State of API Security Activity
A recap of API threat statistics and unique threat patterns observed by the Cequence CQ Prime Threat Research Team.

Summary of Key Findings
- Unusual uptick in traffic from China spiking at a 200% increase
- User-experience business logic was abused to commit fraudulent purchases on stolen cards
- Pop in traffic from a holding company for scraping and hosting services
API Security Trends Observed
Between late February and early April 2022, the Cequence API Security Platform mitigated 108 million ATO attempts, using behavioral fingerprints and blocking millions of malicious IP addresses and organizations. During that same timeframe, the Cequence CQ Prime Threat Research Team observed an unusual uptick in traffic from China across the board, bucking the common bot tactic of blending in with normal traffic. In early March, the team tracked a sophisticated recon effort as a threat actor abused e-commerce user-experience business logic to attempt to commit fraudulent purchases on stolen credit cards through automated account creation. Finally, the team observed a notable pop in traffic from an organization Emeigh Investments LLC which appears to be the holding company for a set of scraping & hosting services.
Uptick in Traffic from China
To ensure their bot achieves its end goal, threat actors will typically make every effort to hide their bot traffic within legitimate end user requests. This means following the same buying process a user follows, funneling traffic through local, residential proxies, and so on. The Cequence CQ Prime Threat Research Team observed a steady uptick in traffic from China beginning in February and spiking at a 200% increase in early March. This pattern deviates from the hide in plain sight approach that bots typically follow, given the target customers were in the US and EMEA and did not transact much business with customers in China.
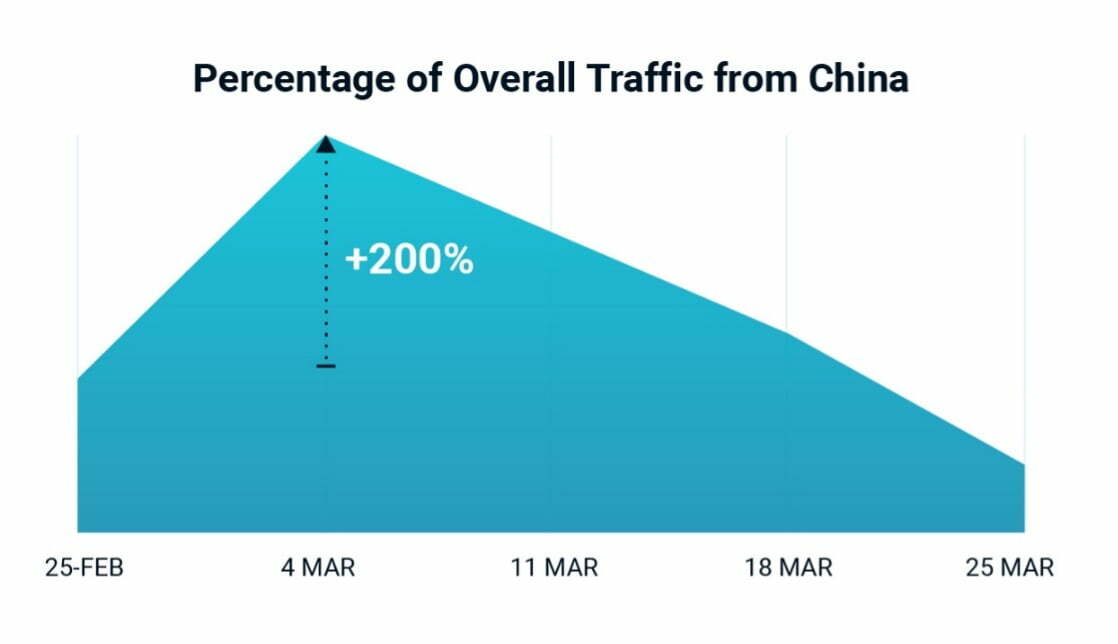 Image 1: Uptick in malicious traffic from China as a percentage of overall.
Image 1: Uptick in malicious traffic from China as a percentage of overall.
While the overall volume of traffic from China is small, the uptick shown in image 1 is worth noting as it was observed across multiple customers in the US and EMEA.
- Account takeover was the most common attack type observed within the traffic from China with roughly 600K ATO attempts emanating from China detected and blocked while protecting 265K unique user accounts, resulting in a customer savings of $1.46M, based on the Juniper Research report that states ATOs cost an average of $290 per account.
- One of the patterns observed saw the threat actor rotate across multiple login API endpoints on 15 minute intervals with traffic bursts of up to 80% of the normal traffic volume of a given API. At least 10 different Behavioral Fingerprints were triggered, representing signs of automation such as the same userID on many different IP addresses, further confirming that this was an automated.
- Attack traffic was distributed across 400K IPs from 168 organizations with most common being China Telecom, 189.cn, China Telecom Jiangx, CHINATELECOM Xinjiang Wulumuqi MAN network and Chunghwa Telecom.
Sophisticated Reconnaissance
In an example of how dedicated threat actors are, the Cequence CQ Prime Threat Research team observed an attacker methodically map a customer’s entire site to learn the precise workflow and uncover any potential weaknesses. The threat actor created an account then tested how it could be abused with an end goal of gift card fraud or fradulent purchases using stolen credit cards. The weaknesses the attacker exploited are common in online retail environments where important decisions regarding the tradeoff between shopper experience and security must be made. In this case, the attacker found that the account creation workflow would immediately authenticate, and authorize a user to do subsequent privileged actions like edit/change payment details. From an end-user perspective, this flow makes sense to reduce user friction for recently created accounts. However attackers realized they could use bots to abuse this business logic, and create accounts en masse. The attacker was committed to remaining undetected as they distributed more than 1.5M requests across 132,660 IPs from 20+ organizations. Ultimately, the attack triggered hundreds of Behavioral Fingerprints representing actions including use of outdated browsers, malicious traffic source, and rapid user-agent rotation.
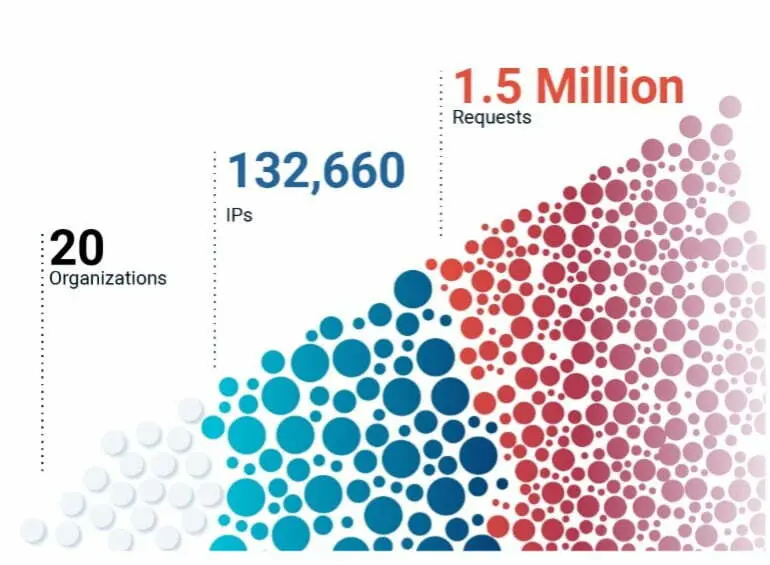
Image 2: Malicious traffic observed during a sophisticated reconnaissance effort.
New Bulletproof Proxy Provider?
The threat team observed an ATO attack that encompassed 8.7M requests distributed across 1.1M residential proxies from 20 or so organizations. The threat actor rapidly retooled, triggering hundreds of Behavioral Fingerprints with actions that include many user names logging in from same IP, too many account verification attempts from same IP and same userid accessed over multiple IP addresses. One of the interesting characteristics of this attack is the emergence of a new organization as the source for malicious traffic. While only a small percentage of the traffic, the threat team observed a spike in use from Emeigh Investments LLC, a holding company for Sprious (https://sprious.com/), which names Blazing SEO (https://blazingseollc.com/), Scraping Robot, (https://scrapingrobot.com/) and WP Super Host (https://wpsuperhost.com/) as partner companies. The likely source of the IP addresses is Blazing SEO, given that their product line includes both data center and residential proxy offerings. The spike is of interest because of the somewhat sudden appearance as a top source of malicious traffic. As noted in the chart, they were more heavily used then Cogent and ServerMania – two sources that are constantly at the top of the list of organizations whose infrastructure is used in automated attacks against our customers.
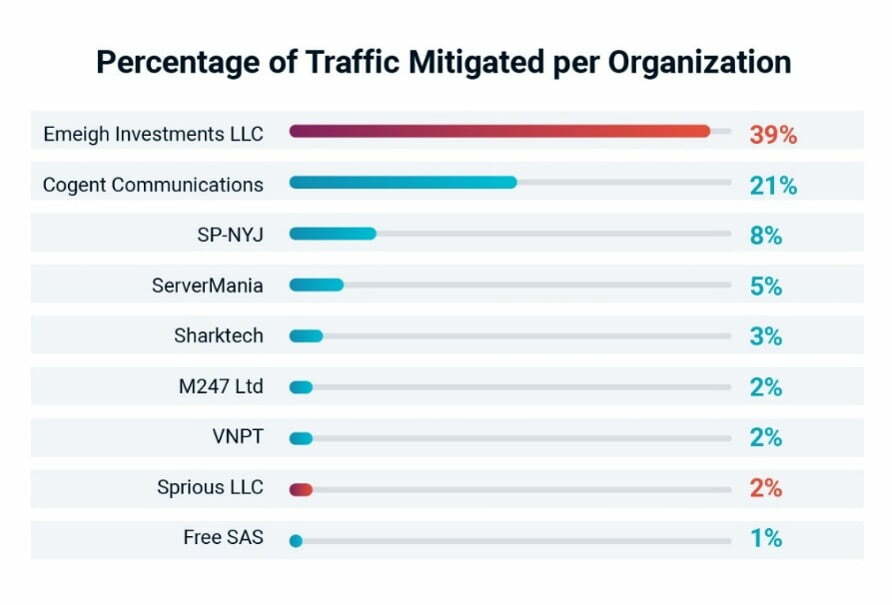
Image 3: A potentially new Bulletproof Proxy vendor appeared in Q1 2022.
As documented in our ongoing research on Bulletproof Proxies, these vendors walk a thin line between legitimate and malicious use. Their services can certainly be of benefit to web masters and marketing teams who wish to test the performance of their web site. However, their tools are commonly used as integral elements of an automated attack. For a very low cost, a bot manager can subscribe to their services and easily distribute their attack across many, many IP addresses from a range of cities, states and countries. All with the end goal of masking identity and location while achieving scale.
The post State of API Security Activity appeared first on Cequence.
*** This is a Security Bloggers Network syndicated blog from Cequence authored by The CQ Prime Team. Read the original post at: https://www.cequence.ai/blog/state-of-api-security-activity/



