9 Cybersecurity Challenges Companies Must Tackle Now

Last year, cybercrimes were fueled by the COVID19 pandemic after the sudden shift to work from home and hybrid working culture. As more workers started working from home and preferred to work remotely, businesses became more vulnerable to ransomware attacks. In the coming years we can expect more of the same and much more devastating cyberattacks to keep an eye on.
Most of these attacks are intended toward the most crucial asset of businesses: data. The new wave of cyberthreats made it mandatory for organizations to set up an effective cybersecurity strategy to survive and thrive in this vulnerable environment.
This blog post will discuss the top cybersecurity challenges companies will face now and in the future.
The New Challenges of Cybersecurity
The most impactful and modern cybersecurity challenges expected to face by companies include:
- Security of remote work and hybrid workforces
- An increase in supply chain attacks
- Firmware attack weaponization
- Ransomware attacks evolution
- Risks associated with 5G
- Attack on a nation-state
- Deep Fake Technology
- Issues of Staffing
- Attacks on APIs
1. Security of remote work and hybrid workforces

The risk involved in remote work (Image source – Keap)
Amid the COVID19 pandemic, almost all industries and businesses have adopted a new work culture that is remote or hybrid work. This need has become a new norm even after most countries’ lockdown restrictions have been lifted. The network protection in organizations that served as the borderline defense against cyberthreats is not possible in this new work model. Employees working from home connect with open Wi-Fi networks with their PCs or laptops under unsupervised conditions.
Remote working is not going anywhere anytime soon, and in recent times, companies have taken significant steps to curb emerging cyber threats. But securing remote and hybrid working conditions will remain a primary pain point for the cybersecurity domain. Between January and April 2020, cloud-based attacks increased by 630%.
2. An increase in supply chain attacks

Image Source: Helpnet Security
Supply chain attacks are cyberattacks that target an organization by compromising its suppliers or other third-party vendors. These attacks can be challenging to detect and can significantly impact an organization, as they can give attackers a way to gain access to sensitive data or systems.
Supply chain attacks are skyrocketing at a rapid pace. A recent survey indicates that around 80% of organizations have experienced a cyberattack due to hidden vulnerabilities and loopholes in their supply chain.
The 2020 SolarWinds event, which Microsoft president Brad Smith described as the “biggest and most sophisticated attack ever,” was one of the most catastrophic examples of a supply chain attack.
Cyberattacks impact the targeted businesses and produce significant collateral damage that impacts partner organizations, vendors, customers, employees, and other critical stakeholders linked with the supply chain. This growing trend is expected to accelerate with more supply chain breaches and malware intrusions in the ongoing year.
3. Firmware attack weaponization
Firmware attacks are a type of cyberattack that targets a device’s firmware. Firmware is the software stored in a device’s read-only memory (ROM). Firmware attacks can allow attackers to gain control of a device or its data and can be challenging to detect and defend against.
Firmware attacks can target any device that uses firmware, including computers, routers, and IoT devices. One example of a firmware attack is known as “badUSB.” This attack reprograms the controller chip in a USB device to turn it into a “keyboard.” This allows the attacker to send keystrokes to the victim’s computer, which can be used to install malware or give the attacker remote control of the computer.
According to Microsoft’s recent “Security Signals” research, which polled 1,000 security and threat protection decision-makers at business companies, 83 percent have been struck by a firmware attack in the previous two years.
Sadly, most organizations often undermine Firmware security. The industries that face most of these attacks must start adopting an effective hardware-based malware protection strategy.
4. Ransomware attacks evolution

Image Source: Kaspersky
Cyber-attacks are on the rise, and it seems like no one can escape. In 2021 we saw massive growth in ransomware against individuals and organizations. However, this trend did not die down because, by 2022, another wave had come crashing down, bringing more pain than ever before!
Hackers threaten to publish the victim’s private data or block access to the valuable data or files unless a ransom demand is met. According to data, around 1 billion USD were paid as ransomware payments in the US during the first quarter of 2021 alone, and this figure is expected to grow further.
JBS, the world’s largest beef supplier, paid cybercrime outfit REvil a $11 million ransom in May 2021 after an attack shut down operations in the United States and Australia.
JBS claimed that while most of its systems could be restored without assistance, the payment was made to ensure that the stolen data would not be exposed.
As ransomware attacks are on the rise and businesses and individuals are at risk, we must assess our cyber security personally. A guide to cyber security can help employers educate their employees about ongoing risks. Similarly, it can help individuals understand how they can stay protected while browsing the internet.
5. Risks associated with 5G
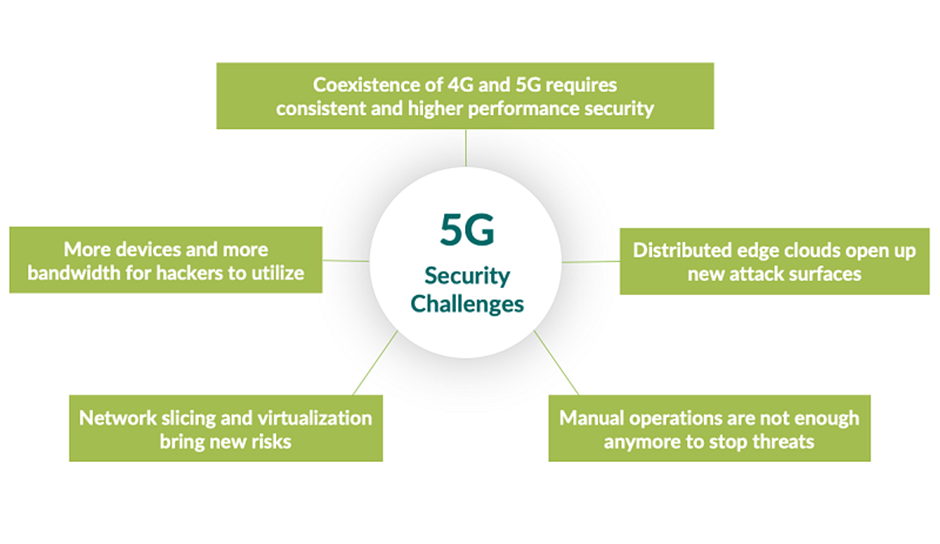
Image Source: Juniper
More companies worldwide are looking to adopt 5G technology to boost their IT capabilities and join the race of digital transformation. But it comes amid some new challenges in terms of cybersecurity. As 5G will rapidly increase the usage of the IoTs, cyberattackers can leverage the vulnerabilities of connected devices and use these devices to intrude the network. Therefore, organizations must curb all the risks linked with the latest 5G technology or face devastating outcomes.
Vodafone Portugal has revealed that it was the victim of a cyber-attack that impacted 4G and 5G networks.
According to the firm, the network outage occurred on February 7, 2022, due to a hostile cyber-attack intended to create harm and disruption. The incident affected data networks, the 4G/5G network, fixed voice, television, SMS, and voice/digital answering services.
6. Attack on a nation-state
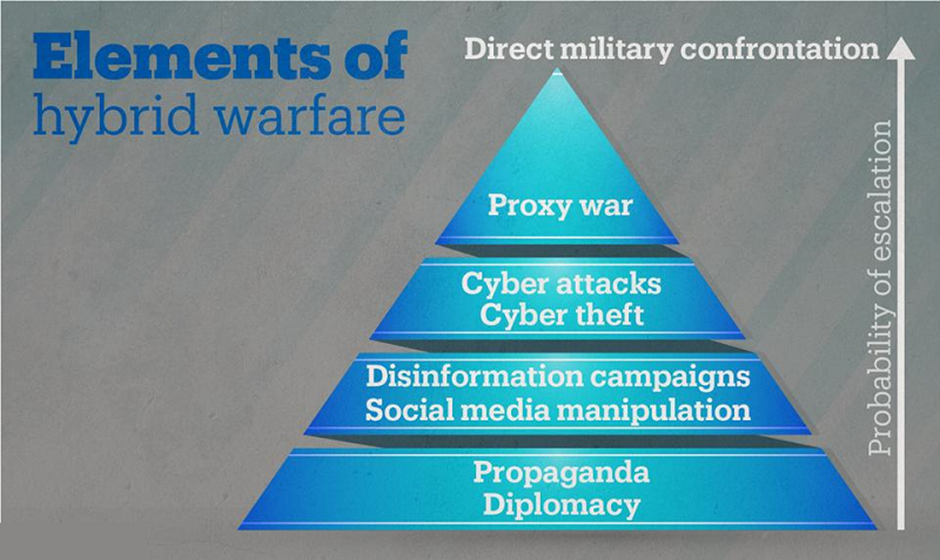
Image Source: TRT World
Modern warfare is all about cyberattacks. Consider an example of the Russia-Ukraine conflict. According to the intelligence data, Russia deployed 8 to 9 different viruses to attack the computing systems of its adversary. United States, UK, and European Union claimed that Russia had targeted satellite communications used by the Ukrainian Army. This hybrid warfare has made it mandatory for the countries and their militaries to set up an effective cybersecurity system to curb the impact of any unfortunate event.
7. Deep Fake Technology

Image Source: Social Media Safety
Deepfake technology is a rapidly evolving AI-based method for creating realistic fake videos. Deepfakes can be used to create realistic fake news stories or to generate “false flag” events that could damage an individual or group’s reputation. Deepfakes are also a potential tool for cybercriminals, who could use them to create phishing attacks or to spread malware.
The first reported Deepfake attack was discovered by insurance company Euler Hermes in March 2019. (which covered the cost of the incident). The con began when the CEO of a British energy company received a call from his employer, the head of the firm’s German parent company—or instead, the CEO mistook for his boss.
According to Euler Hermes, the CEO heard his boss’s voice with the precise tone, inflection, and minor German accent asking him to transfer $243,000 to a Hungarian supplier’s account.
8. Issues of staffing

Source: Help Net Security
Growing cyber threats need to be handled with modern strategies and well-trained cybersecurity staff. The companies are facing issues finding the right skillset and equipped individuals to secure their network infrastructures.
One of the reasons many cybersecurity professionals have battled is the global pandemic’s abrupt surge in remote working.
According to a study that polled over 500 cybersecurity experts, 57% said a shortage of cybersecurity skills impacted the company they work for, with just over 10% saying it has had a significant impact.
People and training are critical as technology evolves quickly, and the methods cybercriminals use to break into networks also evolve. So, it’s critical for businesses to invest in hiring the right people and training them to stay on top of the latest threats and deal with new technology.
9. Attacks on APIs

Image Source: Data Center Knowledge
API security has also become a growing concern for all industries. The most severe and devastating API attacks include API injection attacks targeted toward an application based on awfully developed code. In API injection attacks, hackers inject malicious code into software and gain control of an application. Another attack linked with APIs is Distributed Denial of Services Attack (DDoS), in which multiple computer systems swamp the bandwidth of the web application.
Peloton, a fitness startup, recently announced that customer account data had been exposed on the internet due to a flawed API that allowed unauthenticated calls. Even if users set their account profiles to private, anyone could view their data on Peloton’s servers.
Protecting from evolving threats in 2022
To refrain from facing the aforementioned cybersecurity threats, you need to:
- Keep your cybersecurity systems updated with all the necessary SOPs active
- Use modern and security-rich network infrastructures by trusted manufacturers
- Make sure your IT team is leveraging the latest threat intelligence methodologies to monitor malicious activities
- You must onboard the right talent and cybersecurity tools to address the evolving cybersecurity threats
- Outsource an experienced cybersecurity firm to deal with cyber threats effectively
Conclusion
A new wave of cybersecurity threats cast a substantial financial and reputational impact on your business if you undermine the need for an effective cybersecurity system and strategy.
Therefore, evaluate your network infrastructure, prepare your in-house team, or outsource an experienced cybersecurity service to address this decade’s most devastating cyber threats.
*** This is a Security Bloggers Network syndicated blog from Blog Feed authored by Blog Feed. Read the original post at: https://www.globalsign.com/en/blog/cybersecurity-challenges-companies-must-tackle-now






