How to Disrupt the Web Attack Lifecycle

The cyberthreat landscape has changed. Web attacks that were once separate and distinct have come together in a continuous and integrated cycle of cybercrime. One kind of attack fuels another, propagating and prolonging an attack lifecycle that hits consumers everywhere along their digital journey — and web apps are a prime target.
So, let’s start by looking at what’s driving the changes.
- Attacker Profiles – Cybercriminals aren’t just computer science students and amateur botters looking to make some extra cash. Cybercrime is an industry made up of savvy professionals that launch sophisticated attacks that can have a material negative impact on your business.
- Sophistication – Advances in technology have allowed attacks to become increasingly advanced: bots that rotate IP addresses, solve CAPTCHAs and mimic human behavior; malicious code that loads dynamically to avoid static scanners; and targeted custom malware.
- Location – Of course attacks still take place on login and checkout pages, but they also occur before and after those checkpoints on nearly all of your website pages. Some attacks even happen on users’ browsers beyond the purview of typical web controls like web application firewalls (WAFs).
- Value – Today’s online accounts hold more personal data than ever before, including stored credit card numbers, gift card balances and airline miles and personally identifiable information (PII). This means cybercriminals can reap even bigger rewards from a successful cyberattack.
3 Stages of Cybercrime
Modern cyberattacks are continuous and cyclical. One attack feeds another, such as a PII breach on Website A fueling a downstream account takeover attack on Website B. Because of this, a new understanding of the web attack lifecycle is required.
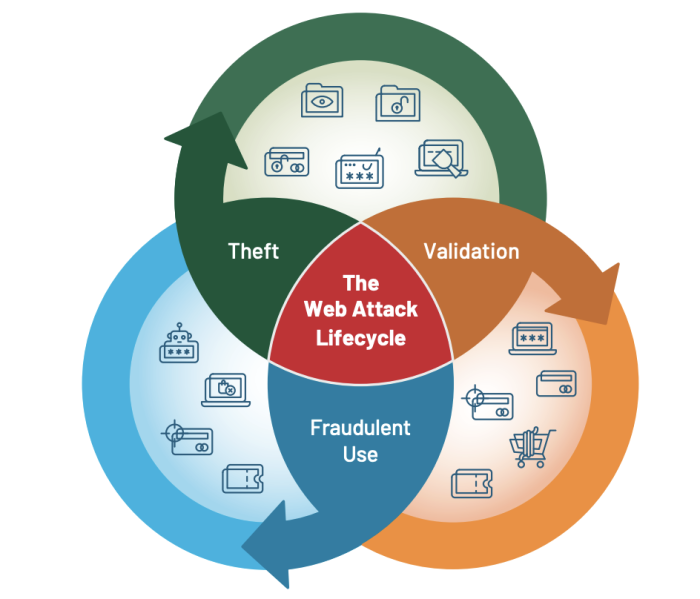
We break down the web attack lifecycle into three stages: theft, validation and fraudulent use.
- Theft: Attackers steal credentials, payment data and other sensitive information via PII harvesting, (Read more...)
*** This is a Security Bloggers Network syndicated blog from PerimeterX Blog authored by PerimeterX Blog. Read the original post at: https://www.perimeterx.com/resources/blog/2022/how-to-disrupt-the-web-attack-lifecycle/




