Fundamental Security Concepts and Best Practices Every Game Developer Should Know
Gaming is now the world’s favorite form of entertainment, with Newzoo reporting that by 2023 there will be more than three billion gamers across the planet. With the growth of multiplayer games, however, the number of cheaters has also increased.
A study by The New York Times found that almost 50% of computer gamers admit to using game cheats at least once in their life. Such a high volume of cheating significantly impairs the gaming experience and as a result the revenues of the entire industry, which is estimated at more than $300 billion.
If gaming is not your thing, just imagine if, during every competitive event that you watched, there was a high probability that one (or more) of the players was cheating. Would you still enjoy it as much?
Is there a difference between the types of cheats concerning prevention?
There is a considerable variety of cheat types, from simple leveling bots that help the player perform exhausting actions over time to advanced item duplications and infinite ammunition.
Client-based cheats like “aimbot,” which allows the player to automatically aim in shooting games, and macros that perform a pre-recorded set of actions are impossible to prevent entirely since they are not dependent on the game implementation and run solely on the player’s local computer (client). This is why it is still seen even in the most popular AAA games, which may have almost endless security budgets.
As such, while this is far from a straightforward process, what types of cheats can be prevented by writing secure code and through better design?
Three real cases of cheating in multiplayer gaming
In Defcon 2019, a player named Manfred showed how easy it was to cheat the most popular multiplayer games. To bypass any encryption and obfuscation methods, he used code injection into different layers that allowed him to read and write code to the games’ client.
- In the popular game Ultima Online, every player can delete their own house, but apparently, the house ID was being sent in the request packet and there was no server validation that the house ID was owned by the requester player. All bad actors had to do was to change the house ID before it was sent to the server and you could now delete other players’ houses.
- In another demonstration Manfred showed how he exploited the massive multiplayer game, Rift. Through using integer overflow, he withdrew -1 coins from the bank and received the max amount instead.
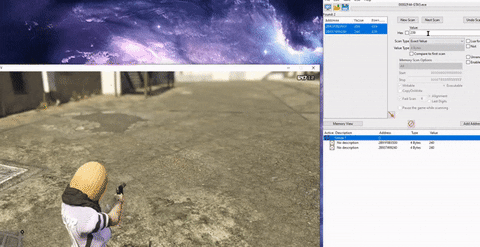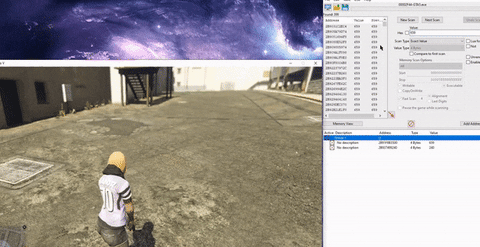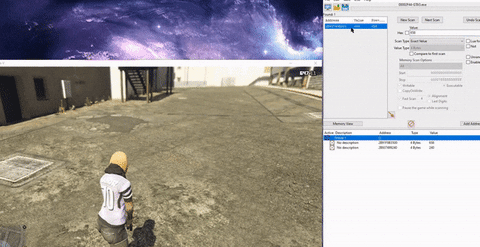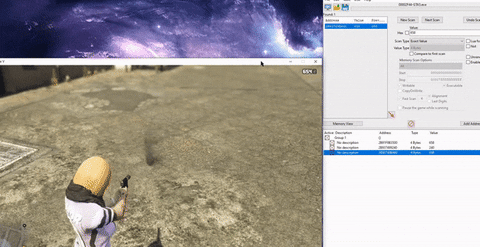
- Even simpler, and not requiring any code manipulation, in GTA 5 Online a player could have an infinite amount of ammunition by modifying the client memory. Simply locate the memory address that keeps the ammunition value, which could be done easily with software like “Cheat Engine”, then search for your current ammunition value (240 for example) and shoot a single bullet. Then search within the found addresses for the new value (239). The addresses left are those that hold the ammunition value, so now all cheaters had to do is keep editing these address values.
How to prevent cheating in online gaming
There are two fundamental concepts that can help you achieve a more secure game:
- Treat the code as open-source.
While encryption, obfuscation, third-party applications, and other techniques designed to make it more difficult to tamper with the client code are good security practices, they cannot be relied upon as they can be easily bypassed. - Never trust the client and anything that comes from it.
As we saw in the examples above, cheaters can modify client memory, disk, network traffic, runtime code, and everything else on the client end.
Seven best practices to prevent cheating in online games
Keeping these two concepts in mind, there is no point in establishing a prevention strategy on the client’s end. We will focus only on the server-side. Below are the best practices to prevent cheating in any multiplayer game.
- Use dedicated servers as the only valid authority. Other multiplayer architectures, like listen servers or P2P, may be good enough for development but not for production. Game decisions should only be made on trusted and protected servers.
- When writing network-related code, it’s important to separate client and server logic. Labeling server functions that are designed to be called from the client is the very first step in cheat prevention, as these will be the functions you need to address.
- Never update the server with the result, but with the actions that led to it, even if it means redundant processing. For example, instead of updating the server that the player has acquired X items, update exactly what the player has done. This will let the server make the necessary checks and draw the required conclusions.
- Avoid sending parameters from the client to the server, again, even at the cost of further processing. Instead of updating the server that the player shot a bullet of type X, let the server re-extract the weapon type.
- Validate anything that comes from the client, and ignore any checks performed on the client-side. Before shooting a bullet – does the player hold a ranged weapon? Does he have bullets in the magazine? Is he even alive? Is the received parameters valid and in the expected value range? Don’t skip even the trivial checks!
- Enforce a minimum delay between client-server calls, to prevent a server function from being called at a smaller interval than it should. This will, for example, prevent a cheater from emptying his entire magazine at a very high speed (rapid fire modifications).
- Environmental checks – some validations will not be as easy to perform. If the player tries to interact with an object in the world, for example, you can check the distance from the player to the object, but what if the object is blocked and the player can’t actually interact with it? These types of checks can be done using engine environment queries (e.g., line traces, collision checks) and in some cases, may affect the server load.
Summary
Unlike other fields, in multiplayer games the communication with the server is immense. Every single action must be synchronized and validated within the server, making it very easy to lose track.
All a cheater needs is one missing validation. That’s why it’s critical to have this mindset from the very beginning of a game’s development, always thinking of cheating possibilities and how they can be prevented.
As mentioned, not all cheats can be prevented by better code implementation and design. The most common type is gaming bots, software applications that run on the player end and give them a significant advantage.
In a related post, my colleague Oren writes about the evolution of bad bots and why they are so difficult to detect.
The post Fundamental Security Concepts and Best Practices Every Game Developer Should Know appeared first on Blog.
*** This is a Security Bloggers Network syndicated blog from Blog authored by Tal Shabi. Read the original post at: https://www.imperva.com/blog/fundamental-security-concepts-and-best-practices-every-game-developer-should-know/