complicated and evolving threat environment, breaches are pretty much guaranteed – no matter how prepared you are. You need technology in place to help you quickly detect incidents, evaluate the seriousness of them, begin incident documentation, and automatically notify the employees responsible for handling alerts.
-
Containment, eradication, and recovery: If you are impacted by a breach, you need to establish a protocol to contain the incident, remove it, recover impacted systems, and collect all relevant attack data.
-
Post-incident activity: Analyzing attack data can help organizations understand where their current security strategy is lacking and what they need to improve. Depending on the severity of the attack, post-incident activity may include cooperating with auditors, attorneys, security vendors, government officials, insurance agencies, and other stakeholders.
In addition, consider creating an incident response playbook to better define your plan. But now that you’ve established a solid incident response plan for your SOC, let’s dive into how to coordinate your incident response plan and platform.
Coordinating your Incident Response Plan and Platform
Low-code security automation platforms, like Swimlane Turbine, offer automated incident response capabilities that utilize SOAR to improve SecOps and better protect your organization. Considering the recommended NIST framework, Swimlane Turbine’s incident response platform can help by:
-
Coordinating people, processes, and technology: Low-code security automation allows you to integrate and orchestrate all the people and security tools you are using in your incident response processes.
-
Preventing incidents through adequate preparation: Security automation makes it easy to transfer all of your plans into actionable automated workflows. This streamlines alert investigation, requiring manual intervention when deemed necessary.
-
Streamlining detection and analysis: SOAR solutions quickly gather all contextual data from security platforms, analyze it, and generate a course of action. What’s more, they can automatically execute certain preventative actions to speed up analysis and mimic the practices of your security team.
-
Speeding up containment, eradication, and recovery: Speed and productivity are key when it comes to containing, eradicating, and recovering IT systems. SOAR helps increase efficiency by saving hours during incident response and threat detection by providing your SecOps team with all critical data in a centralized interface.
-
Supporting strategic post-incident discussions: If a breach has occurred within your organization, it is crucial that you discuss what security steps need to be taken to prevent a similar incident in the future. SOAR solutions gather all the contextual data and create automated cybersecurity incident reports.
Advanced Incident Response
Swimlane Turbine provides you with a robust incident response platform backed by low-code SOAR technology that is easy to use, manage, and scale. There is no need to replace the existing security solutions you have already invested in. Turbine’s API allows you to integrate solutions and leverage their capabilities. You never have to worry again that a missed alert will cause a breach within your organization. Instead, you can respond to every alert and ensure that your enterprise is protected from internal and external threats.
*** This is a Security Bloggers Network syndicated blog from Swimlane (en-US) authored by Kevin Broughton. Read the original post at: https://swimlane.com/blog/incident-response-platform/





