Framework Selection: How to Architect a Systematic Security Program – Part 1
A need for public trust in information systems has driven continuous technological advances and new regulatory requirements, which have in turn made the global cyber threat landscape more complex and connected (see figure 1). As Boards of Directors, regulators, and the public become more aware of this interplay, organizations will need to evolve to address more intricate threats in ways that maximize their security budgets while satisfying all stakeholders. This is where cybersecurity frameworks are most useful, because they help you understand how your organization’s current security state compares to a benchmark of success in a systematic way. You then can leverage that knowledge to form a strategy for growth. But where do organizations with no existing security program or an immature security program start?
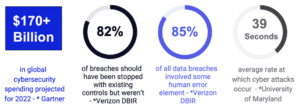
Figure 1: A set of statistics denoting the amount of money spent on cybersecurity in comparison to the frequency of technical error, human error, and rate of attacks.
Why Have Frameworks At All?
Every organization has a security program. Whether an organization aligns discrete resources (people, processes, and technology) to that program and how those resources are aligned determine whether the program is mature or not. So the million-dollar-question is: how do you know if you have the appropriate resources and if they are aligned correctly? A cyber security framework!
Many readers at this point will say to themselves, “We use a framework!” and will be thinking of ISO 27001, PCI, HiTRUST, SOC Type I/II, or any other number of compliance frameworks. While compliance frameworks do serve a purpose and do provide some level of security, contrary to some analysis, they only ensure certain boxes are checked. They do not provide a systematic approach to the development or improvement of a cybersecurity program. Add to this the pressure of deadlines, certifications, ROCs, and the potential monetary fallout of non-compliance and you have a recipe for organizations to achieve compliance in the quickest, most efficient way possible without much consideration for effectiveness.
While few organizations will avoid some level of regulatory- and compliance-driven security requirements, Praetorian recommends adopting the opposite mindset. We follow the axiom, “security should drive compliance not the other way around.” During the course of our advisory work with clients, Praetorian’s security engineers have observed the following three general areas in which organizations struggle when delving into cybersecurity frameworks from a security-driven mindset: framework selection, definition of a scoring rubric, and customization of the selected framework.
This article will focus on the first and most important item here: selecting an appropriate framework. This step is so crucial because it sets up the roadmap for potentially years of cybersecurity investments and will be the reason that the cybersecurity program ultimately succeeds for fails.
CIS Critical Security Controls: An option that matures with young programs
We consider the Center for Internet Security Critical Security Controls (CIS CSC) a great starting point for organizations who have no prior experience in cybersecurity programs or a fledgling program that is in need of maturation. This framework also is ideal for organizations who lack resources to implement a resource-intensive cybersecurity program, but who want to minimize their risk. The CIS CSC outlines 18 controls that an organization should have in place to protect against most internet threats. The CIS CSC defines each of their controls at three levels, called implementation groups (IG), which range from the minimum (IG1) to most robust (IG3) implementation.
The CIS CSC are broadly achievable early on in an organization’s lifecycle despite requiring specific implementations, which sets the framework apart from most other standards and frameworks. For example, the IG1 version of Control 3, Data Protection, only requires 6/14 Safeguards while IG3 requires all 14. Using these implementation groups, an organization can easily start work towards IG1 safeguards but also have a simple transition to the higher implementation groups without having to entirely change frameworks.
NIST Cybersecurity Framework: A holistic, organizational option for robust programs
For organizations that perhaps already have a robust security program but want to continue their maturation journey, the National Institute of Standards and Technology’s CyberSecurity Framework (NIST CSF) is a great option. Once your organization has implemented the 56 controls in CIS CSC IG1 (or up to IG3 if you’re ambitious!), it’s time to look to larger frameworks such as the NIST CSF. This also is true if you have an existing security program in place,
Developed in response to an Executive Order from President Obama in February of 2013, the NIST CSF has evolved as experts have researched what makes a cybersecurity program robust and successful. It is a great tool for measuring your existing cybersecurity program against risk and organizational aspects in addition to technical controls. The greatest benefit to the NIST CSF is that it allows organizations to customize how they satisfy the objectives, though recommended controls and implementations do exist for guidance.
The NIST CSF organizes cybersecurity into five different functions: Identify, Protect, Detect, Respond, and Recover. Each function breaks down into a set of objectives and sub-objectives. To see where your company’s cybersecurity program makes the mark or falls short, start by looking at the objectives under each function. For example, if you are not confident that you could detect a breach, then you should focus on the objectives and sub-objectives under the “Detect” function. Alternatively, if you look through the “Respond” function and can’t answer questions such as “who would be responsible for communicating an incident internally?,” consider taking a deeper dive on that function.
The Future And Beyond
After establishing a strong cybersecurity posture informed by the CSCs, the CSF, or another security maturity framework, the next step is to start layering with compliance and regulatory regimes that overlap it. This will ensure that your security-driven achievement of the controls in those frameworks has the added benefit of satisfying a compliance requirement.
In the next post in this series, we will dive deeply into how exactly an organization can measure themselves against a framework so that they can better understand their progress and target state.
The post Framework Selection: How to Architect a Systematic Security Program – Part 1 appeared first on Praetorian.
*** This is a Security Bloggers Network syndicated blog from Blog - Praetorian authored by emmaline. Read the original post at: https://www.praetorian.com/blog/how-to-architect-a-systematic-security-program/





