UnFAIR Cyber Risk Quantification: Balbix vs. FAIR
One thing evident from discussions at RSA and Black Hat 2022 is that cyber risk quantification (aka CRQ) is #trending. To understand why, consider this context: the chaos in cybersecurity continues with more breaches, eye-popping ransomware payouts, bigger fines, new regulation and increasing scrutiny of cybersecurity spending. As you can imagine, boards are frustrated and security teams are exhausted.
Enter CRQ.
CISOs want to use CRQ to prioritize risk issues. With CRQ, they also hope to better communicate cyber risk to business risk owners, c-level execs and the board, and to align cyber risk management with other risk practices.
The units of risk has to be money – that’s the only language that everyone understands. The theory is that with better prioritization, communication and alignment, organizations will be able to drive cyber risk reduction.
Some of you are likely flinching. Does implementing CRQ mean using FAIR?
What is FAIR?
Historically, risk quantification for cyber has been synonymous with FAIR which stands for Factor Analysis for Information Risk. Designed as a framework to understand, measure, and analyze cybersecurity risk, FAIR estimates the frequency and magnitude of loss events that result from different scenarios.
To implement a FAIR risk assessment, you enter data into a tool that guides you through the process of calculating your cyber risk. If you have never used a FAIR tool, this process is not very different from using one of those online tax calculators that tell you how much money you owe the tax man.
While FAIR is great in theory, implementing it has been a source of great frustration and disappointment for cybersecurity and risk practitioners. This is due to three reasons:
- FAIR relies on data that often does not exist. During assessments, this data is essentially made up by humans.
- FAIR is manual and hard for teams to do. It is impossible to continuously analyze risk with FAIR.
- FAIR is a black box with fuzzy outputs that are not actionable.
FAIR is not a practical approach to CRQ in 2022
A CRQ implementation is actionable only when your input data is objective, consistent and updated in real-time from the actual state of your enterprise’s software and systems. The input into CRQ should be comprehensive, covering your entire attack surface and reflecting the business context of each asset.
Instead of using data you already have, FAIR bases its risk assessment on manually sourced data which is inevitably influenced by opinion. As a result, FAIR tends to yield vague outputs leaving security practitioners questioning its accuracy. FAIR’s model is very rigid and practitioners struggle to incorporate information about specific threats and exploits, compensating controls or asset business value – things that they deal with every day.
The biggest drawback to FAIR is that — by itself — the model does not support automation, and therefore cannot provide real-time visibility of risk. With FAIR, calculating risk is a lengthy process that relies on manual input from risk assessors and consultants who render an analysis that quickly becomes obsolete. With the evolving threat landscape, risk scenarios need to be constantly re-analyzed to keep the FAIR model updated, which is practically impossible. If you use FAIR, your security practitioners, executives and board will almost always be making decisions based on obsolete data.
FAIR cannot be used to operationalize the rapid reduction of cyber risk
An effective CRQ solution produces output that decision-makers can use to operationalize rapid risk reduction. Without actionable insights, cyber risk quantification provides very little, if any, value to an organization.
FAIR’s over-reliance on probability estimation and qualitative inputs limits its usefulness for driving risk reduction. FAIR comes up with results that don’t provide traceability to your underlying security issues while also ignoring important business context. Furthermore, because FAIR analysis is limited to specific risk scenarios, security controls are narrowly targeted to mitigate these specific situations instead of reducing risk for real threats across the entire network.
Providing you with an UnFAIR advantage in cyber risk quantification (and reduction)
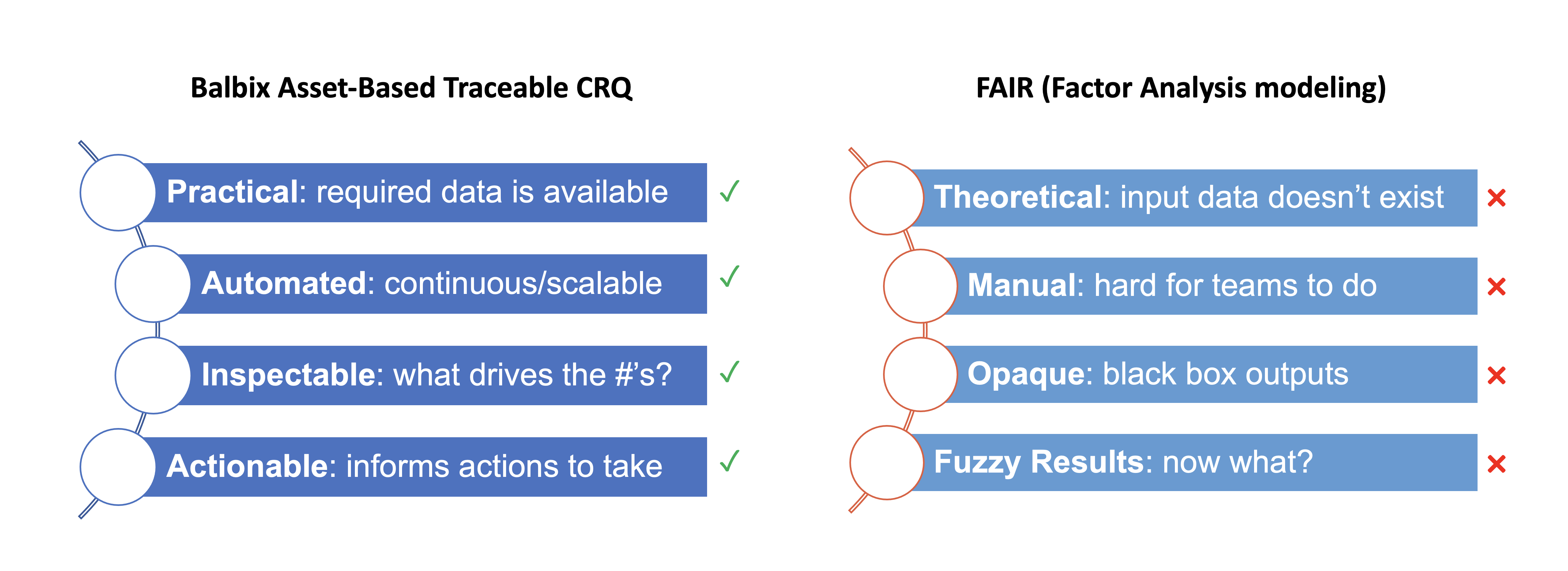
Unlike FAIR, Balbix was designed from the ground up as a practical and efficient risk quantification solution. When compared to FAIR, Balbix’s key differentiators are:
- Balbix utilizes data from your deployed cybersecurity, IT and business tools and real threat information. Nothing is made up.
- Balbix is maximally automated and continuously analyzes your attack surface to measure cyber risk.
- Balbix provides actionable steps to reduce cyber risk, prioritized by risk-reduction ROI
Utilizing actual enterprise asset-level and user-behavior data rather than scenario-based estimations, like the ones produced by FAIR, can lead to a more accurate interpretation of cyber risk.
Balbix automatically ingests machine-generated data from your environment across multiple IT, cybersecurity and business tools. This data is analyzed to produce a comprehensive view of cyber risk for each asset and for the entire enterprise. With this type of risk assessment, you can see how a particular threat is affecting your entire organization and utilize risk-management solutions to reduce cyber risk across the whole enterprise.

When we designed Balbix, we knew that automation would allow cyber risk quantification to happen faster, more effectively, and more accurately. Balbix’s automation capabilities allow for risk to be continuously calculated using real-time asset-level data, including vulnerabilities, threats, exposure, applicable security controls as well as business criticality.
Balbix is able to predict where and how breaches are most likely to happen by analyzing different attack scenarios. It then provides actionable prescriptions that your security team can use to improve cybersecurity posture, avoid breaches and improve cyber-resilience. You can analyze different remediation options and see the expected risk reduction outcomes.
Balbix also automates end-to-end processes for dispatching and mitigating risk issues. As remediation actions are taken, the risk calculations update the model immediately. All this is performed automatically and in near real-time without a need to manually reassess risk.
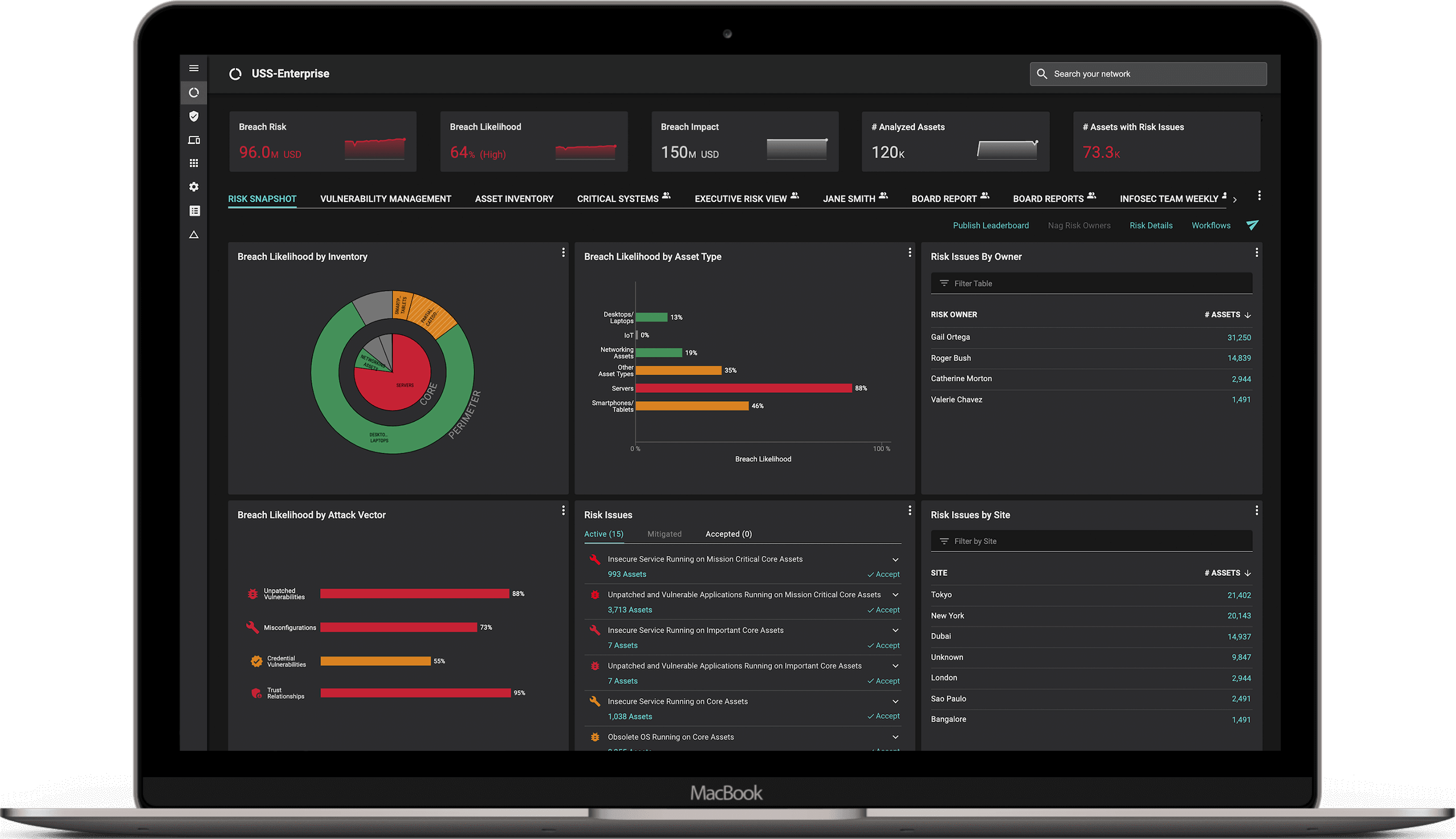
All this information, and more, can easily be reported to key stakeholders within your organization using business-aligned comprehensive dashboards. There is something magical about seeing the complexities of your cybersecurity posture being distilled into a single cyber risk value in Dollars (or Euros, Pounds, Rupees, Yen, etc.). It’s even more useful to be able to decompose these risk values into risk by type, risk by BU, risk by owner and drill down to the underlying security issues driving the risk. With Balbix you can do all of this.
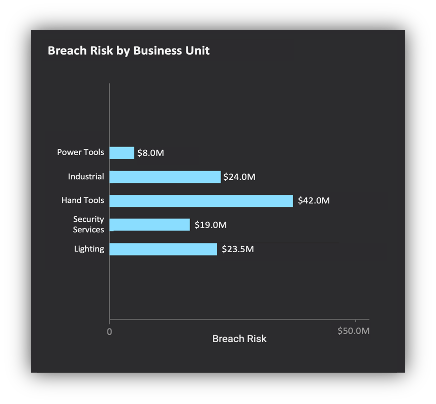
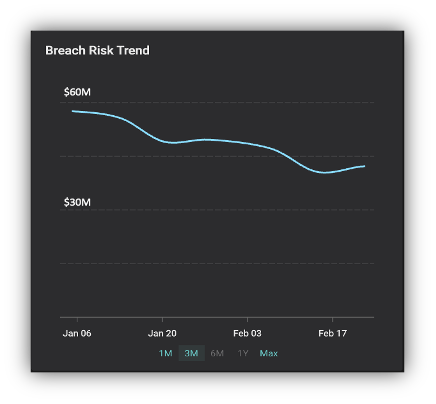
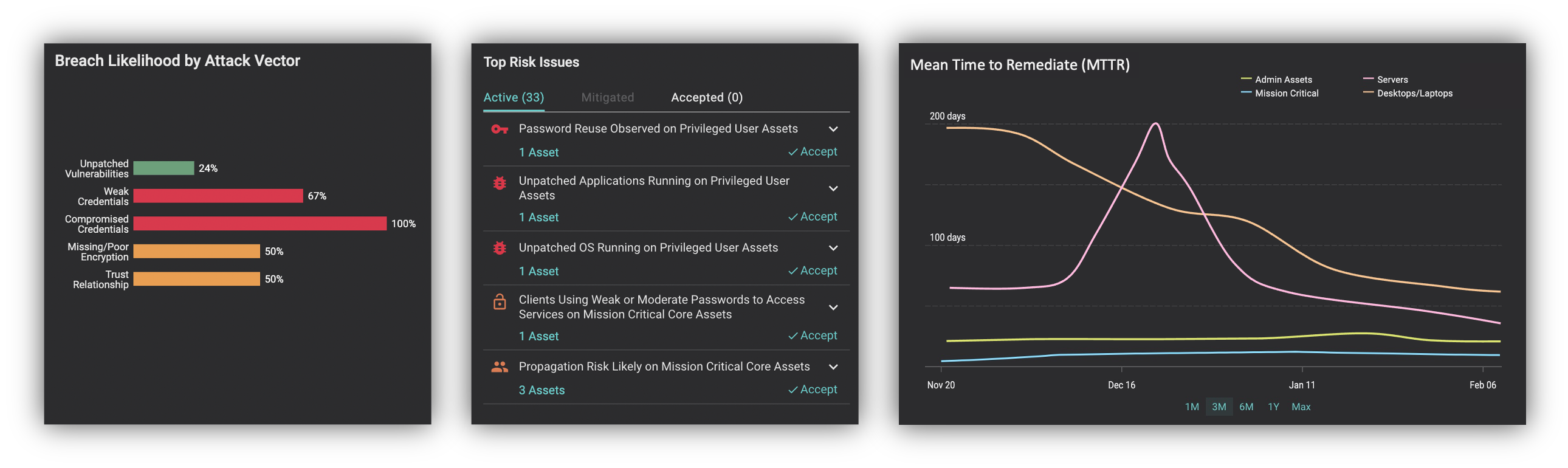
Perhaps most importantly, the Balbix approach lets your cybersecurity and risk management folks really understand all aspects of cyber risk. With Balbix, you can answer thousands of questions that come up as your security and risk management colleagues go about their daily work. Balbix’s search allows you to define a query using the vocabulary of cybersecurity, IT, business tags/names and cyber risk- think Google for cybersecurity! These queries define dynamic groups which can then be dashboarded, assigned to owners, used for reporting and triggering workflows. You can’t do any of this with FAIR.
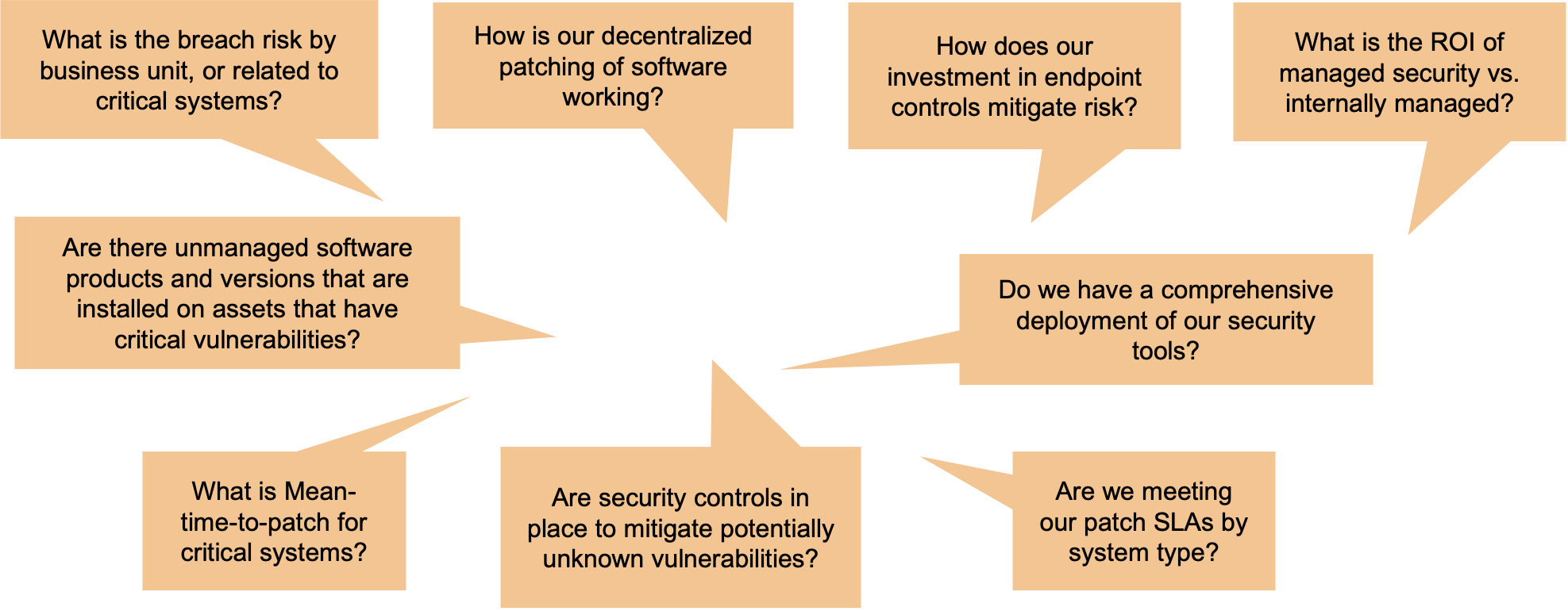
So, should you do FAIR, or would you like an UnFAIR advantage in cyber risk management? Please reach out and allow us to show you why 18 of the Fortune 100 and 100s of other organizations are rethinking how they do risk management with Balbix. You can ask for a demo here.
*** This is a Security Bloggers Network syndicated blog from Blog – Balbix authored by Gaurav Banga. Read the original post at: https://www.balbix.com/blog/unfair-cyber-risk-quantification-balbix-vs-fair/





