The Return of LOIC, HOIC, HULK, and Slowloris to the Threat Landscape
In June 2021, I wrote a blog questioning if decade-old denial-of-service tools were still relevant. At the time, I had concluded that while the tools were still relevant, they were not as popular or effective as they used to be due to the evolution of the threat landscape and the advancements in mitigation technology. I went on to say that Anonymous, the largest user group of those tools, was no longer the threat it used to be. Fast forward a year later, and not only have hacktivists returned to the threat landscape in a significant way, but they have also brought out the old playbook.
FIRE TEH LAZER!
In the decade’s first half, simple denial-of-service tools, such as HOIC, HULK, LOIC, and Slowloris, were the go-to choices for hackers and hacktivists worldwide. When leveraged by a group in a coordinated attack like an Anonymous operation, the threat actors could launch powerful distributed denial-of-services (DDoS) attacks, resulting in more successful campaigns. But after the publication of BASHLITE’s source code in 2015 and Mirai’s source code in 2016, threat actors abandoned these old tools. They began focusing on building their own IoT botnets capable of launching much more powerful DDoS attacks.
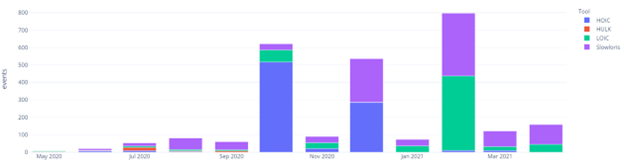
Data source: Radware Cloud Services
By the decade’s end, simple denial-of-service tools barely impacted the threat landscape, averaging less than a few hundred monthly events (see figure 1). This decline in use is primarily attributed to the collapse of Anonymous following the Trump/Clinton election battle in 2016 and hacktivists’ inability to grasp more advanced Tactics, Techniques, and Procedures (TTP) as the threat landscape evolved into a more organized and for-profit model.
CHARGING MY LASER! Again?
Since the first quarter of 2022, there has been a significant increase in hacktivism worldwide. This year we have already seen notable cyber conflicts arise in Eastern Europe due to Russia invading Ukraine and the Middle East due to the escalating tit-for-tat war. We are also now seeing an increase in activity in Asia related to geo-political escalations in Taiwan. Along with the renewed growth in hacktivism this year, we have also seen a tremendous spike in the use of decade-old denial-of-service tools in lockstep (see figure 2).
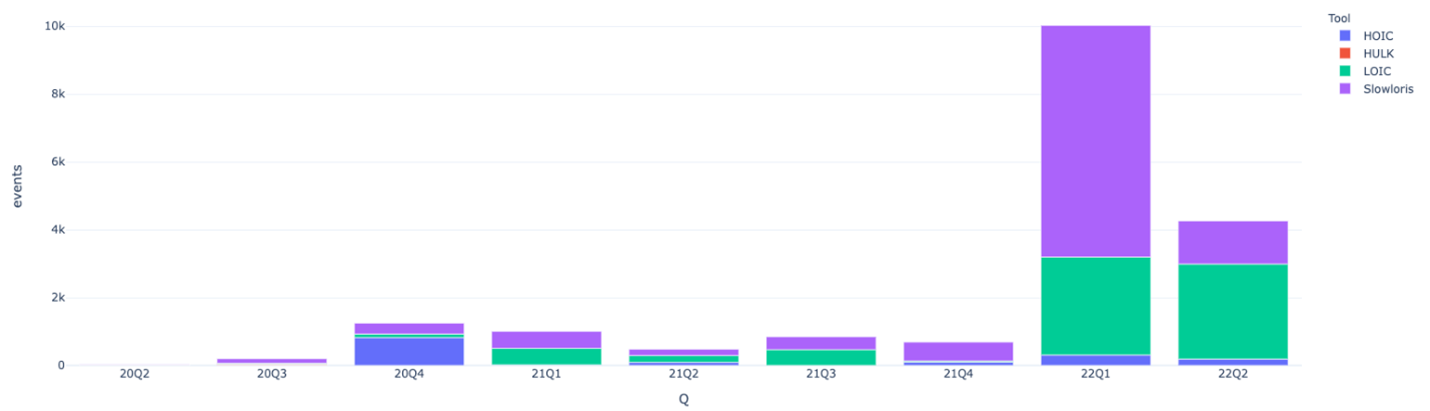
Data source: Radware Cloud Services
While these denial-of-service tools are trending down coming out of Q2 2022, the spike in Q1 is very noticeable. It’s greater than the last two years of HOIC, HULK, LOIC and Slowloris events combined. This growth is mainly attributed to the ongoing conflict in Eastern Europe, which has seen a large influx of hacktivism on both Russian and Ukrainian sides. This includes not only the return of Anonymous to the main stage with renewed operations under the battle tag, OpRussia, but also new hacktivist campaigns targeting Israel from threat group DragonForce Malaysia.
[You may also like: Q1 2022 DDoS and Application Attack Activity – An Overview]
Denial-of-Service: The People’s Digital Weapon of Choice
HOIC, HULK, LOIC, and Slowloris are all well documented, allowing anyone the ability to launch a denial-of-service attack without any prior knowledge or experience. And while these tools may not be relevant to the current threat landscape, one thing is clear about their return. They are the digital weapon of choice for people worldwide.
Most threat actors today who use these tools are not cyber experts or technically savvy people. They are people who have been driven to act and commit a crime due to a local or geo-political event, assuming their actions will be justified and result in their desired outcome. But what happens when that objective isn’t accomplished?
They crash from a dopamine high, reporting either they do not have the knowledge or the experience to counter mitigation by leveraging more advanced TTPs or that denial-of-service attacks on pharmacies and movie theaters will not win a kinetic war.
[You may also like: Is DDoS a Crime?]
Not only have we at Radware seen a noticeable dip in simple denial-of-service events in the second quarter of 2022, but Dyma Budorin, CEO of Hacken, has noticed a similar trend. In a recent article published by TheRecord, DDoS attacks surge in popularity in Ukraine — but are they more than a cheap thrill?, Budorin said that more than 100,000 people download his DDoS tool Liberator at the beginning of the Russian invasion, which has seen a peak of more than 6,000 consecutive users. Today, however, fewer than 3,000 people are currently using the tool.
Looking Forward: H2 Trends
As the Russian/Ukrainian conflict continues into the second half of the year, it is expected that the use of simple denial-of-service tools will continue to decline in the region as the local threat landscape evolves and escalates. Those unable to counter mitigation techniques or find unprotected websites will likely exit the conflict. At the same time, those who can advance will probably move away from the psychological highs of launching simple denial-of-service attacks and pursue more advanced tactics and techniques that will have a more significant impact on the current conflict.
It is also likely that low-level threat actors in the second half of 2022 will begin to shift their emotions and attention towards the growing conflict between China and Taiwan, running the same playbook seen in the Russian invasion of Ukraine during the first half of the year. In this case, we could expect another peak of activity from denial-of-service tools such as HOIC, HULK, LOIC, and Slowloris as unprotected assets are targeted in the region.
*** This is a Security Bloggers Network syndicated blog from Radware Blog authored by Daniel Smith. Read the original post at: https://blog.radware.com/security/2022/08/the-return-of-loic-hoic-hulk-and-slowloris/





