Home » Security Bloggers Network » Sifting Through Digital Exhaust
Sifting Through Digital Exhaust
Our Digital Exhaust & Identity
With all the data you have exposed on the Internet, I bet I know more about you than most of your close friends. Let me explain why.
For the greater part of the last two decades, to improve efficiency in business, government, commerce and socializing, nearly everything has moved online. So if I told you that today, you have a much larger digital presence than you did 10 years ago, you wouldn’t bat an eye—no surprise there. But compare your digital presence today against what it was just before the start of the COVID-19 pandemic, and you might be shocked to know your digital exhaust footprint has grown much more than in the 10 years prior.
Today, our digital identity is comprised of thousands, if not more, data points such as your:
- Personal details (name, date of birth, government ID numbers, etc)
- Contact information (email, telephone number, physical address, online handles, etc)
- Social media activity (posts, comments, likes, followers, etc)
- Hobbies and interests
- Work experience
- Skills and Languages
- Education/Degrees
- Relationships
- Achievements
But as we seek further efficiency afforded by technology––think connected “smart devices” like thermostats, refrigerators, light bulbs, a variety of other gadgets and appliances––our digital footprint is guaranteed to grow. It is projected that by the end of 2025, there will be more than 75 billion devices connected to the internet, which is nearly 10 devices for each living person on Earth. Some of those 10 devices you will use to intentionally expand your digital footprint (your phone, laptop, or tablet), while the remaining devices dirty your digital exhaust in ways you are unaware.
In three to five years, we’ll see a longer list of elements that comprise our digital identity, made possible by the telemetry sent by our connected smart devices. This data will amass in the digital ether and could come together to ascertain your:
- Dietary habits
- Home occupancy patterns
- Health metrics and medical conditions
- Safe driving habits (or lack thereof)
- Biometrics (voiceprint, fingerprint, faceprint)
How Does Digital Exhaust Occur?
We know our digital identity is made up of a large collection of data, but why is it on the internet in the first place? There are four main reasons.
1. Human Nature. As human beings, we like to share everything we do on the Internet.
2. Data Leakages. Accidental publications of your data, due to misconfigurations and errors, by companies you have or currently engage with
3. Data Brokers. Their main business is to sell your data on the Internet, and most of them operate fully within the law!
4. Data Breaches. Although the companies you engage with make a concerted effort to safeguard your data, this information is valuable to hackers, and so data breaches happen frequently, exposing your personal information on the Dark Web.
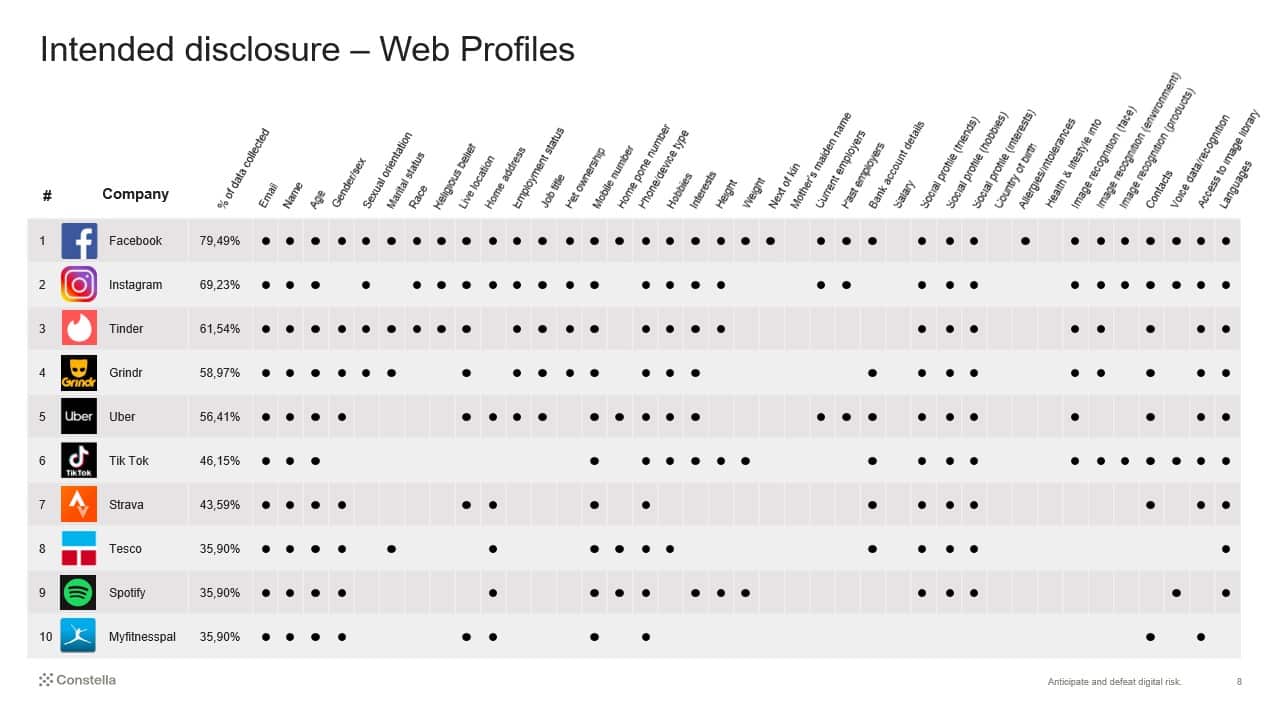
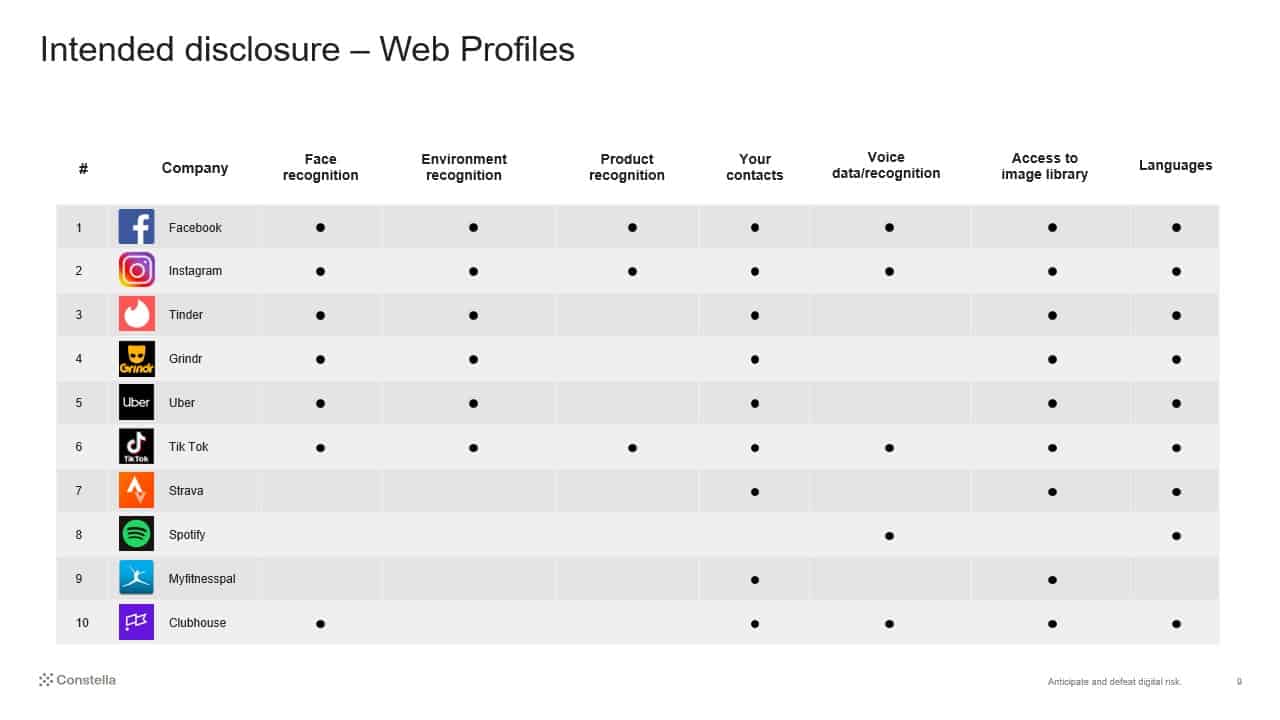
Intended Disclosure – Web Profiles
Those of you who are active Internet users, particularly social media, recognize that many sites you visit ask for information about you, and you volunteer it. This makes sense, as an online dating profile won’t get you any dates if it contains nothing about you, for example. Intended disclosure of your personal data online is more than just being cautious about what you post on social media, it extends out to information you provide on your various profiles. Take a look at the graphics below.
As if your social profile data did not reveal enough about you, many of these companies implement face and voice recognition software that can find photos and videos of you that you’re not tagged in.
Third Party Disclosure – Misconfigurations
IT expertise is a coveted skill, and not every IT practitioner even knows about— secure configuration & maintenance of IT systems. Perhaps a company’s systems were set up by the vendor but haven’t been maintained or tested for security in years. Or a small company can’t afford enterprise tools and has to rely on free consumer tools (that typically aren’t optimized for business use). These are realities that small companies face, and many don’t identify the need to upgrade as the business grows. While these companies don’t have any malicious intent, an innocent lack of knowledge or IT skills can lead to the inadvertent disclosure of your personal information.
Sometimes, sensitive documents are unintentionally published on the internet via:
- Open Devices (i.e. no security by default) like FTP servers, Buckets, Databases
- File-sharing websites like Scribd, Google Docs/Slides/Sheets, 4Shared, etc.
- Websites indexing content unintentionally
Because these documents are out in the wild with no security layer hiding their contents, these sites, despite receiving little traffic, are indexed by search engines, and a simple Google Search may turn up with your private data.
Third Party Disclosure – Companies’ Bad Practices
“When you sign up for a newsletter, make a hotel reservation, or check out online, you probably take for granted that if you mistype your email address three times or change your mind and X out of the page, it doesn’t matter. Nothing actually happens until you hit the Submit button, right? Well, maybe not. As with so many assumptions about the web, this isn’t always the case, according to new research: A surprising number of websites are collecting some or all of your data as you type it into a digital form.” –Wired Magazine.
Have you ever started shopping with an online merchant you hadn’t used before, and after adding a few items to your cart decided to hold off on making the purchase and left the page—but moments later you receive an email reminding you there are “items waiting for you” in your shopping cart? As competition grows, websites are implementing very clever techniques to maintain their edge, like reminding you of your “abandoned” shopping cart. Experts have found that many sites capture everything you type on their site, in real-time, regardless of you pressing “submit” on the form.
Data Brokers
A growing problem in the data trade is Data Brokers. These companies harvest your exposed data and enrich it with other information available about you (sometimes buying this data from other organizations) to create a comprehensive profile on you and your family; also linking your professional information with your personal information. Once packaged, these enriched data sets with your contact information (and many others like you) are made available for sale to buyers seeing contact lists for marketing purposes, or to head-hunters seeking certain professionals.
A large database containing contact information for Executives and VIPs can be purchased for as little as $79. Some data brokers even charge you a few cents per query, where you can find the personal and professional email addresses and phone numbers of person you’re attempting to make contact with.
Data Breaches – The Unpredictable Problem
Finally, let’s close this chapter with what I call “the unpredictable problem”, the Data breaches. As you know, this is a problem that is growing out of control. At Constella, we have detected a total of 66 billion breached identity records.
It’s easy to dismiss the impact a data breach can have on you, but it is very important not to ignore this reality. Like the typical internet user, you likely have accounts on some very well-known web services such as Facebook, LinkedIn, MyFitnessPal, and Adobe. All of these companies have suffered a data breach in the recent past, and parts of their databases have been compromised. For example, a breach of LinkedIn exposed 164 million individuals’ records onto the dark web.
Do you know how many breaches you appear in?
If you look at the culmination of your data exposures, you may be surprised to find out that your location was exposed 3 times, your email 9 times, your credit card twice, and 6 of your passwords exposed.
So, What Now?
Very likely, quite a bit of your personal information is available on the internet and more of your data will continue to seep out into the public sphere. If this comes as a shock to you, you very likely need to take a step back, evaluate your level of exposure and come up with a game plan. Rest assured, you’re not alone, and there is a lot you can do to protect yourself. But the process starts with learning what’s out there.
In a future installment of “Sifting Through Digital Exhaust”, we’ll discuss how to remove much of your exposed data from the internet, opt-out of being tracked, and keep tabs on what information about you is out there. Furthermore, we’ll discuss in greater depth how this data can be used against you.
In the meantime, protect yourself and your business by enrolling in identity and credit monitoring, and remain mindful that as you drive the roads of the digital world, your exhaust leaves a trail of breadcrumbs that can come back to haunt you.
Learn about Constella’s Dome Digital Risk Protection Platform
What type of threats are you or your organization facing? Check your exposure risk and see if you or your employees credentials have already been exposed in a data breach. Safeguarding your employees and organization begins here.
Deliver new monitoring services to your customers using the Constella Intelligence API.
The post Sifting Through Digital Exhaust appeared first on Constella Intelligence.
*** This is a Security Bloggers Network syndicated blog from Constella Intelligence authored by The Constella Team. Read the original post at: https://constellaintelligence.com/digital-exhaust-cyber-physical-threats/