Understanding the Coinbase API Vulnerability
This past Saturday, the Twitter account “Tree_Of_Alpha” posted a very interesting tweet regarding a security flaw he “accidentally” found in Coinbase. Tweets like this one have long become very popular, and with so many vulnerability discoveries shared, this post could have easily been missed. However, this case was indeed special.
First, some background on Coinbase. If you’ve followed cryptocurrency or crypto trading at all, Coinbase is a company you know. For those of you unfamiliar with it, we’ll briefly explain what Coinbase is. Coinbase is an online crypto exchange system. In essence, Coinbase provides its users with a platform to conduct online trading of cryptocurrency such as Bitcoin, Bitcoin Cash, Ethereum, Litecoin, and many others. The services Coinbase provides are extensive, ranging from statistics and analytical data of crypto coin values to the ability to buy and sell any supported cryptocurrency.
Coinbase was founded in 2012, and with the extremely rising popularity of the crypto market, it became one of the largest online crypto exchange platforms. It supports more than 73 million registered users and more than $300 Billion in quarterly trades.
Given the critical nature of the transactions on the Coinbase platform, even a minor security issue could have catastrophic impact, which is why Coinbase invests a lot of effort and resources into securing its platform end to end.
And this is what made the Saturday night tweet very special indeed.
In his tweet, “Tree_Of_Alpha” noted he was inspecting a relatively new feature provided by Coinbase called “Advanced Trading.” As part of this new Coinbase feature, users are able to place orders for selling one type of crypto currency and use the funds to buy another.
Under the hood, such a request uses a standard RESTful API request similar to this one:

As the above capture shows, this request contains several key parameters, including:
- Product: the product being traded – in this case, Ethereum to Euro
- Source Account: the source account funds should be sold from
- Target Account: the destination account to transfer the converted currency to
To his (and everyone else’s) great surprise, he was able to conduct a few basic tests and learn that while those parameters exist in every request, they are lacking proper basic validation checks.
More specifically, he could manually change the `product` parameter, but the Coinbase back-end system did not properly validate that the user actually has the wallets defined in the product. As a result, anyone could initiate a transfer of funds from a non-existing wallet – effectively, your crypto-wallet does not belong to you!
To validate his find, while minimizing the risk substantial damage to the ecosystem or any Coinbase users, he sent the same request while manually changing the product from “ETH-EUR” to “BTC-USD,” meaning an order to sell and convert Bitcoin to US dollars – but without actually owning a Bitcoin wallet. Surprisingly, the Coinbase platform correctly processed the request, and the funds were transferred from an “unknown” Bitcoin account into a valid USD wallet, as the following tweet shows.
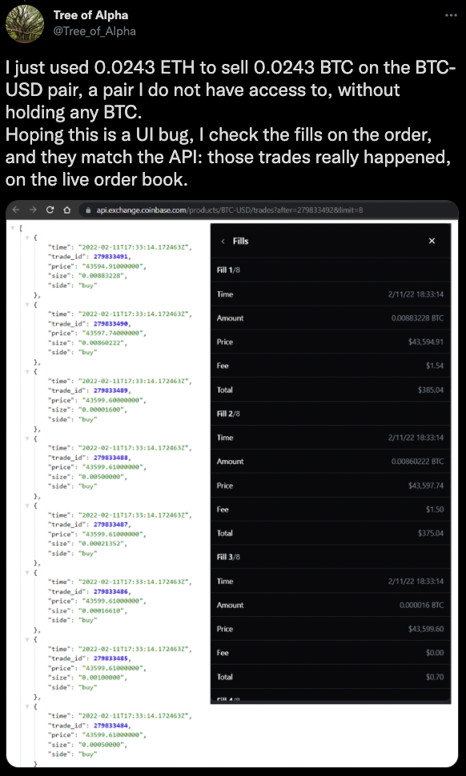
This API security gap, in malicious hands, would have catastrophic consequences – it could put millions of users, and perhaps the entire crypto currency ecosystem, at very high risk. And it could easily have put Coinbase out of business.
Luckily, “Tree_Of_Alpha” responsibly disclosed the vulnerability to Coinbase, whose team very quickly acted to fix the issue. “Tree_Of_Alpha” earned an unprecedented $250,000 bug bounty award for the finding, further evidence of the magnitude and risk of this API vulnerability. Additional investigation and a public report by Coinbase confirmed the issue, and the company also shared it had “conclusively determined that it has never been maliciously exploited.”
As potentially catastrophic as this vulnerability might be, the whole industry must recognize such a flaw is by no means exclusive to Coinbase. At Salt Labs, we deal with hundreds of similar API issues on a monthly basis – we see this type of issue on a regular basis.
How could this type of vulnerability, which could have decimated Coinbase, get into production APIs? The cause rests in part on rapid development lifecycles. In today’s era of cloud computing and advanced CI/CD methods, it is easier than ever for any online service to publish new, highly durable and scalable features within a matter of minutes or hours. The push to innovate fast sometimes comes at the expense of security. As computing history – and human nature – teaches us, new functionalities and features will always be more lucrative and important to any service. Complicating the matter, modern API design can sometimes be cumbersome and complex.
So what does this mean for all these organizations looking to develop fast? Realize that bad actors are drawn to looking for API vulnerabilities just as much as the whitehat hackers – look at how profitable it can be! And few organizations have deployed effective API security solutions to date. Just as with the Experian and Peloton vulnerability discoveries last year, any organization can be susceptible to an API logic flaw. The Coinbase incident is simply the latest red warning flag for online service and users alike to ensure they’re making API security a top priority in protecting their online services.
*** This is a Security Bloggers Network syndicated blog from Salt Security blog authored by Salt Labs. Read the original post at: https://salt.security/blog/understanding-the-coinbase-api-vulnerability





